Set up DMARC (verification) for Postfix on Ubuntu
Last week I wrote a post about how to set up SPF and DKIM for Postfix on Ubuntu, today I want to show how to set up DMARC for Postfix on Ubuntu.
DMARC extends two existing email authentication mechanisms, Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM).
Therefore if not already done, in order to use DMARC verification on postfix, you first need to set up SPF and DKIM on your postfix server, because DMARC depends on the SPF- and DKIM verification results to take actions regarding —> reject, quarantine or allow the delivery of the email message to the recipients inbox.
Install OpenDMARC
OpenDMARC is an open source implementation of the Domain-based Message Authentication, Reporting and Conformance (DMARC) specification.
For how to set up DMARC verification for Postfix on Ubuntu, all credit goes again to Xiao Guoan from linuxbabe.com, which post below I used myself to set up OpenDMARC on my Ubuntu server.
Set Up OpenDMARC with Postfix on Ubuntu to Block Spam/Email Spoofing
https://www.linuxbabe.com/mail-server/opendmarc-postfix-ubuntu
$ sudo apt install opendmarc
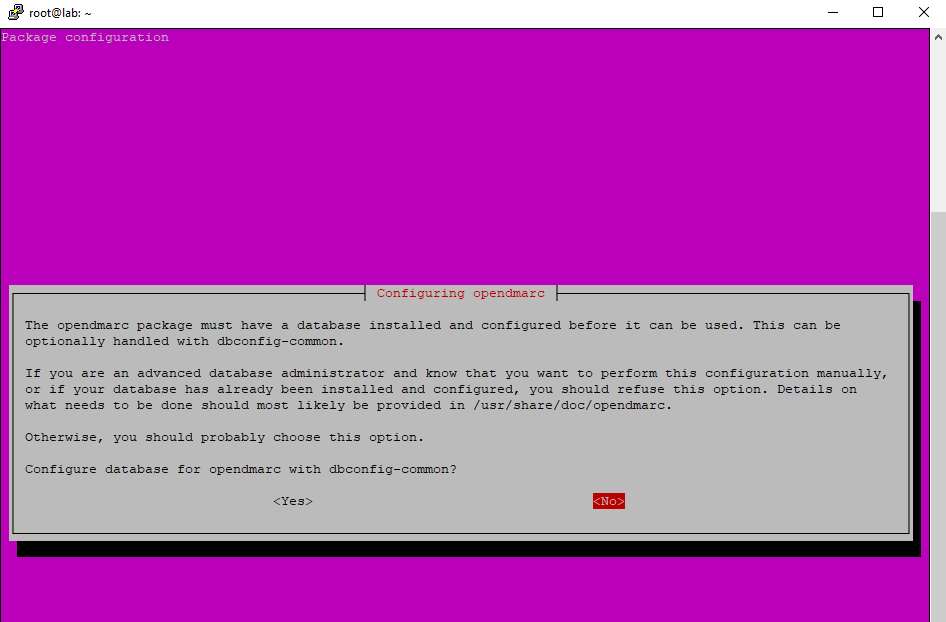
If you were asked to configure a database for OpenDMARC with dbconfig-common, you can choose No. The database is just used in case you want to generate DMARC reports for other mailbox providers.
To enable auto-start at boot we enter the following command.
$ sudo systemctl enable opendmarc
Now we need to edit the main configuration file /etc/opendmarc.conf
$ sudo nano /etc/opendmarc.conf
Find the following line
# AuthservID name
and replace it with
AuthservID OpenDMARC
Sets the authserv-id to use when generating the Authentication-Results: header field after verifying a message. The default is to use the name of the MTA processing the message. If the string HOSTNAME is provided, the name of the host running the filter (as returned by the gethostname(3) function) will be used.
So if checking the header and logs, you will see immediately the verification is done by the OpenDMARC daemon.
Next add the following line. Replace the hostname with your real Postfix FQDN. This tells OpenDMARC to trust authentication result with mail.yourdomain.com in the ID. This is needed when you have OpenDKIM running to do DKIM verification.
TrustedAuthservIDs mail.yourdomain.com
If the Postfix FQDN isn’t included in the TrustedAuthservIDs, or you have a typo in the FQDN, then OpenDMARC will ignore the Authentication-Results header generated by OpenDKIM, and you will find the following error message in the mail log /var/log/mail.log
opendmarc[1133]: A436A205C9 ignoring Authentication-Results at 1 from mail.yourdomain.com
Find the line
# RejectFailures false
By default, OpenDMARC won’t reject emails that fail DMARC check, even if the domain’s policy is set to p=reject. If you prefer to reject emails that fail DMARC check when the domain’s policy is set to p=reject, then uncomment this line and change false to true.
RejectFailures true
You may want OpenDMARC to ignore SMTP clients that are successfully authenticated via SMTP AUTH. For example desktop/mobile mail clients that submit outgoing emails over port 587. In this case, add the following line at the end of this file.
IgnoreAuthenticatedClients true
Add the following line at the end of this file.
RequiredHeaders true
This will reject emails that don’t conform to email header standards as described in RFC5322. For example, if an incoming email doesn’t have From: header or date: header, it will be rejected. A From: field from which no domain name could be extracted will also be rejected.
It’s recommended to also add the following line at the end of this file. This will make OpenDMARC perform a fallback SPF check itself when it can find no SPF results in the message header.
SPFSelfValidate true
OpenDMARC is implemented as a milter (mail filter). Postfix can talk to milter applications via Unix socket. The default socket file used by OpenDMARC is /var/run/opendmarc/opendmarc.sock. But the Postfix SMTP daemon shipped with Ubuntu runs in chroot jail, which means the SMTP daemon resolves all filenames relative to the Postfix queue directory (/var/spool/postfix). So we need to change the socket file used by OpenDMARC.
Find the following line.
Socket local:/var/run/opendmarc/opendmarc.sock
and replace it with
Socket local:/var/spool/postfix/opendmarc/opendmarc.sock
Create a directory to hold the OpenDMARC socket file and change the ownership so that opendmarc user and opendmarc group can access it.
$ sudo mkdir -p /var/spool/postfix/opendmarc
$ sudo chown opendmarc:opendmarc /var/spool/postfix/opendmarc -R
Change permission to 750 to restrict access, so users not in group opendmarc can’t access this directory.
sudo chmod 750 /var/spool/postfix/opendmarc/ -R
Add user postfix to group opendmarc.
$ sudo adduser postfix opendmarc
Finally restart OpenDMARC
$ sudo systemctl restart opendmarc
Configure Postfix for OpenDMARC
Edit the main configuration file /etc/main.cf
$ sudo nano /etc/main.cf
As we already configured OpenDKIM in the last post I mentioned, you should still have the following lines below.
milter_default_action = accept
milter_protocol = 6
smtpd_milters = local:opendkim/opendkim.sock
non_smtpd_milters = $smtpd_milters
Now you just need to add the OpenDMARC socket file so that Postfix can talk to OpenDMARC. (Make sure it’s after the OpenDKIM socket.)
milter_default_action = accept
milter_protocol = 6
smtpd_milters = local:opendkim/opendkim.sock, local:opendmarc/opendmarc.sock
non_smtpd_milters = $smtpd_milters
Restart Postfix
$ sudo systemctl restart postfix
Testing OpenDMARC Verification
To test if OpenDMARC works on your postfix server, you can send an email from another email account and for which sending domain SPF and DKIM is configured to an account on your postfix server.
If it works correctly you should see the DMARC verification results in the E-Mail header like below
Authentication-Results: OpenDMARC; dmarc=pass (p=reject dis=none) header.from=braincourt.com
Further in the postfix server logs under /var/log/mail.log you should see something like below
opendmarc[25606]: 8C7621800DC: braincourt.com pass
Links
Set Up OpenDMARC with Postfix on Ubuntu to Block Spam/Email Spoofing
https://www.linuxbabe.com/mail-server/opendmarc-postfix-ubuntu
Hands-on: implementing SPF, DKIM and DMARC in Postfix
https://www.sidn.nl/en/news-and-blogs/hands-on-implementing-spf-dkim-and-dmarc-in-postfix
Related Posts
Follow me on LinkedIn


