Prevent Members from Domain Users Group to Logon by default to any Domain joined Computers
In this post I want to show how you can prevent that domain users can logon by default to each domain joined computer in your Active Directory network.
In Active Directory when you create a new user, by default this user is a member in the Domain Users group as shown below.
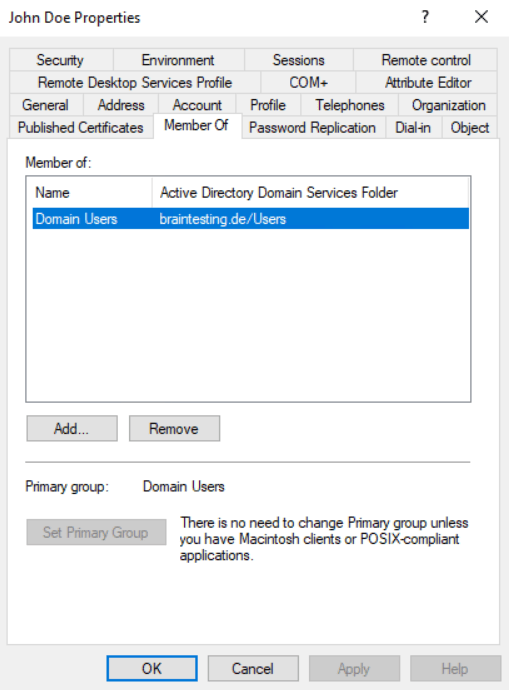
The AD group Domain Users is by default a member in the local Users group on domain joined windows computers as shown below. This is also true for Windows Server except if it is a domain controller.
Domain Controllers don’t have the Local Users and Groups databases once they’re promoted to a Domain Controller.
Therefore AD users get permission to logon to all domain joined computers. Further the AD group Domain Administrators is also by default added as member of the local Administrators group.
Besides the Domain Users group which is added to the local Users group after joining the computer to the domain, two other local groups named Authenticated Users and Interactive are still by default member in the local Users group, you will see them in the figure below. They will be on standalone and domain joined computers member of the local Users group.
So finally if just one of these three groups are member in the local Users group, a domain user is able to logon to a domain joined computer.
The reason for why just one of these three groups must be member in the local Users group is obvious when you read what the groups are for. I think the Domain users group is self-explaining.
The Authenticated users group –> Any user who accesses the system through a sign-in process has the Authenticated Users identity. The sign-in process here is the logon against a domain controller and therefore the user can logon to any domain joined computer after it authenticated successful against the domain controller.
The Interactive group –> Any user who is logged on to the local system has the Interactive identity.
Any user that has access to a desktop is considered an Interactive user.
Any user that logs on against a domain is considered an Authenticated user.
Special identities
https://docs.microsoft.com/en-us/windows/security/identity-protection/access-control/special-identities
Domain joined Windows 10 computer
The Autenticated Users and Interactive group are already member of the local Users group before domain join.
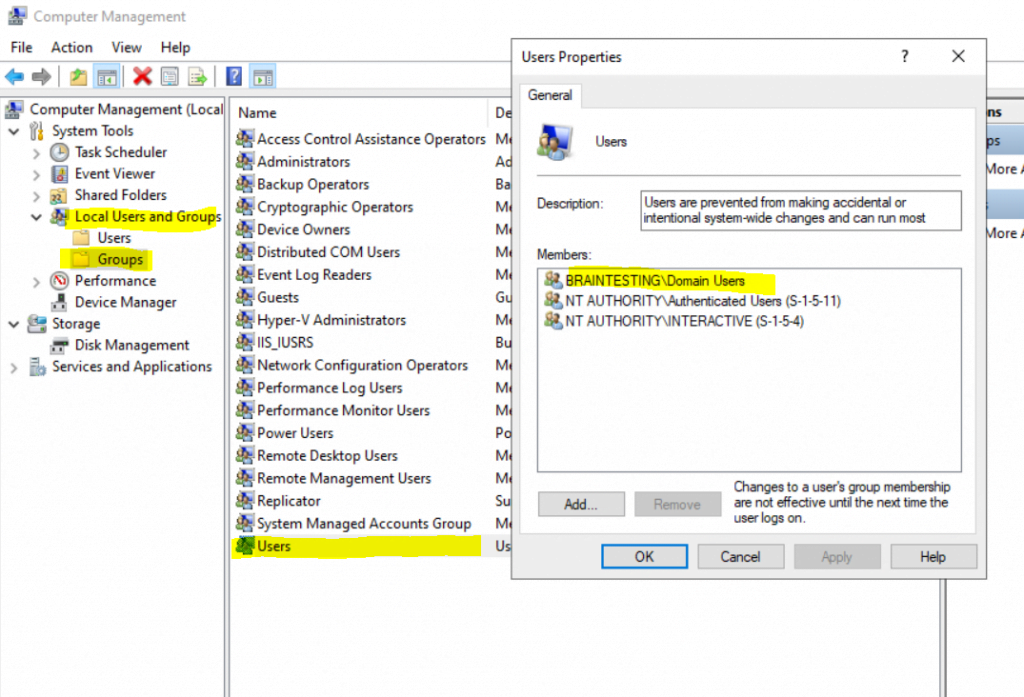
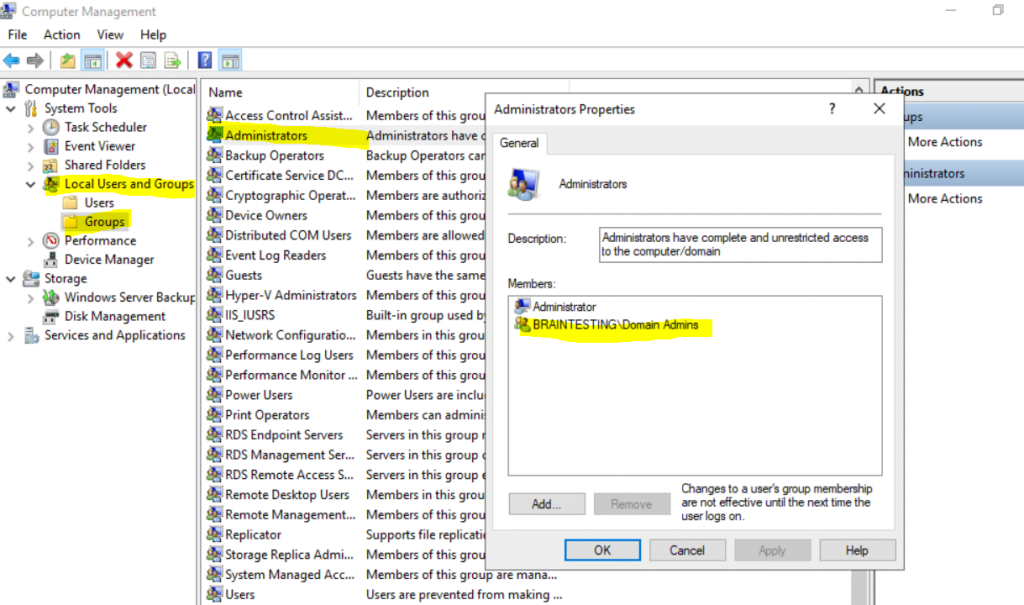
Note! You can now think I will just remove these three groups from the local Users group and adding the accounts I want to have access to directly in the local Users group.
Removing these groups will have adverse impacts for local users, shared printers, network shares, etc., so don’t remove them!
In order to restrict this behavior we can take action on either the user account or the computer account configuration.
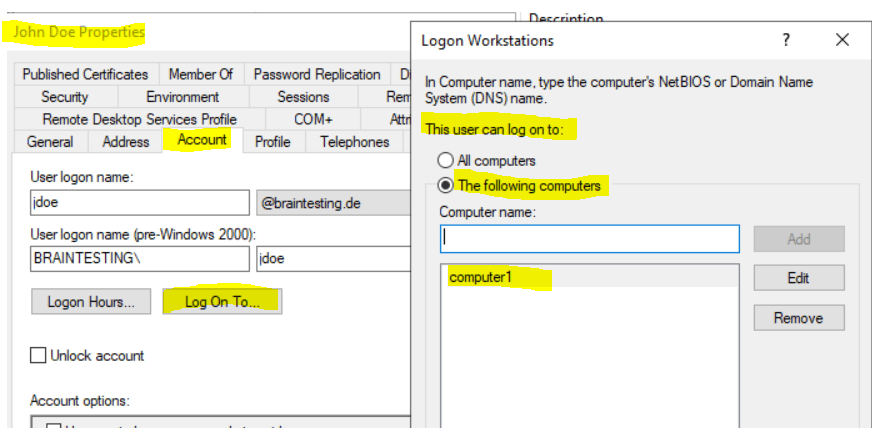
The simplest way to restrict a specific user to allow logon to only one or a bunch of computers instead of all domain joined computers, is to specify them at his AD account as shown below.
By default this is set to All computers, from now on the user John Doe can only logon to a domain joined computer named computer1.
You can also use the Active Directory Module for Windows PowerShell to manage the above allowed computer where a user can logon to.
> Get-ADUser jdoe -Properties LogonWorkstations | fl Name, LogonWorkstations
> Set-ADUser jdoe -LogonWorkstations “computer1, computer2,computer3”
In order to add a computer you can use the following commands
> $computers = (Get-ADUser jdoe -Properties LogonWorkstations).LogonWorkstations
> $computers += “,computer4”
> Set-ADUser jdoe -LogonWorkstations $computers
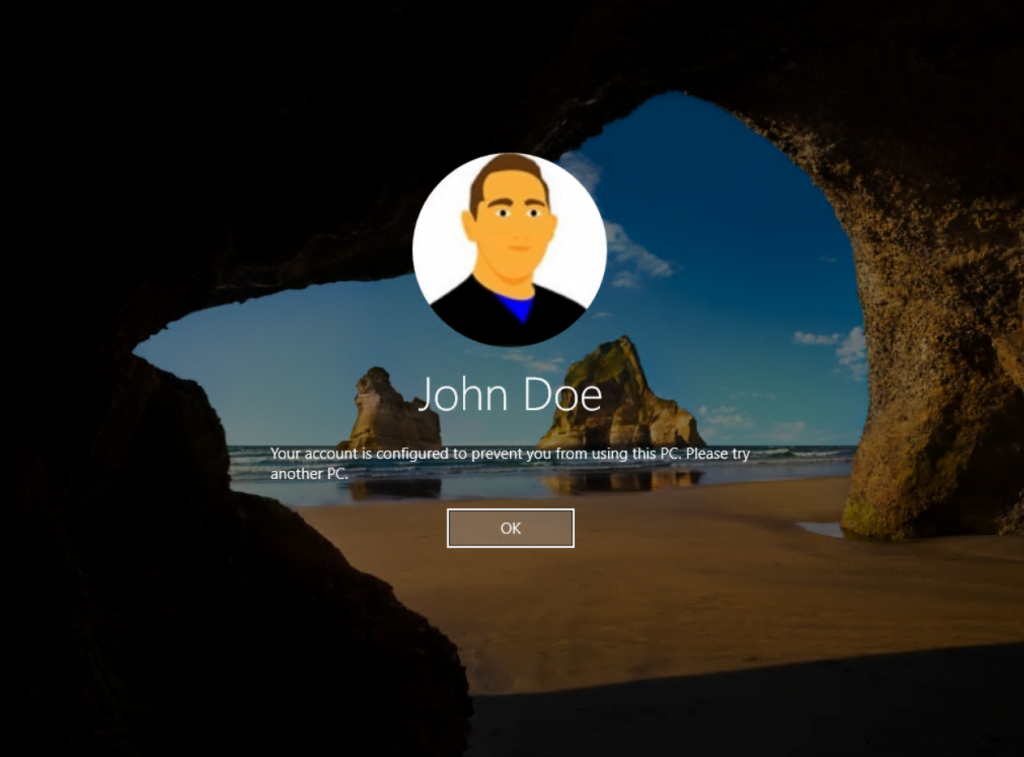
If the user tries to logon to a computer not listed above, the logon will be refused with the following message.
Your account is configured to prevent you from using this PC. Please try another PC.
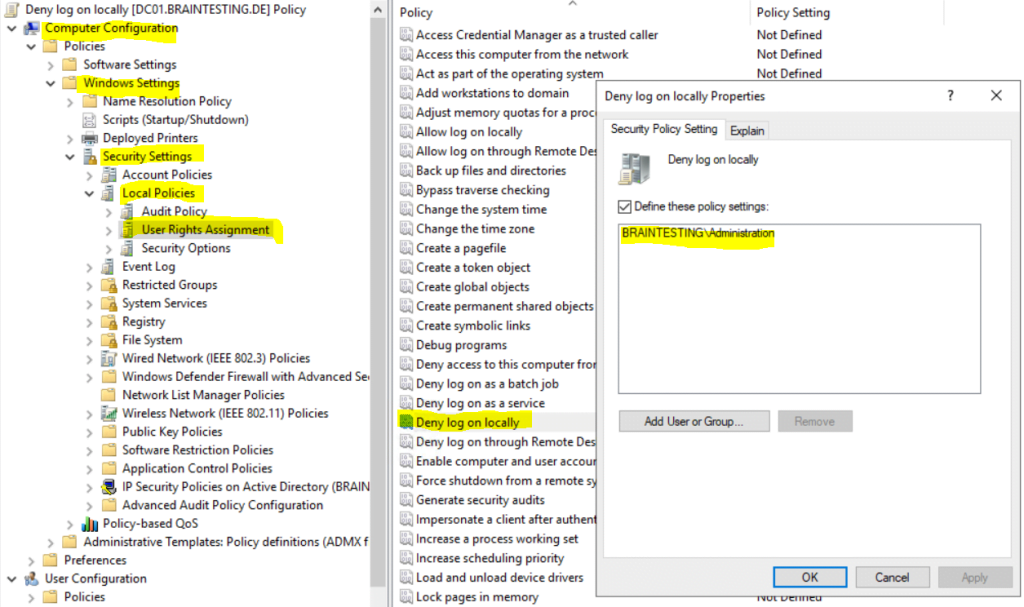
You can also use a Group Policy to prevent users from logon to a domain joined computer by default. Below I configured the Deny log on locally policy. All members in the AD group Administration will be denied from logon to domain joined computers where this policy is linked to. The Policy is linked to the OU of the computers I want to restrict access to.
Computer Configuration –> Policies –> Windows Settings –> Security Settings –> Local Policies –> User Right Assignment –> Deny log on locally
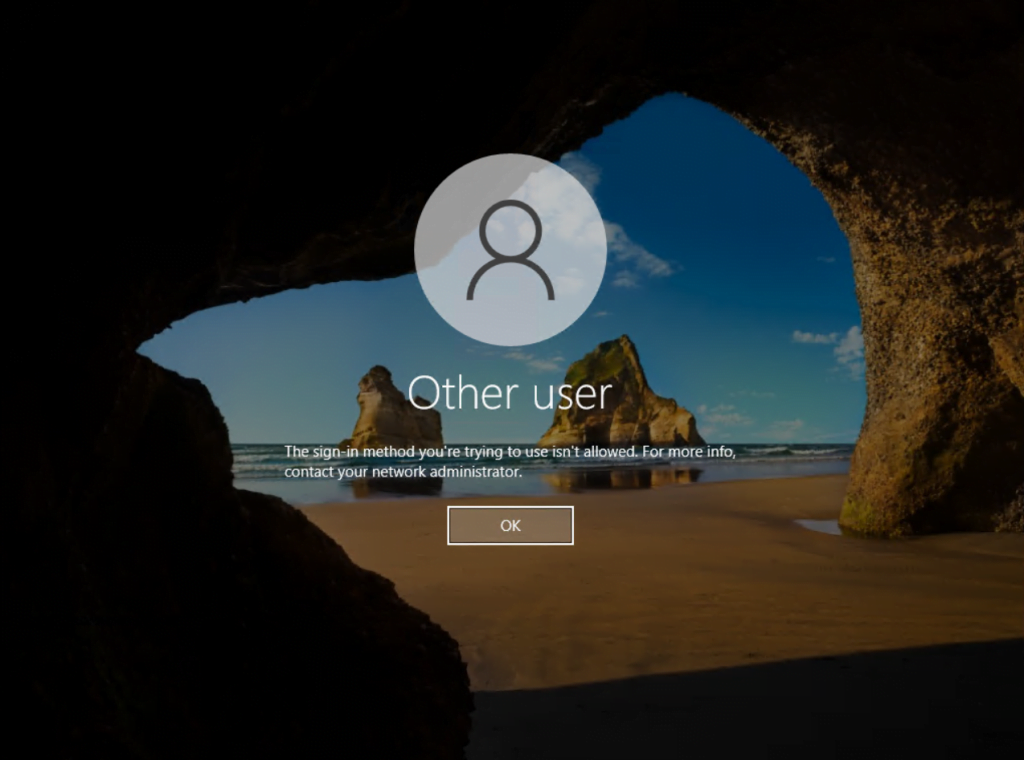
If a user from the AD group Administration tries to logon to a computer where the policy is linked to, it will refuse the logon with the following message.
The sign-in method you’re trying to use isn’t allowed. For more info, contact your network administrator.
If you also configure the Allow log on locally and the user resides in both policies, the Deny log on locally wins.
Links
Special Identities
https://docs.microsoft.com/en-us/windows/security/identity-protection/access-control/special-identities
Tags In
Follow me on LinkedIn


