Set up Microsoft Defender for Endpoint
In this post I will show what Microsoft Defender for Endpoint is, how we can integrate it with Microsoft Intune as a Mobile Threat Defense solution and how we can onboard devices either from Intune or directly to Microsoft Defender for Endpoint
When you integrate Intune with Microsoft Defender for Endpoint, you can take advantage of Defender for Endpoint’s threat and vulnerability management and use Intune to remediate endpoint weakness identified by Defender’s vulnerability management capability. This integration brings a risk-based approach to the discovery and prioritization of vulnerabilities that can improve remediation response time across your environment.
Source: https://learn.microsoft.com/en-us/mem/intune/protect/atp-manage-vulnerabilities
Connecting Microsoft Intune and Microsoft Defender for Endpoint for example allows you to use Microsoft Defender for Endpoint’s dynamically calculated machine risk scores in Intune compliance evaluation and Microsoft Entra conditional access enforcement.
Introduction
First of all Microsoft Defender for Endpoint is an enterprise endpoint security platform included within Microsoft Defender XDR (formerly known as Microsoft 365 Defender).
Microsoft Defender XDR is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.
Microsoft Defender XDR coordinates with several other security platforms and solutions like Microsoft Defender for Office 365, Microsoft Defender for Identity, Microsoft Defender Vulnerability Management, and more …
With the integrated Microsoft Defender XDR solution, security professionals can stitch together the threat signals that each of these products receive and determine the full scope and impact of the threat; how it entered the environment, what it’s affected, and how it’s currently impacting the organization. Microsoft Defender XDR takes automatic action to prevent or stop the attack and self-heal affected mailboxes, endpoints, and user identities.
Source: https://learn.microsoft.com/en-us/microsoft-365/security/defender/microsoft-365-defender
Defender for Endpoint uses the following combination of technology built into Windows 10 (and later) and Microsoft’s robust cloud service:
- Endpoint behavioral sensors: Embedded in Windows 10 (and later), these sensors collect and process behavioral signals from the operating system and send this sensor data to your private, isolated, cloud instance of Microsoft Defender for Endpoint.
- Cloud security analytics: Leveraging big-data, device learning, and unique Microsoft optics across the Windows ecosystem, enterprise cloud products (such as Office 365), and online assets, behavioral signals are translated into insights, detections, and recommended responses to advanced threats.
- Threat intelligence: Generated by Microsoft hunters, security teams, and augmented by threat intelligence provided by partners, threat intelligence enables Defender for Endpoint to identify attacker tools, techniques, and procedures, and generate alerts when they are observed in collected sensor data.
Licensing
Microsoft Defender for Endpoint is available in two plans, Defender for Endpoint Plan 1 and Plan 2. A new Microsoft Defender Vulnerability Management add-on is now available for Plan 2.
For more information on the features and capabilities included in each plan, including the new Defender Vulnerability Management add-on, see Compare Microsoft Defender for Endpoint plans.
Enable Microsoft Defender for Endpoint in Intune
The first step you should take is to set up the service-to-service connection between Intune and Microsoft Defender for Endpoint. Set up requires administrative access to both the Microsoft Defender Security Center, and to Intune.
You only need to enable Microsoft Defender for Endpoint a single time per tenant.
Connecting Microsoft Intune and Microsoft Defender for Endpoint allows you to use Microsoft Defender for Endpoint’s dynamically calculated machine risk scores in Intune compliance evaluation and Microsoft Entra conditional access enforcement.
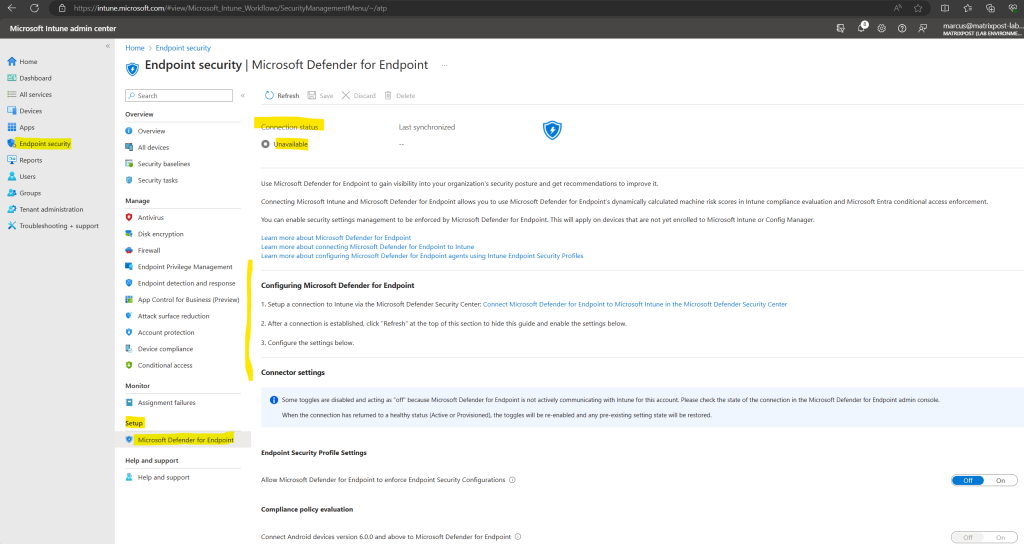
To setup the connection between Intune and Microsoft Defender for Endpoint we have to go to the Microsoft Defender portal.
In the Microsoft Defender portal select Settings > Endpoints
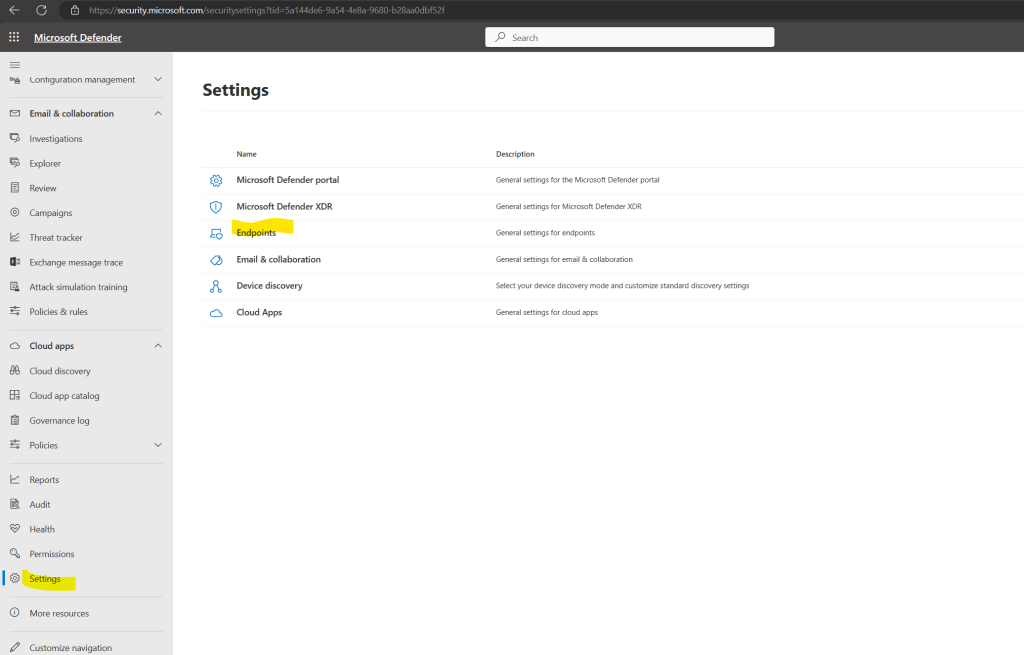
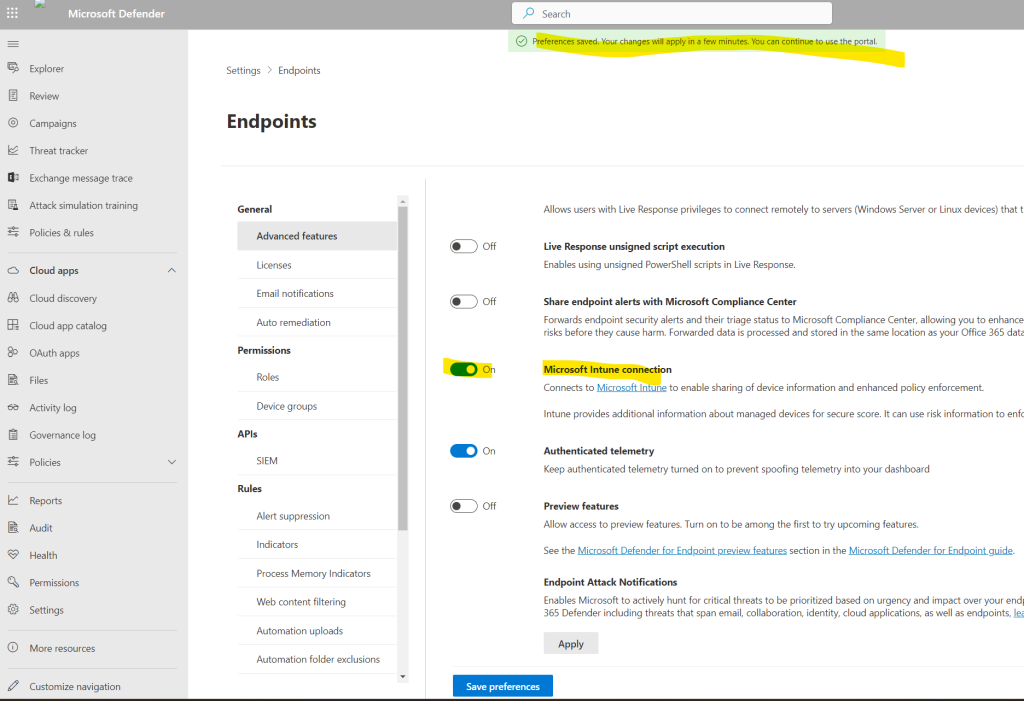
Within the Endpoints Settings section, select Advanced features and for Microsoft Intune connection, choose On.
Finally click on Save preferences.
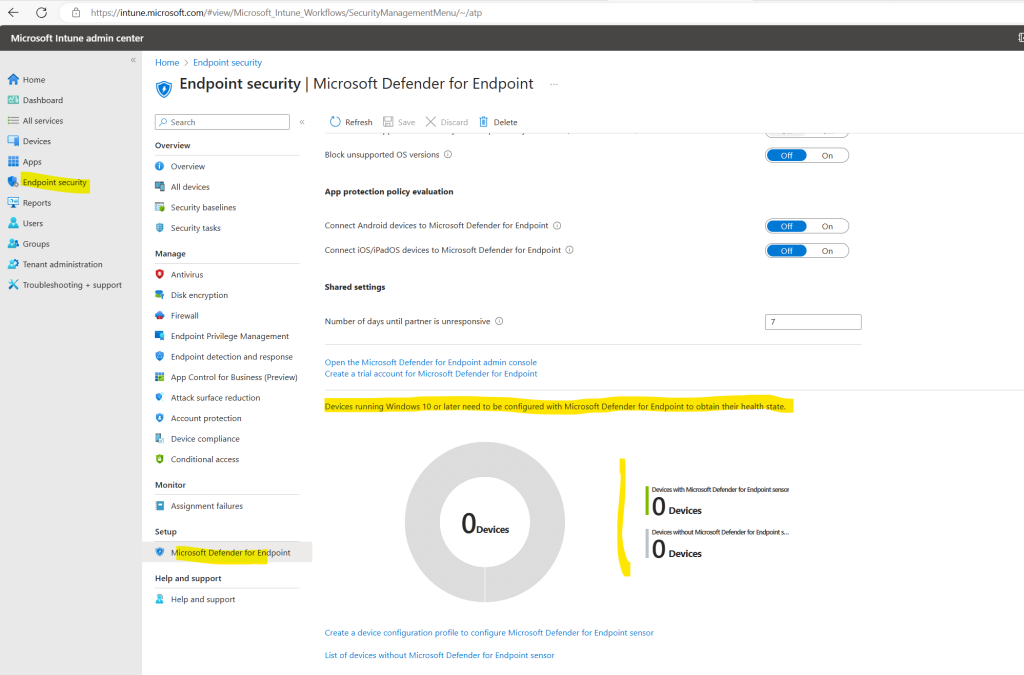
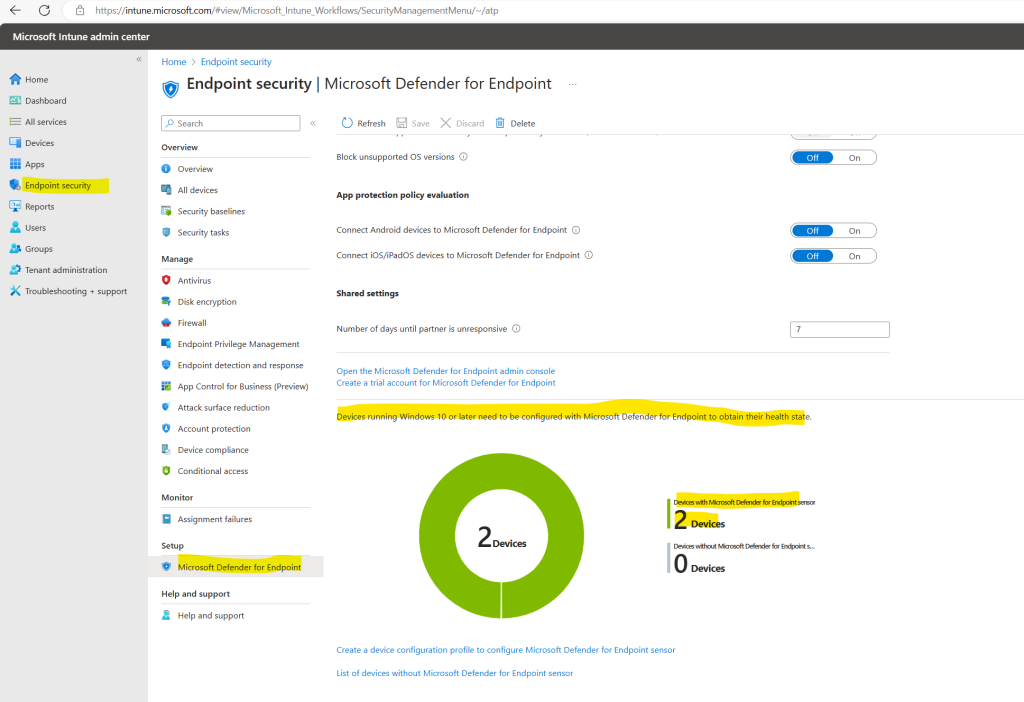
Once the connection is established, the services are expected to sync with each other at least once every 24 hours. The number of days without sync until the connection is considered unresponsive is configurable in the Microsoft Intune admin center. Select Endpoint security > Microsoft Defender for Endpoint > Number of days until partner is unresponsive
In the Microsoft Intune admin center under Endpoint security -> Microsoft Defender for Endpoint we can now see that the connection with Microsoft Defender for Endpoint so far is available but not already enabled.
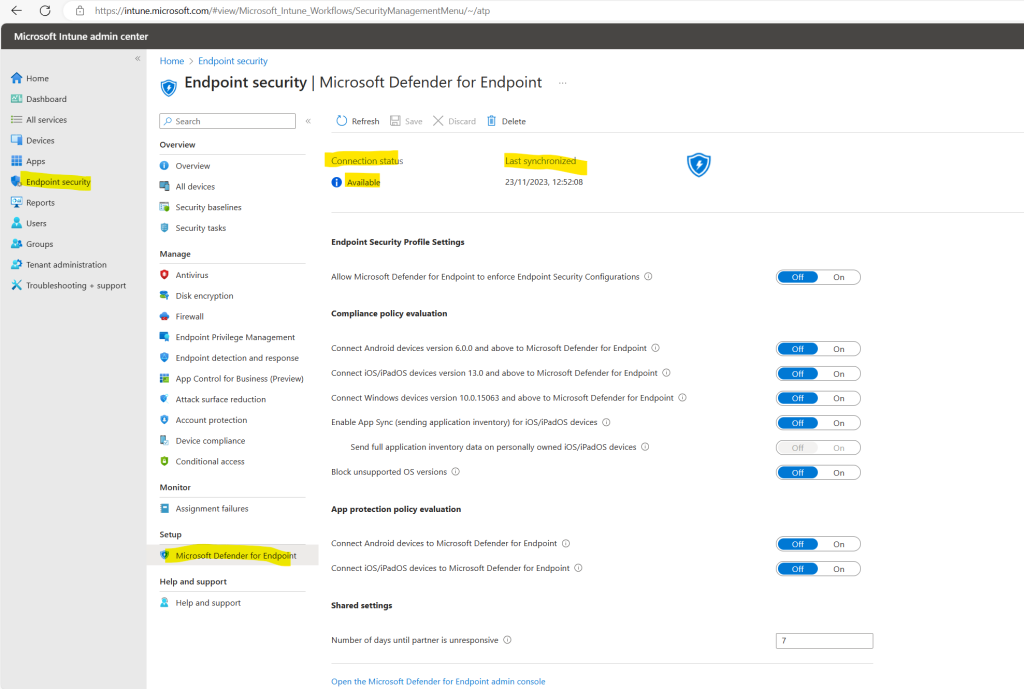
To use Defender for Endpoint with compliance policies, configure the following Policy Settings for the platforms you support:
- Set Connect Android devices to Microsoft Defender for Endpoint to On
- Set Connect iOS devices to Microsoft Defender for Endpoint to On
- Set Connect Windows devices to Microsoft Defender for Endpoint to On
When these configurations are On, applicable devices that you manage with Intune, and devices you enroll in the future, are connected to Microsoft Defender for Endpoint for compliance.
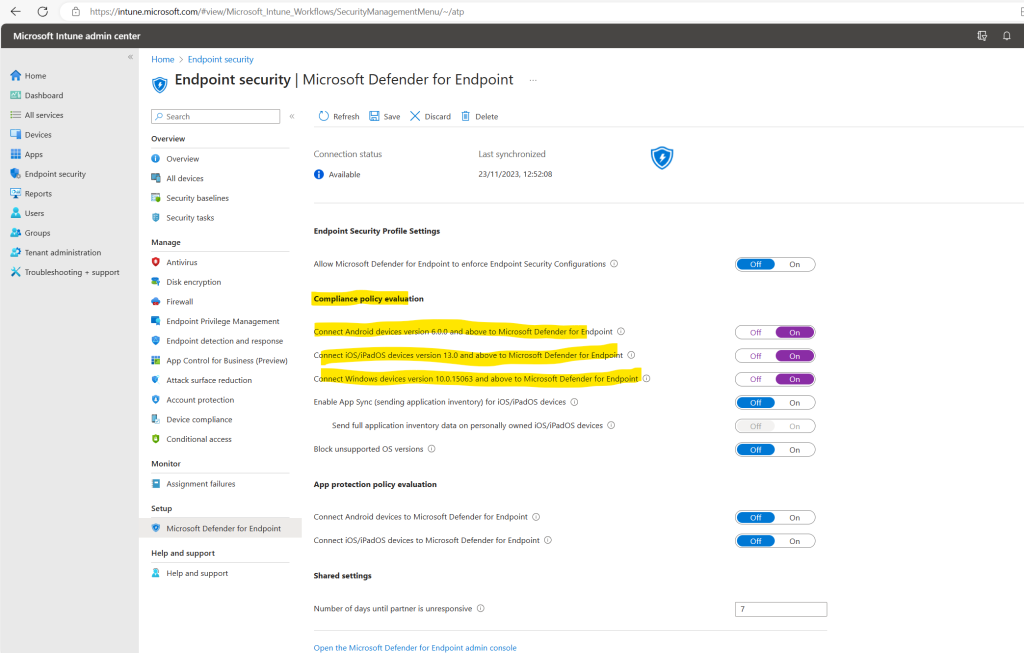
After enabling these policies in order to connect these devices to Microsoft Defender for Endpoint, the connection status now shows enabled.
When on, compliance policies using the Device Threat Level rule will evaluate devices including data from this connector.
When off, Intune will not use device risk details sent over this connector during device compliance calculation for policies that have a Device Threat Level configured. Existing devices that are not compliant due to risk levels obtained from this connector will also become compliant.
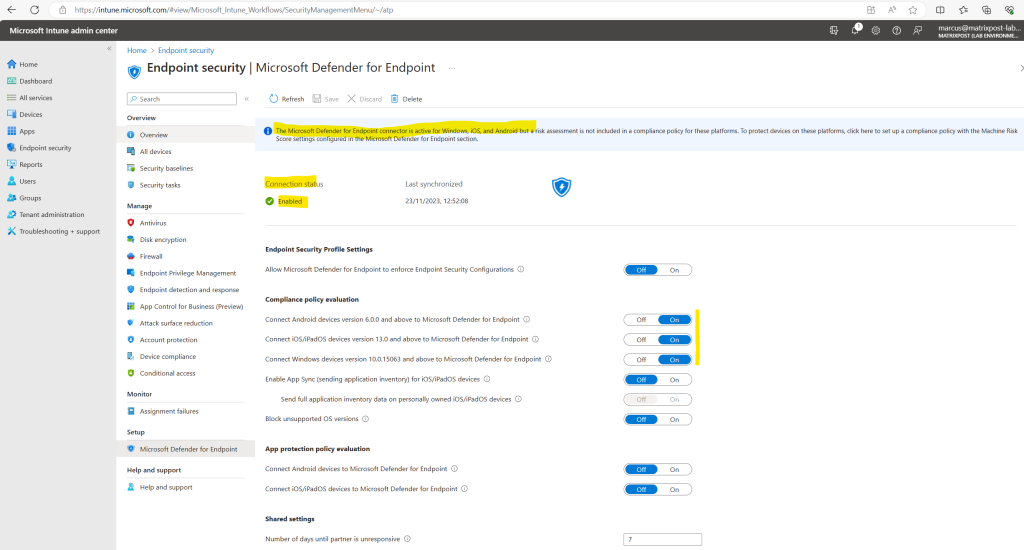
On the screenshot above I will also see a banner which notifies me that risk assessment is not included in a compliance policy for the platforms I enabled.
The Microsoft Defender for Endpoint connector is active for Windows, iOS, and Android but a risk assessment is not included in a compliance policy for these platforms. To protect devices on these platforms, click here to set up a compliance policy with the Machine Risk Score settings configured in the Microsoft Defender for Endpoint section.
Therefore I will set up a new compliance policy for my Windows devices by clicking on the banner above.
Enter a name for the policy.
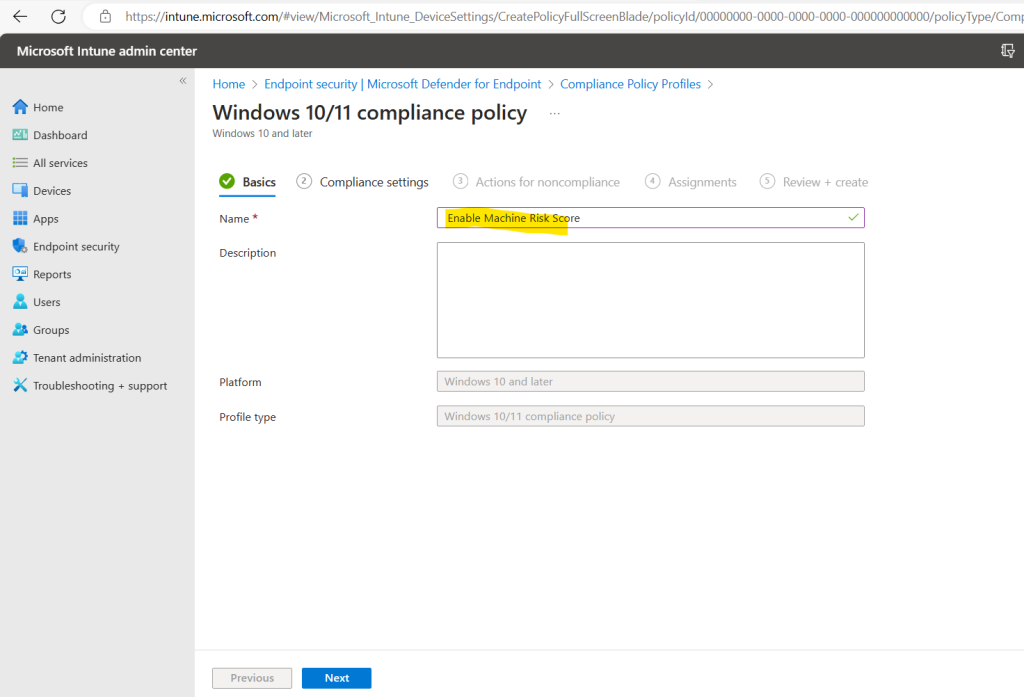
In the Compliance settings tab we need to expand the Microsoft Defender for Endpoint section where we can select our maximum allowed machine risk score. I will select here Medium.
Select the maximum allowed machine risk score for devices evaluated by Microsoft Defender for Endpoint. Devices which exceed this score get marked as noncompliant.
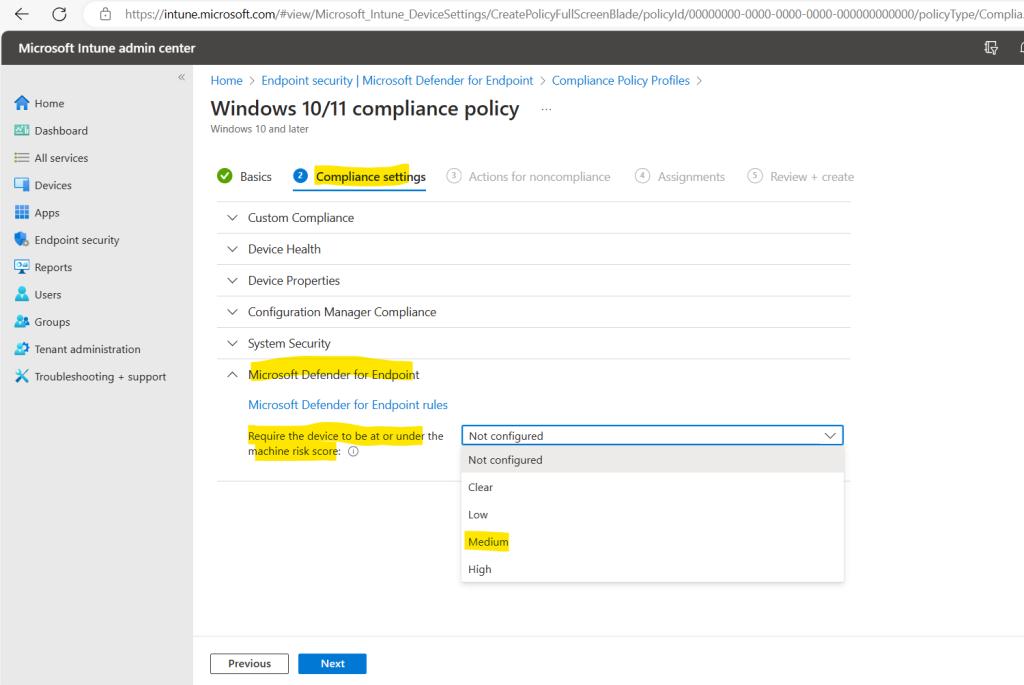
We can also specify a sequence of actions which will be applied for noncompliant devices like sending an email to the end user. I will skip this step.
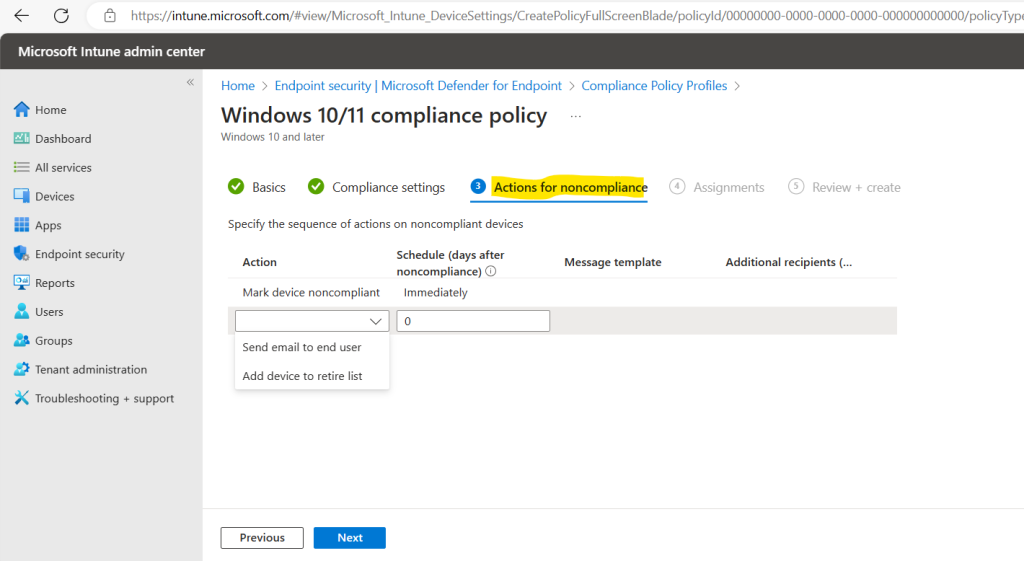
Under Assignments we can select to which users or devices the policy should be assigned. I will assign this policy to all devices in my lab tenant.
Finally I will create the rule.
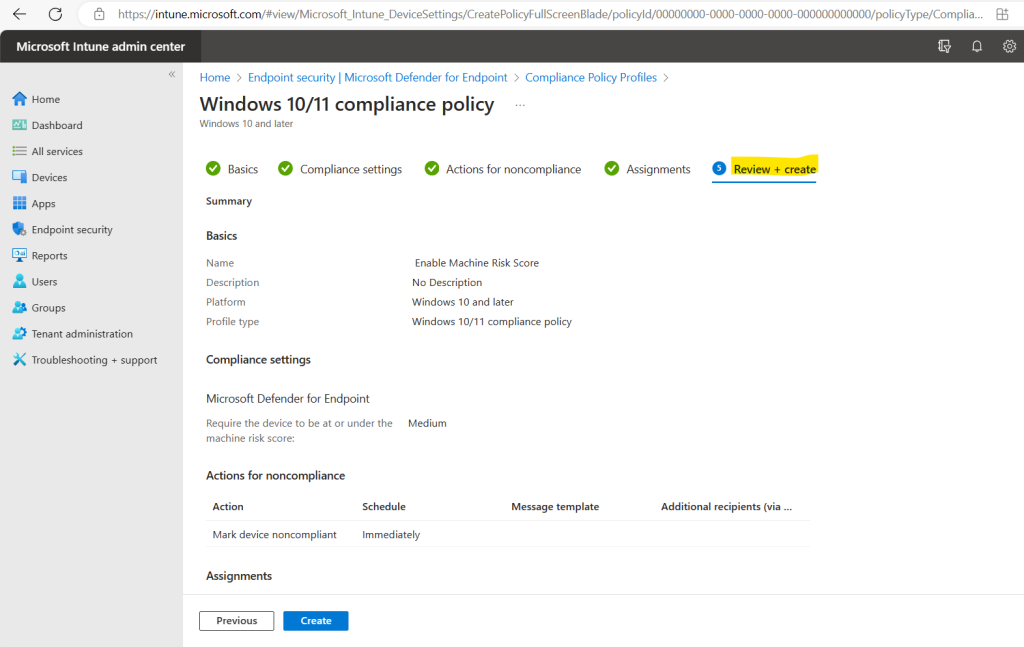
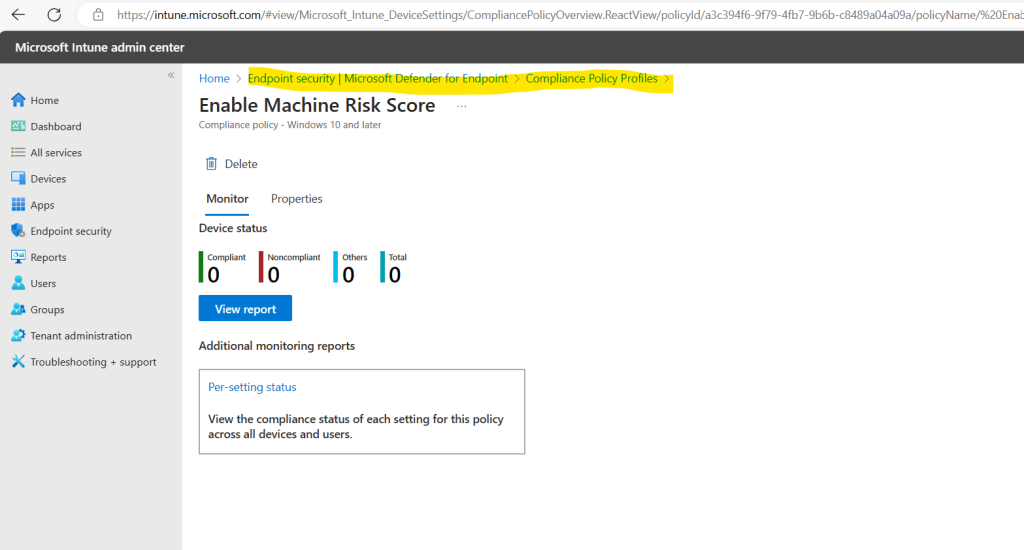
As you can see, now the banner shows only that iOS and Android devices are still missing a risk assessment policy.
In my case I will use in my lab tenant just Windows devices but in order to prevent this banner shows up, I will also add a policy for IOS and Android devices.
Therefore I can either click just on the banner again or directly in the left menu on Device compliance as shown below.
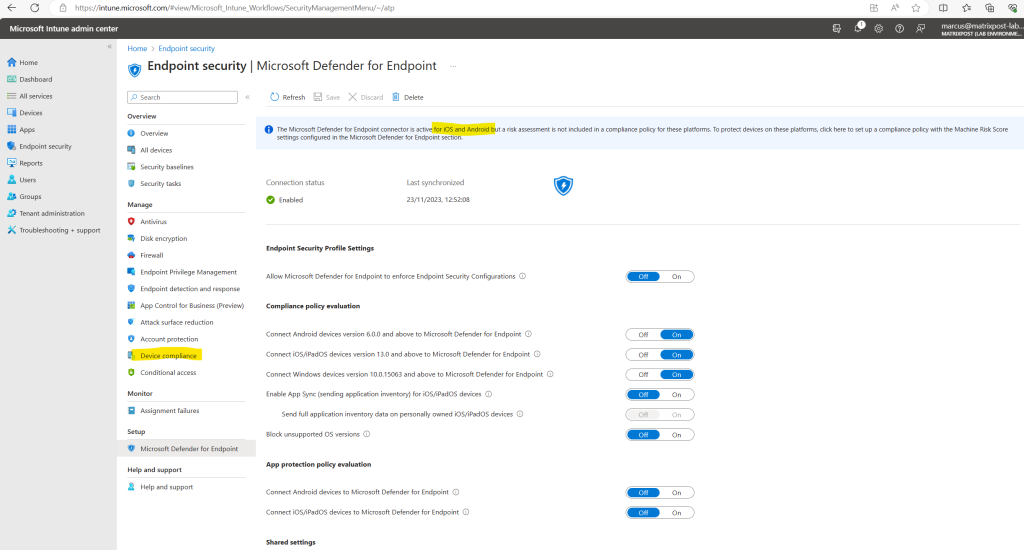
Here I will also see my previously created compliance policy for the Windows devices. I was also renaming the policy here to distinguish between the OS platforms.
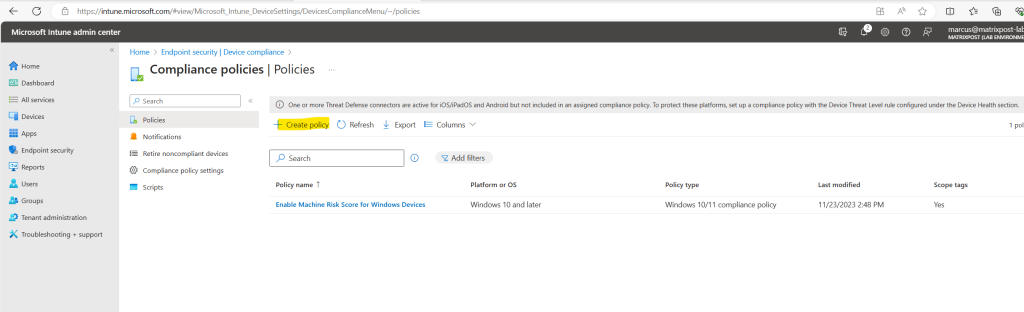
I will skip the steps to create the policy for iOS and Android devices, this will be the same as previously for Windows devices. Just one exception, for Android devices select for the platform Android device administrator, all other will not include the machine risk score policy.
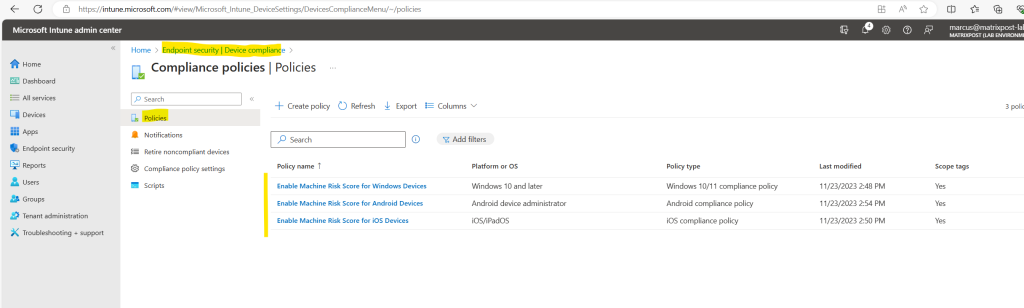
The banner now disappeared!
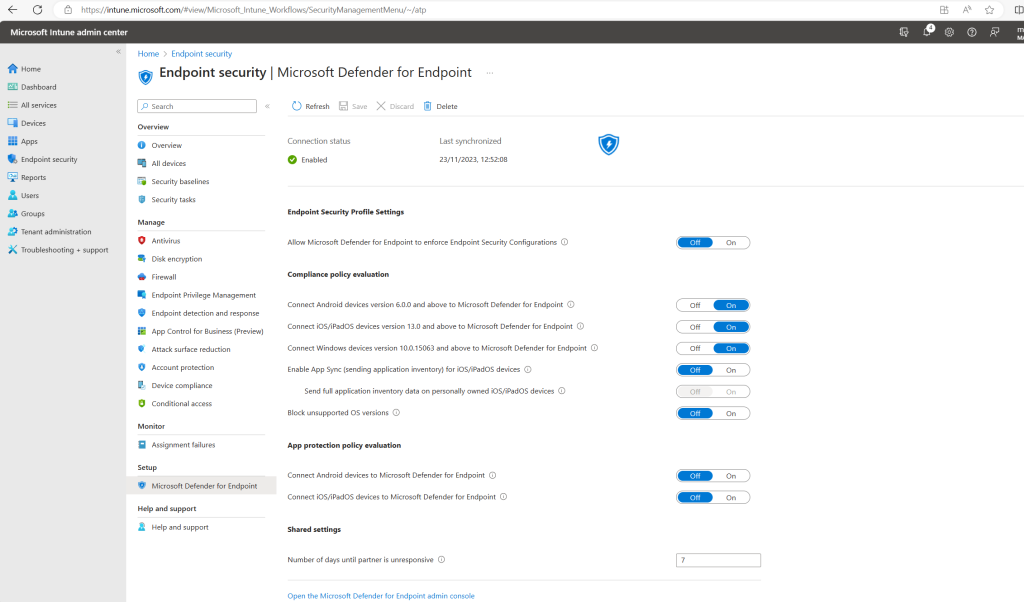
Source: https://learn.microsoft.com/en-us/mem/intune/protect/advanced-threat-protection-configure
Onboard Windows Devices to Microsoft Defender for Endpoint (MDE)
Defender for Endpoint provides several options for onboarding Windows devices. I will show here in my post three of them. Two of these options will onboard devices they already enrolled in Microsoft Intune and one which will onboard devices directly to Microsoft Defender for Endpoint and are not enrolled to an MDM solution.
Select deployment method
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/deployment-strategy?view=o365-worldwide#step-2-select-deployment-method
To onboard devices by using Microsoft Intune, you can either create a new EDR Policy and using the Endpoint detection and response profile, or you can create a predefined device configuration profile.
Both methods will finally auto populate the Microsoft Defender for Endpoint onboarding blob to the devices.
The predefined device configuration profile will finally also shown up under the Endpoint detection and response policies.
Onboard by using an EDR Policy
When you enabled support for Microsoft Defender for Endpoint in Intune, you established a service-to-service connection between Intune and Microsoft Defender for Endpoint. You can then onboard devices you manage with Intune to Microsoft Defender for Endpoint. Onboarding enables collection of data about device risk levels.
When onboarding devices, be sure to use most recent version of Microsoft Defender for Endpoint for each platform.
So far no devices are on-boarded to Microsoft Defender for Endpoint.
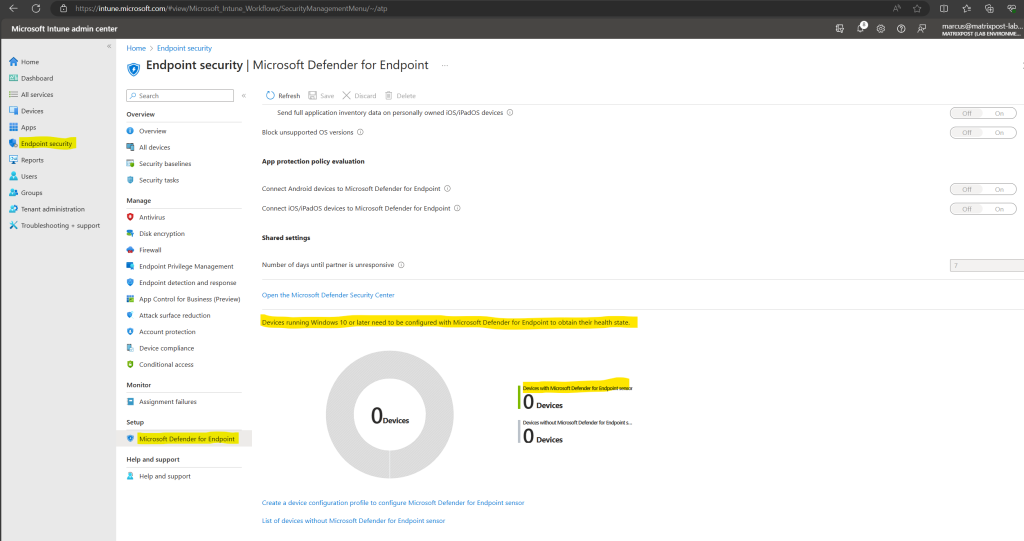
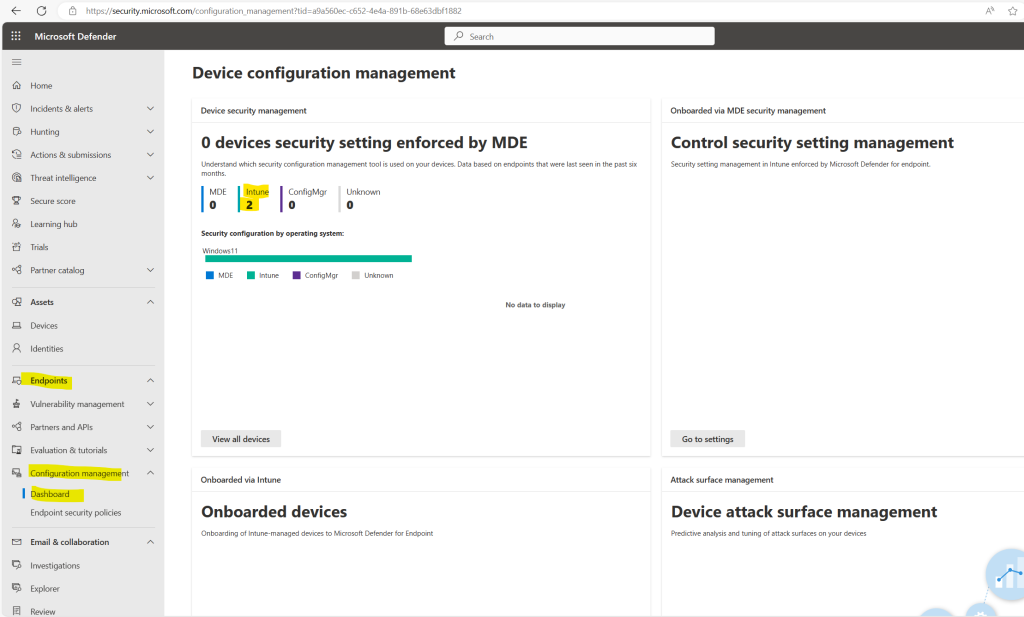
You can check this also in the Microsoft 365 Defender portal under Endpoints -> Configuration management -> Dashboard.
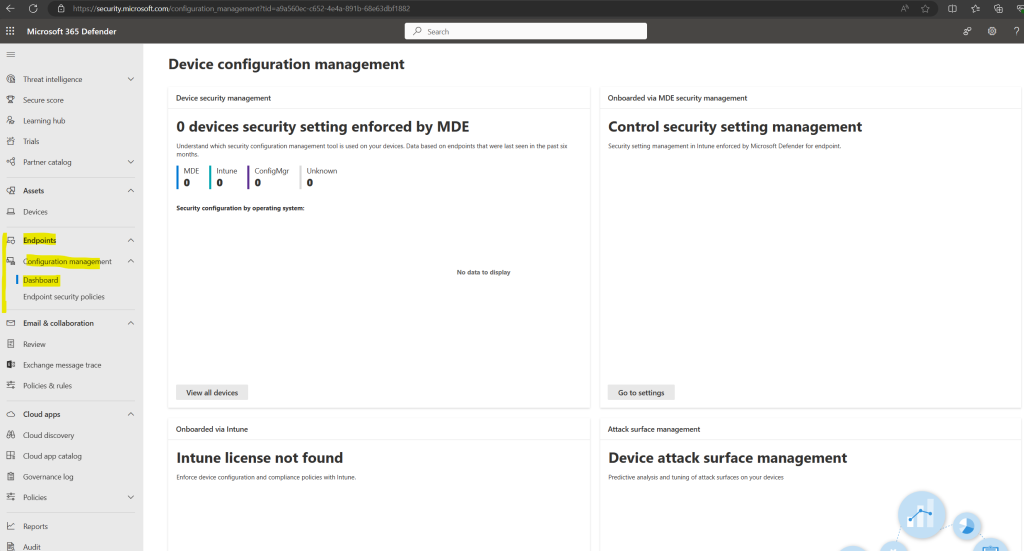
After you connect Intune and Microsoft Defender for Endpoint, Intune receives an onboarding configuration package from Microsoft Defender for Endpoint. You use a device configuration profile for Microsoft Defender for Endpoint to deploy the package to your Windows devices.
The configuration package configures devices to communicate with Microsoft Defender for Endpoint services to scan files and detect threats. The device also reports its risk level to Microsoft Defender for Endpoint based on your compliance policies.
We can now onboard devices to Microsoft Defender for Endpoint by creating an Endpoint detection and response policy (EDR policy) in Microsoft Intune.
Sign in to the Microsoft Intune admin center.
Select Endpoint security > Endpoint detection and response > Create Policy.
For Platform, select Windows 10 and Later. For Profile type, select Endpoint detection and response, and then select Create.
When you integrate Microsoft Defender for Endpoint with Intune, you can use endpoint security policies for endpoint detection and response (EDR) to manage the EDR settings and onboard devices to Microsoft Defender for Endpoint.
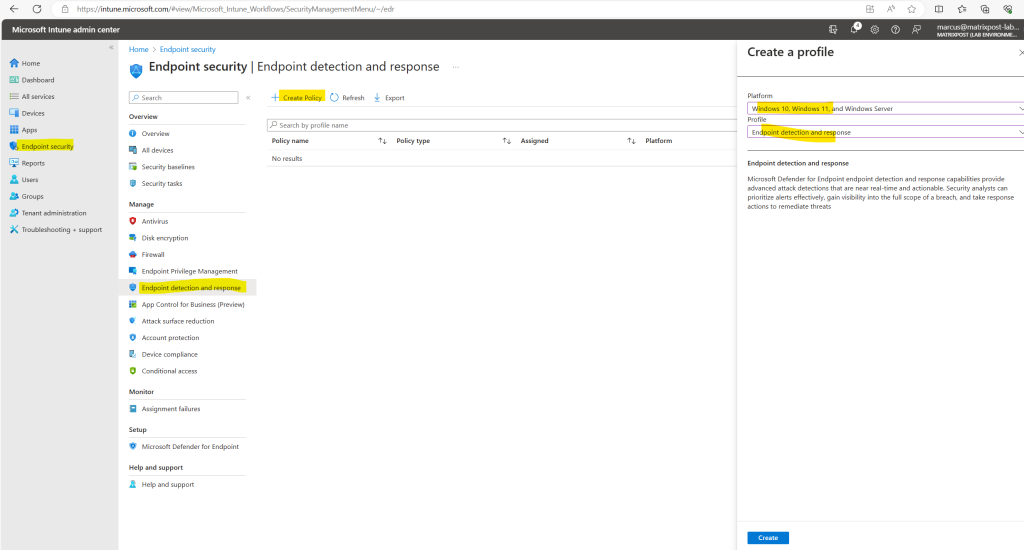
On the Basics page, enter a Name and Description (optional) for the profile, then choose Next.
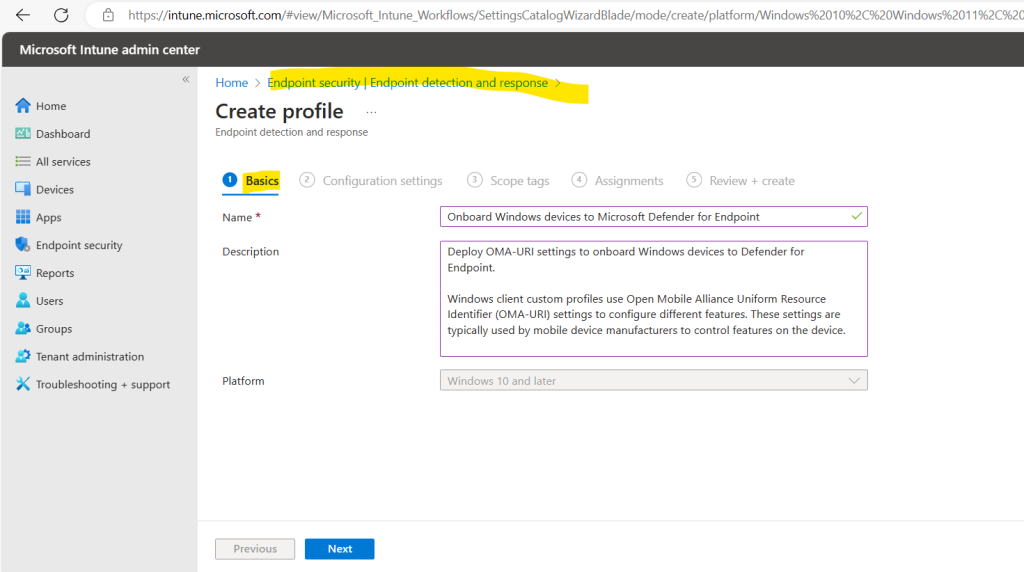
On the Configuration settings page, configure the following options for Endpoint Detection and Response:
- Sample sharing for all files: Returns or sets the Microsoft Defender for Endpoint Sample Sharing configuration parameter.
Sample Sharing sends a file to Microsoft for deep analysis. Organizations can disable sample sharing on specific devices that are considered too sensitive. - Expedite telemetry reporting frequency: For devices that are at high risk, Enable this setting so it reports telemetry to the Microsoft Defender for Endpoint service more frequently.
The main point here is to select how you want to deploy the configuration package. As already mentioned, after you connect Intune and Microsoft Defender for Endpoint, Intune receives an onboarding configuration package from Microsoft Defender for Endpoint.
So I will select here Auto from connector to use the package, Intune receives directly by the connector from Microsoft Defender for Endpoint.
With this option, Intune automatically gets the onboarding package (blob) from your Defender for Endpoint deployment, replacing the need to manually configure an Onboard package.
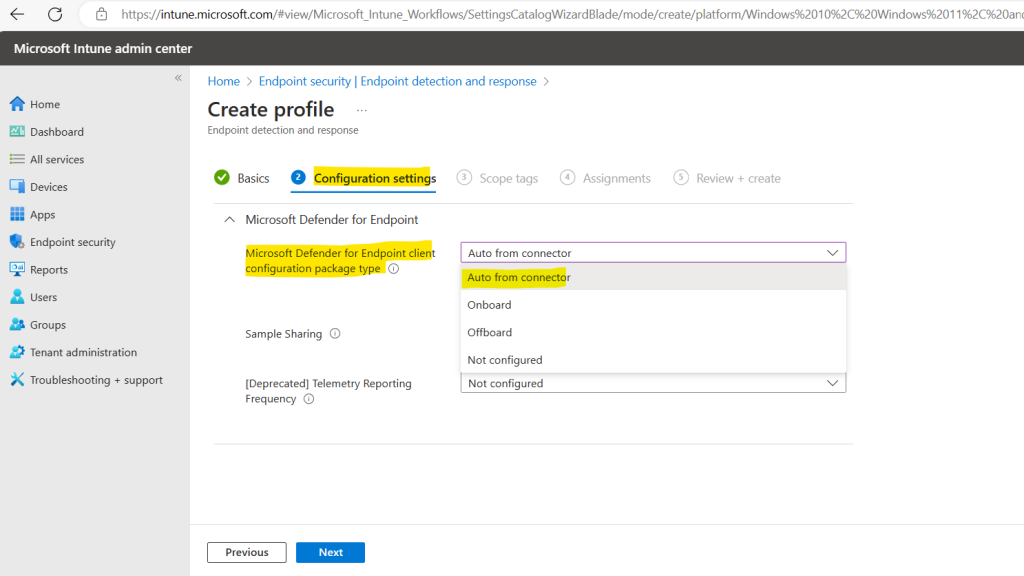
Because I am here in my lab tenant and therefore doesn’t have any sensitive devices within, I will select for Sample Sharing “All” and for the Telemetry Reporting Frequency “Normal”.
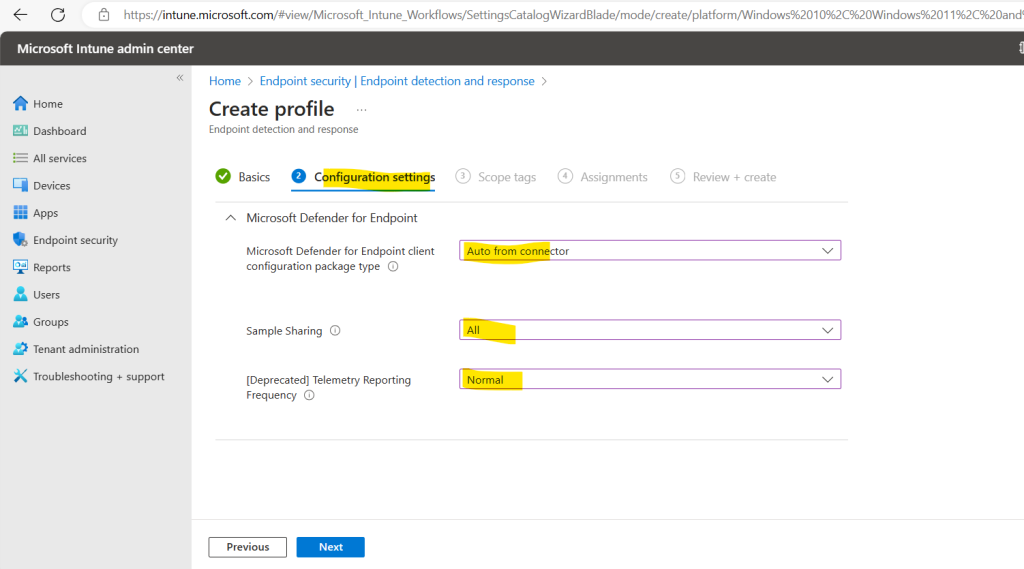
Scope tags I will skip and navigate directly to the Assignments tab.
Here I will assign the EDR policy to all devices.
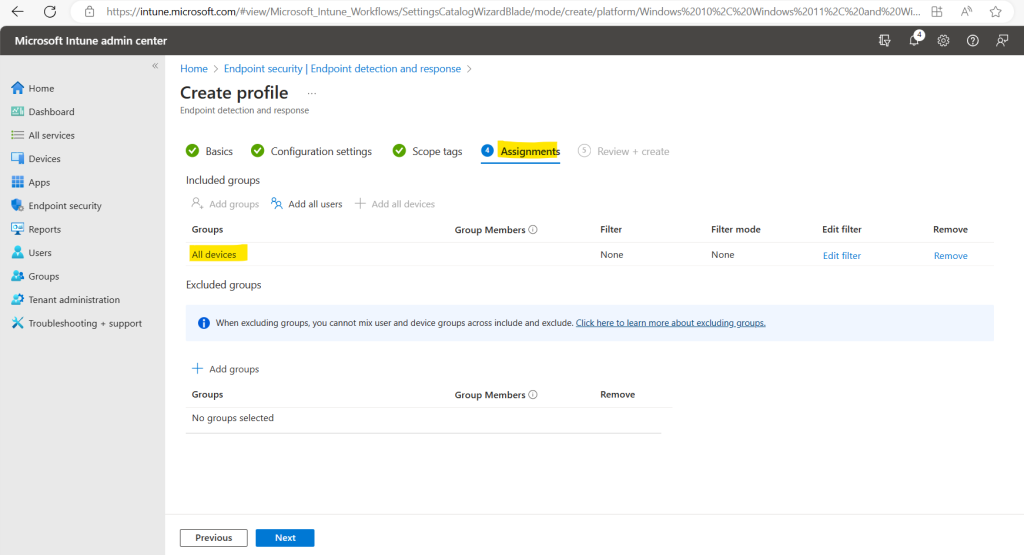
Finally I will create the EDR policy.
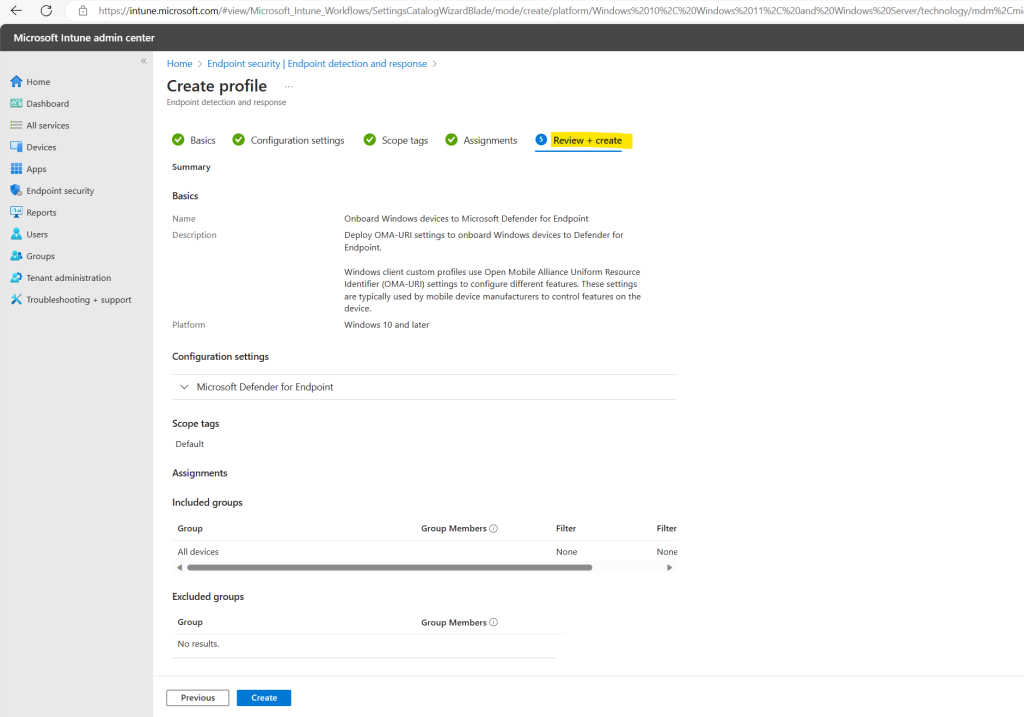
To check the device assignment status for the newly created EDR policy, we can click below on the policy to view a report.
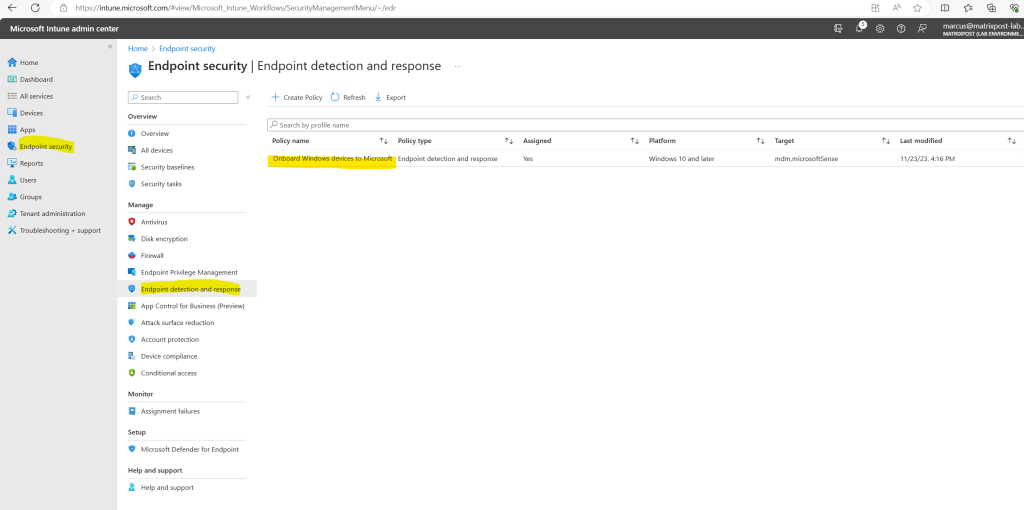
Click on view report. I can see here that the policy is already assigned to 2 devices.
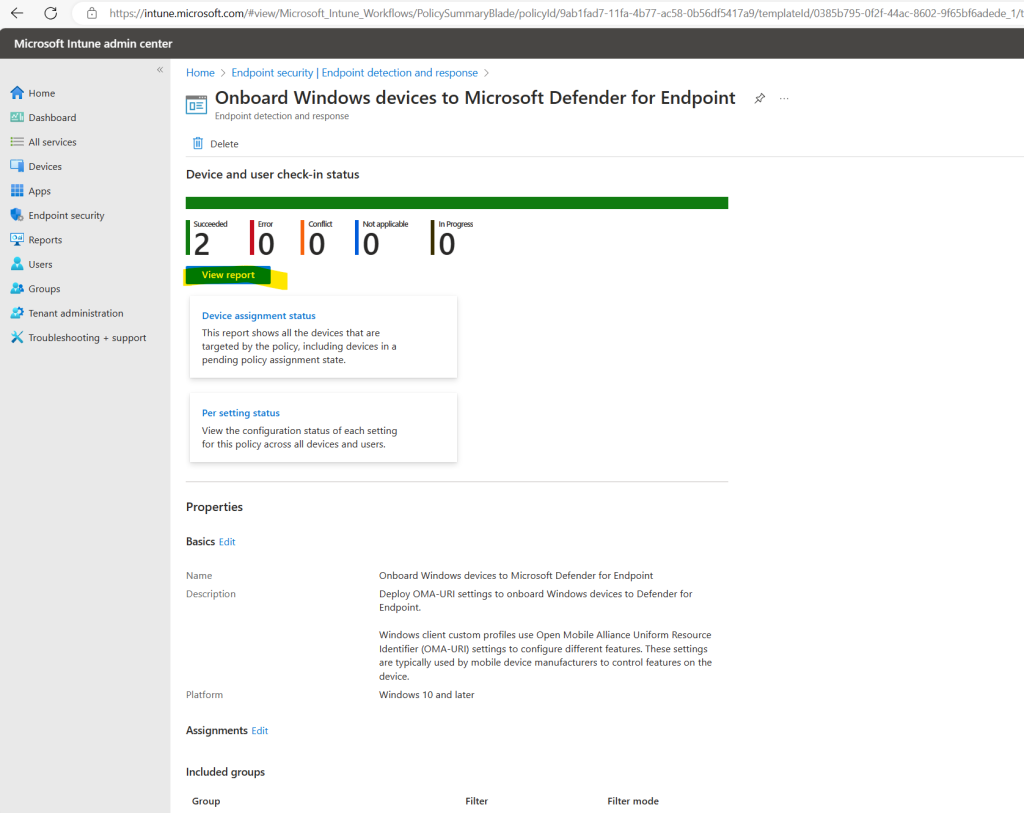
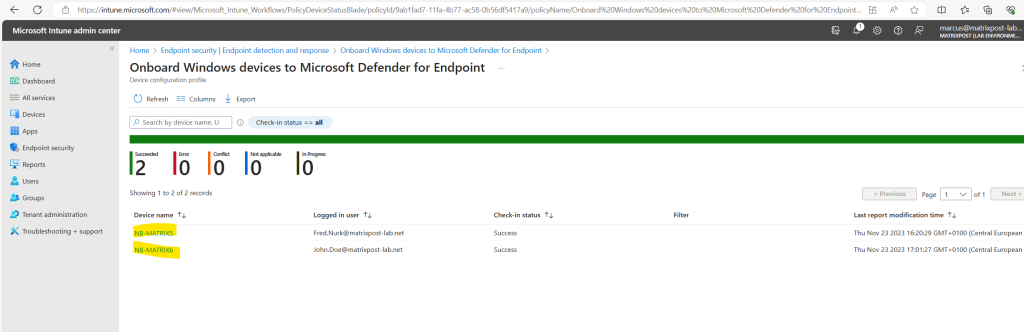
Unfortunately in the Microsoft Intune admin center the devices are still not on-boarded to Microsoft Defender for Endpoint.
Within the Microsoft Defender portal under Endpoints -> Configuration management -> Dashboard the two devices are shown up already as onboarded.
They shown up within the device configuration management section under Intune which just means that their security configuration settings will be enforced by Intune.
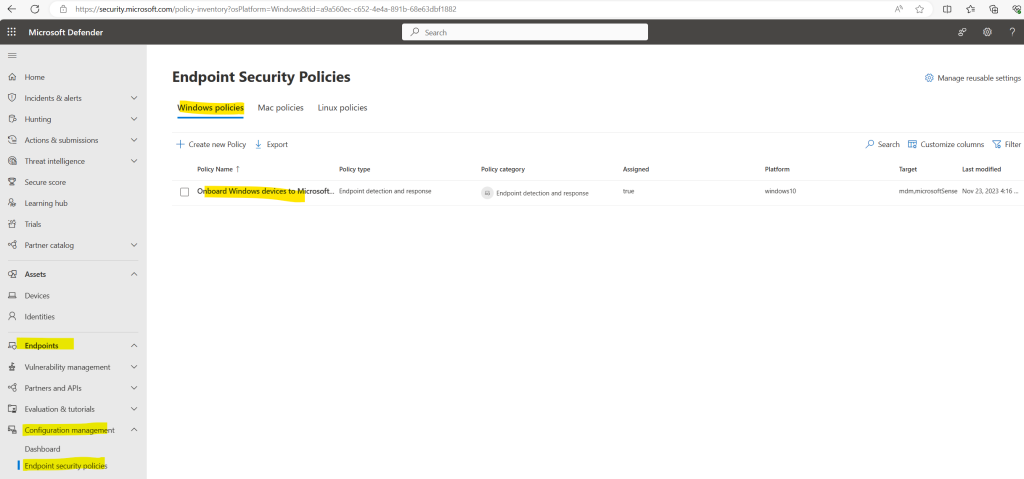
By checking the policy in the Microsoft Defender portal I can also see that the onboarding configuration package was applied successfully to both devices.
Onboard by using Intune Profiles
We can also leverage Intune profiles to conveniently deploy the Defender for Endpoint sensor to devices which will effectively onboarding them to the service.
On the Microsoft Defender for Endpoint page within Microsoft Intune you can directly click on the link shown below Create a device configuration profile to configure Microsoft Defender for Endpoint sensor to start with a predefined device configuration profile.
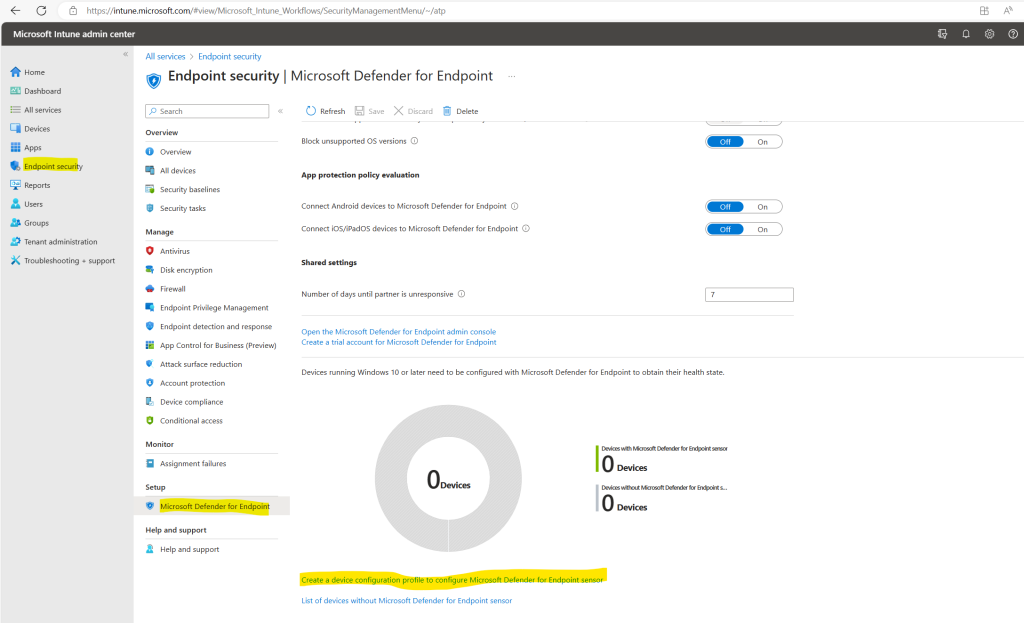
Enter a name and description for the device configuration profile (policy).
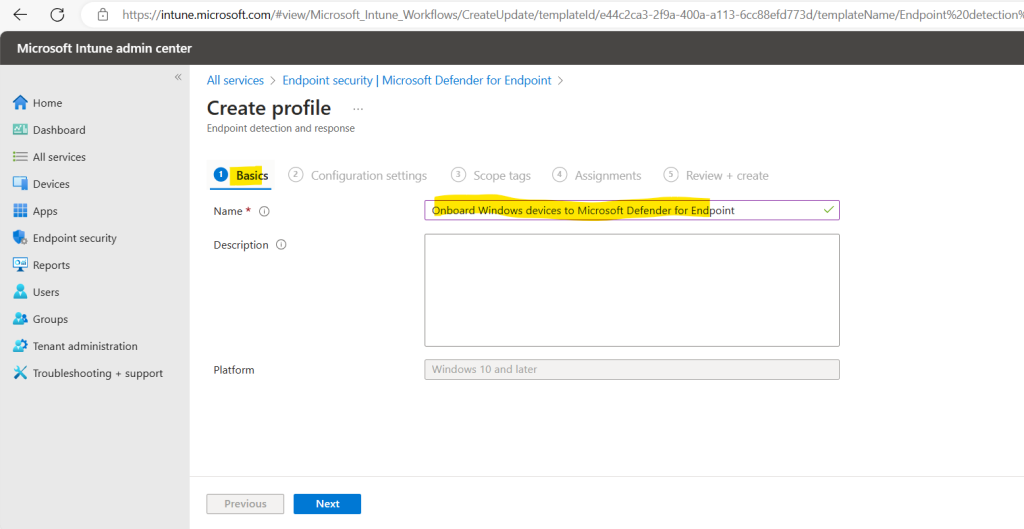
On the next Configuration settings page below, configure the following options for Endpoint Detection and Response:
- Sample sharing for all files: Returns or sets the Microsoft Defender for Endpoint Sample Sharing configuration parameter.
Sample Sharing sends a file to Microsoft for deep analysis. Organizations can disable sample sharing on specific devices that are considered too sensitive. - Expedite telemetry reporting frequency: For devices that are at high risk, Enable this setting so it reports telemetry to the Microsoft Defender for Endpoint service more frequently.
As already mentioned, after you connect Intune and Microsoft Defender for Endpoint, Intune receives an onboarding configuration package from Microsoft Defender for Endpoint.
By default the onboarding configuration package will be added here behind the scenes, you will see this further down on the Review + Create tab.
With this option, Intune automatically gets the onboarding package (blob) from your Defender for Endpoint deployment, replacing the need to manually configure an Onboard package.
The next Scope tags tab I will skip. Under the Assignments tab I will assign the profile to all devices in my lab tenant.
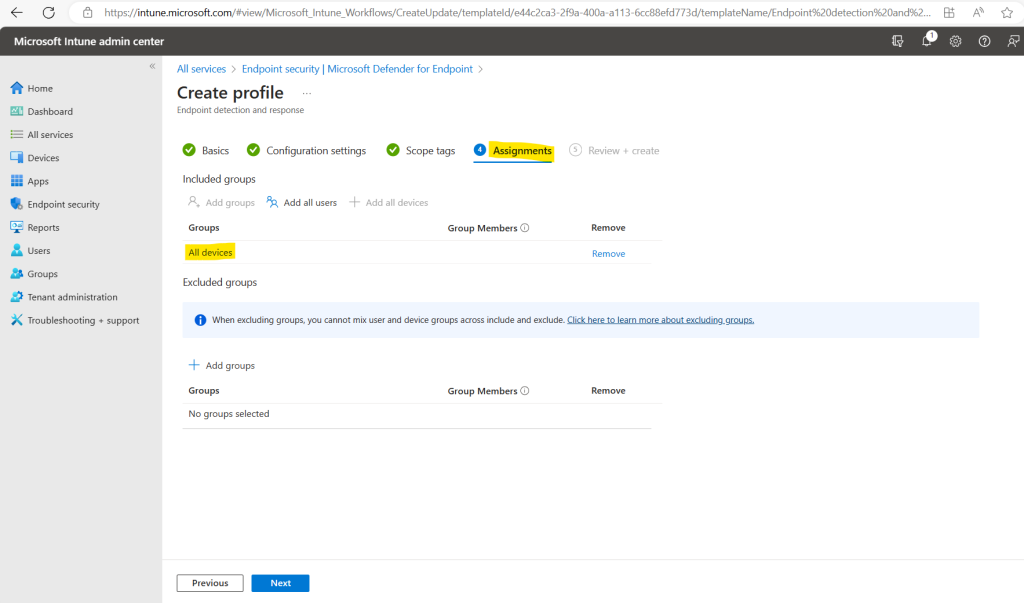
Finally we can create the profile.
As already mentioned, within Configuration settings section on the Review + Create tab, you will see that we deploy with this profile the configuration package blob to the assigned devices in order to onboard them to Microsoft Defender for Endpoint.
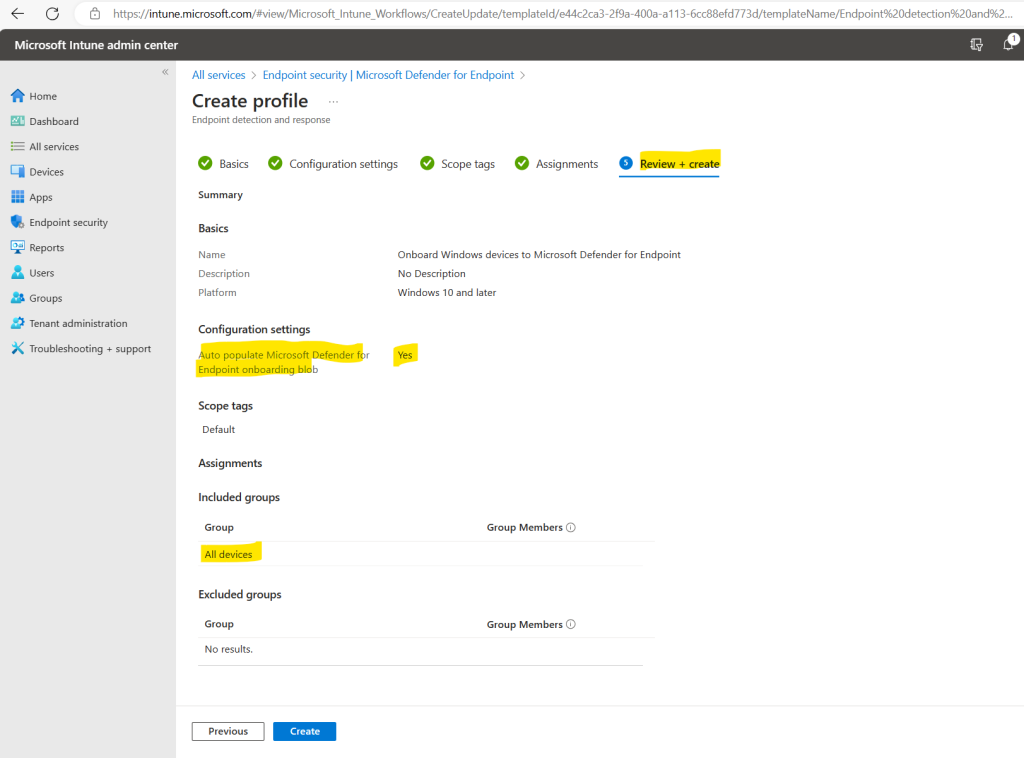
The profile (policy) is created.
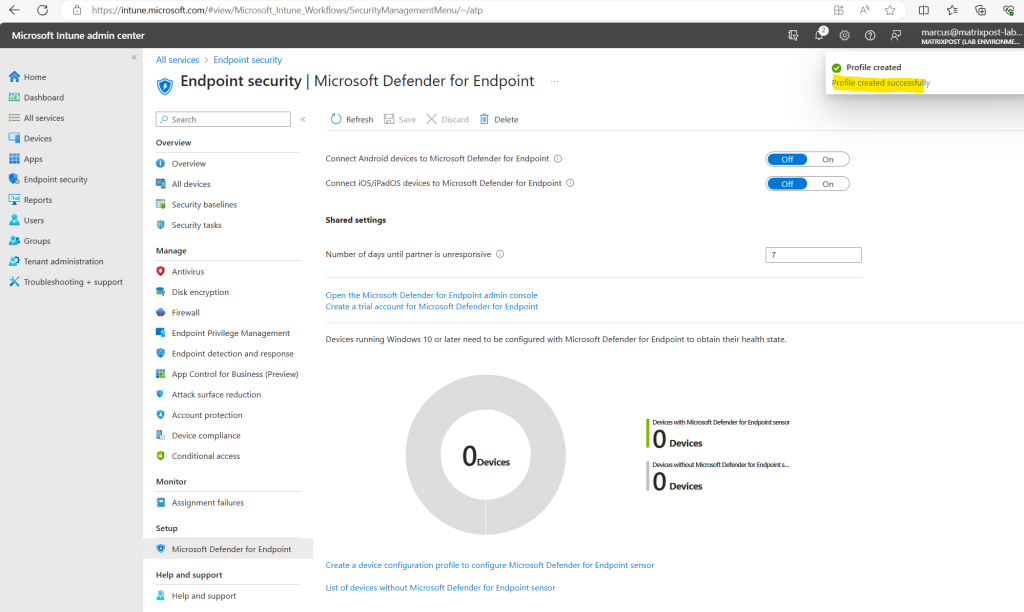
The previously created device configuration profile you will find as new policy in Microsoft Intune under Endpoint security -> Endpoint detection and response.
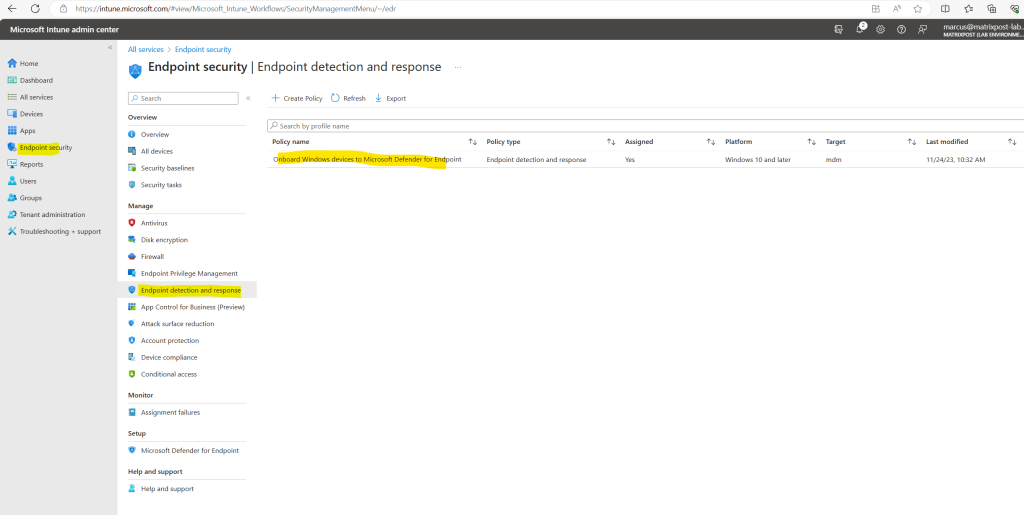
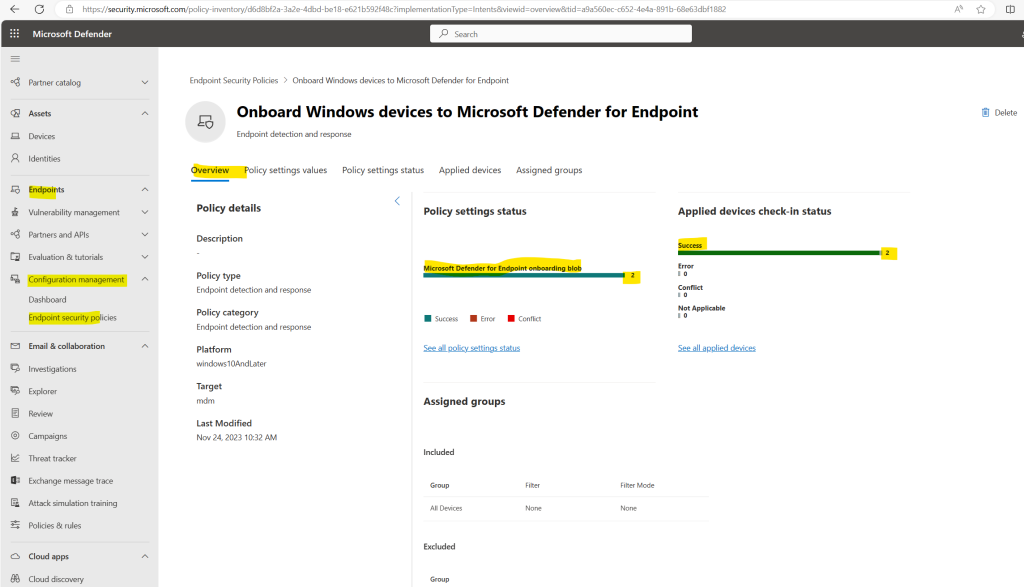
You will find the device configuration profile also as new policy in the Microsoft Defender portal under Endpoints -> Configuration Management – > Endpoint security policies as shown below.
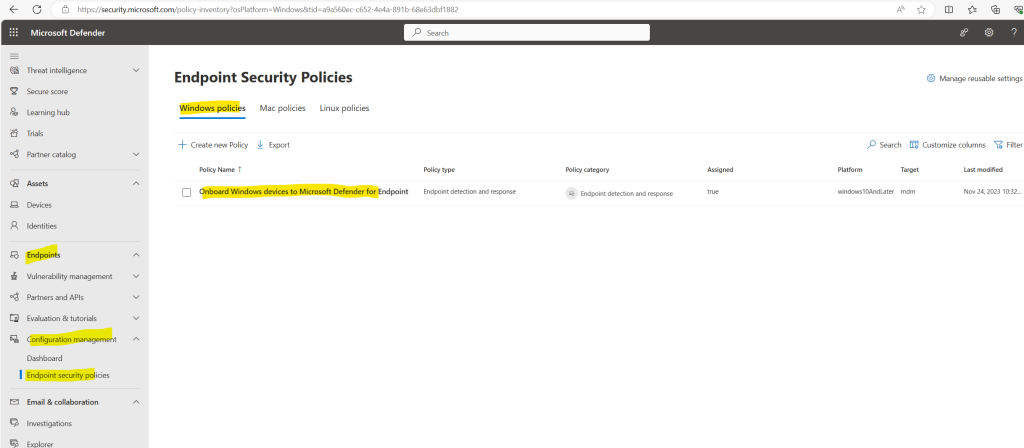
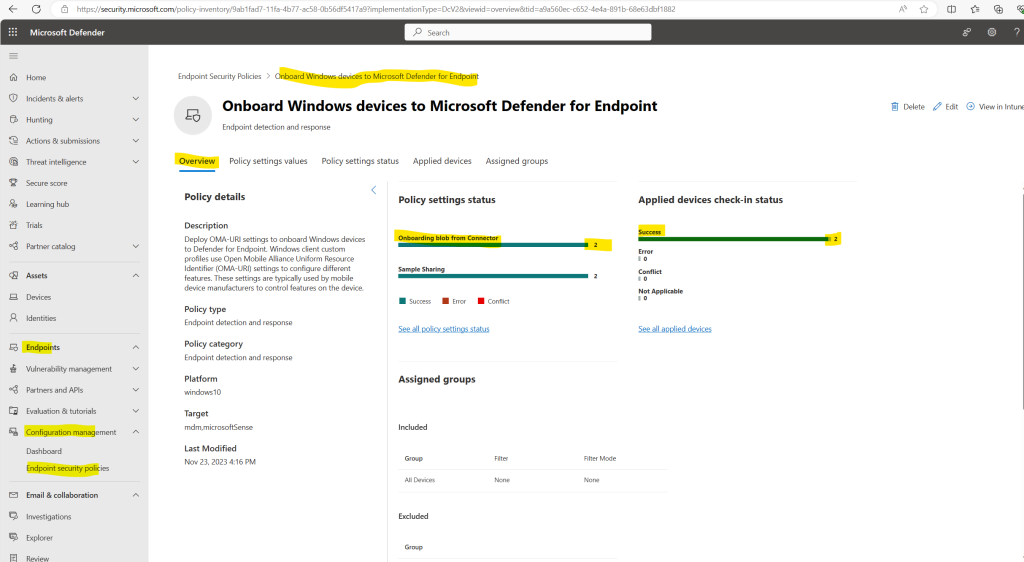
When clicking on the policy you will see further details like policy settings, status and applied devices.
So the policy is just applied to one of my two devices in the lab environment.
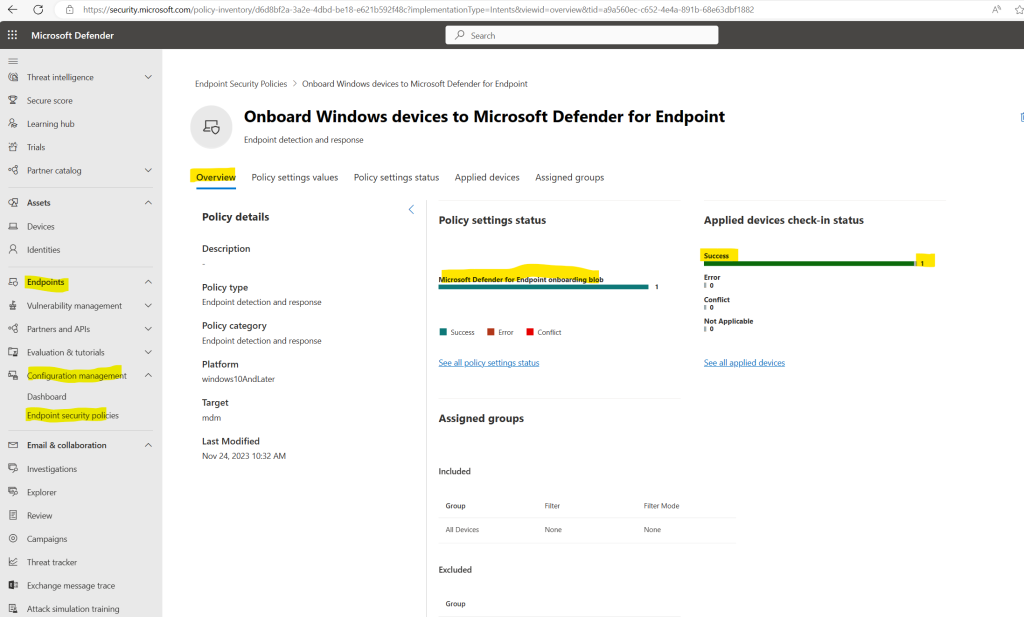
Within the Policy settings values tab you can review the settings for.
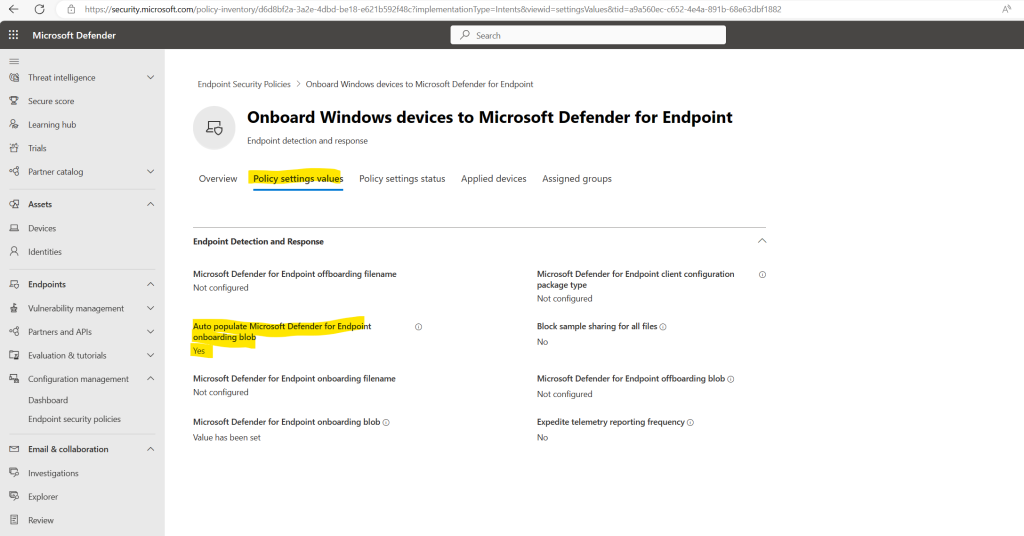
Policy settings status tab
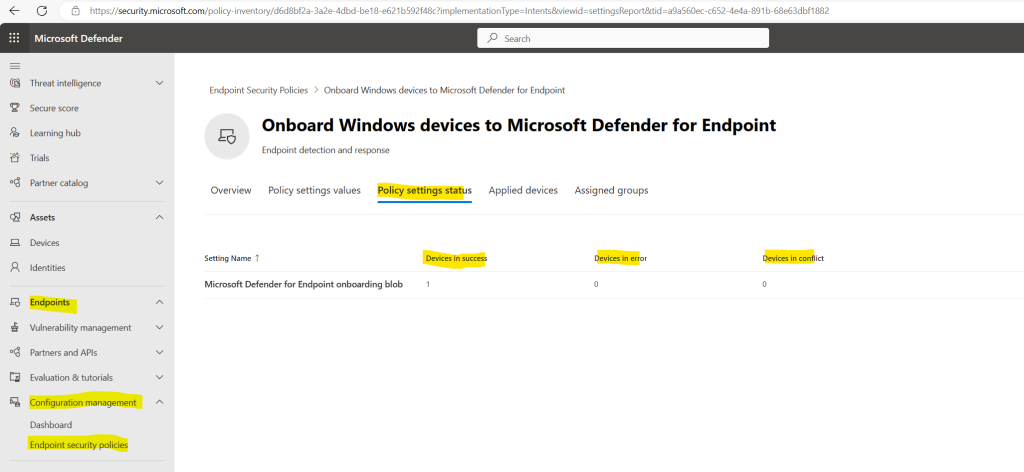
Here you can see all of your devices enrolled in Microsoft Intune with the Check-in status for Microsoft Defender for Endpoint.
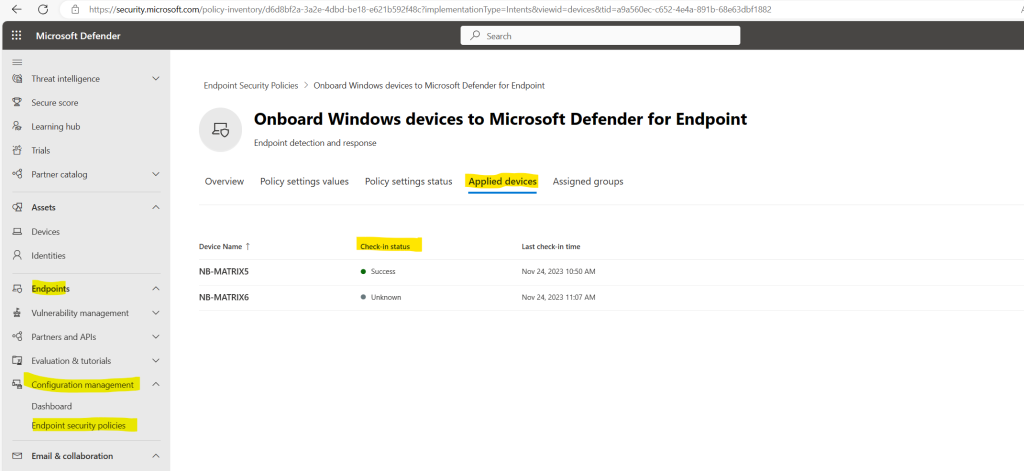
Assigned groups (devices)
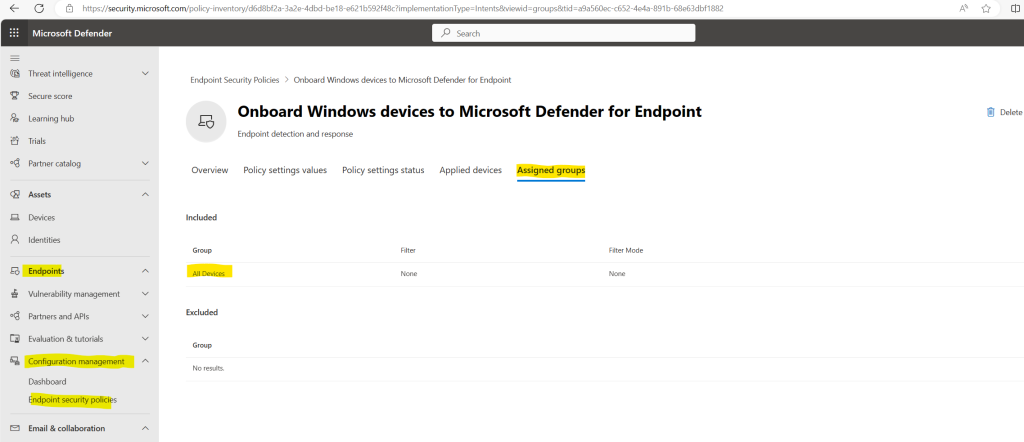
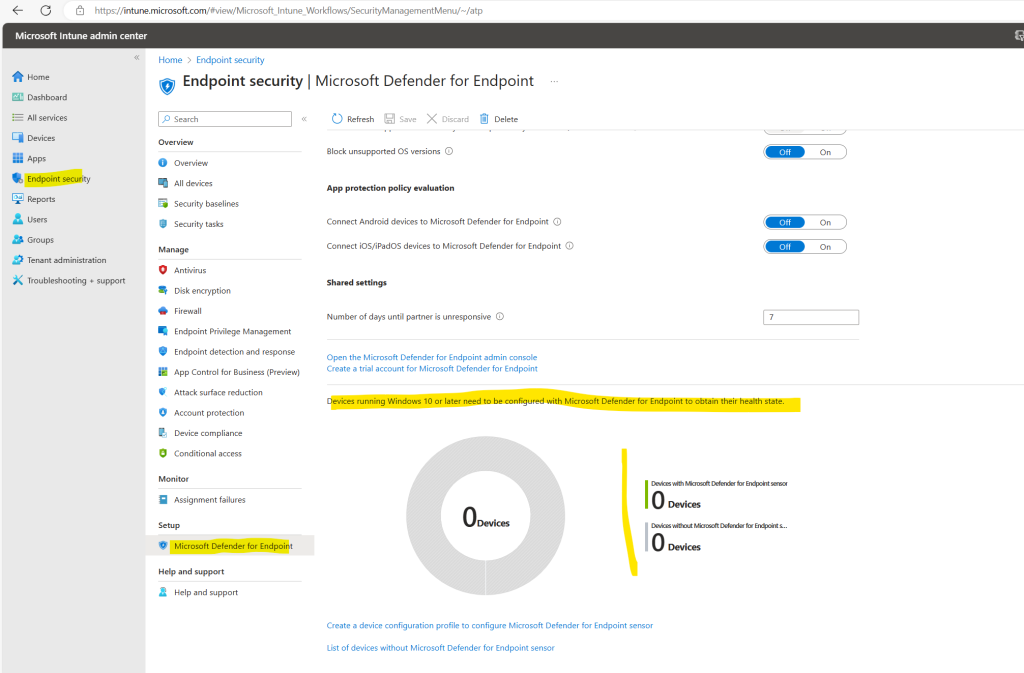
On the Microsoft Defender for Endpoint page in Microsoft Intune there are still no onboarded devices shown up.
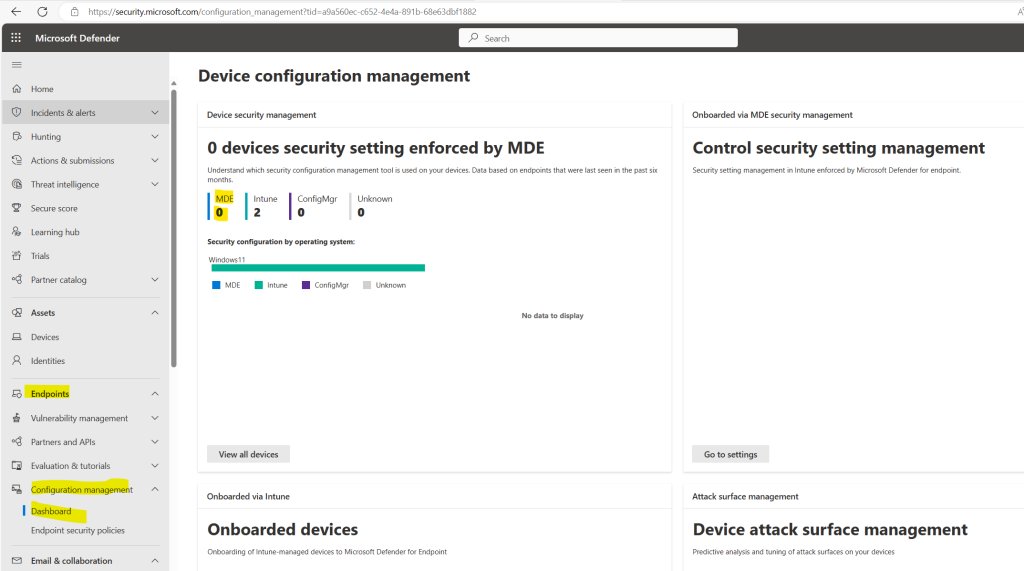
On the Dashboard in the Microsoft Defender portal under Endpoints -> Configuration management -> Dashboard we can see both devices already shown up under Device configuration management by Intune.
So both devices are onboarded successfully to Microsoft Defender for Endpoint.
You can see here also highlighted in yellow MDE with 0 devices. Devices shown up here meant, that their security configuration settings will be enforced directly by Microsoft Defender for Endpoint (MDE) instead of Intune, ConfigMgr or others. Further these devices onboarded directly to Microsoft Defender for Endpoint. Further down we will see how we can onboard devices which are not enrolled to Intune directly to Microsoft Defender for Endpoint.
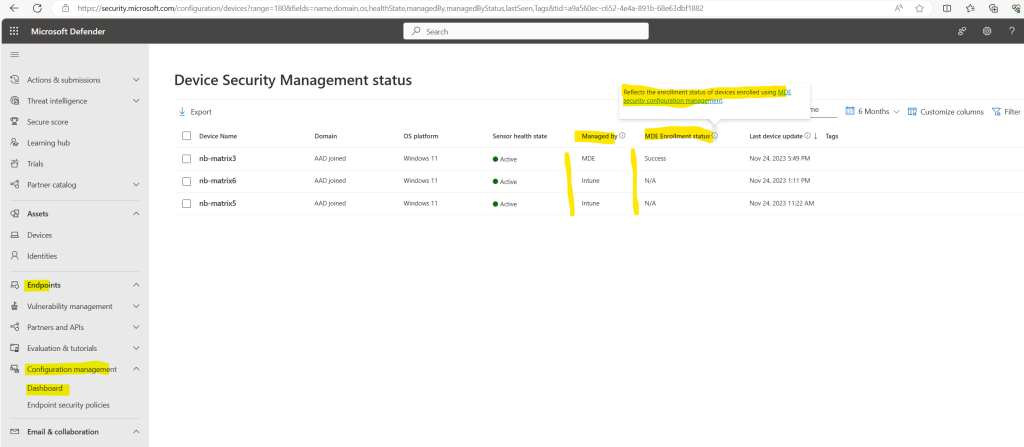
When we click above on View all devices, we will see all of our onboarded devices to Microsoft Defender for Endpoint.
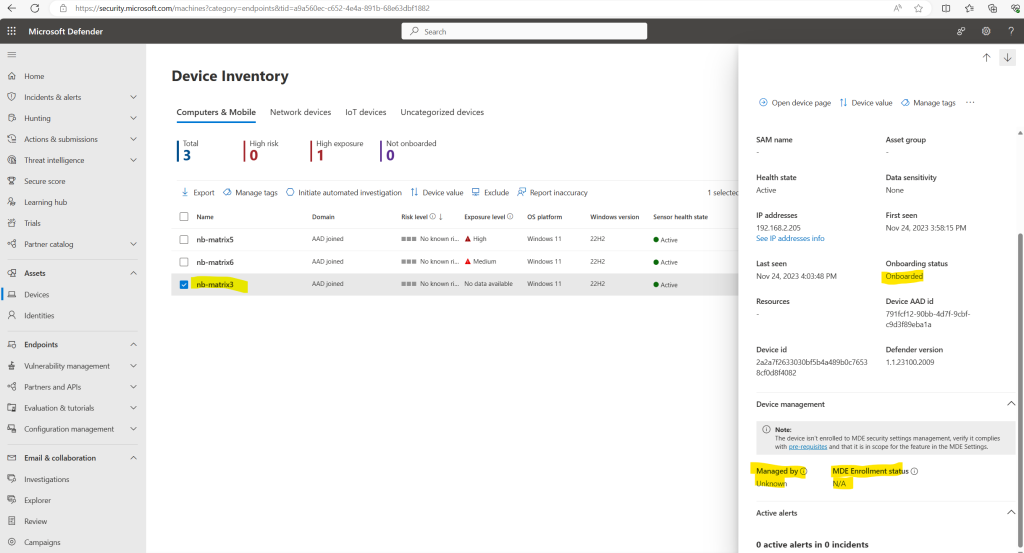
The nb-matrix3 device is not enrolled to Intune and was onboarded directly to Microsoft Defender for Endpoint. Therefore under Managed by is listed MDE and the MDE Enrollment status shows Success.
This status I find a little bit confusing, the two other devices which are enrolled to Intune shows here N/A for not available. This doesn’t meant that they were not already onboarded to MDE, this status is just for devices they were enrolled directly to MDE by using MDE security configuration management which I will show further down.
About 1h later both devices in my lab tenant finally shown up also as enrolled to Microsoft Defender for Endpoint in the Microsoft Intune portal on the connection status page as shown below.
In another tenant I experienced here that it took much longer, about 24h until the devices appears here as onboarded to Microsoft Defender for Endpoint.
In the Microsoft Defender portal you will also see that meanwhile the policy with the device configuration profile was applied successfully to both devices.
Onboard Devices directly to Microsoft Defender for Endpoint (MDE)
When you use Microsoft Defender for Endpoint, you can deploy endpoint security policies from Microsoft Intune to manage the Defender security settings on the devices you’ve onboarded to Defender without enrolling those devices with Intune. This capability is known as Defender for Endpoint security settings management.
This scenario extends the Microsoft Intune Endpoint Security surface to devices that aren’t capable of enrolling in Intune. When a device is managed by Intune (enrolled to Intune), the device doesn’t process policies for Defender for Endpoint security settings management. Instead use Intune to deploy policies for Defender for Endpoint to your devices.
Source: https://learn.microsoft.com/en-us/mem/intune/protect/mde-security-integration
To support security settings management through the Microsoft Intune admin center, you must enable communication between them from within each console.
Sign in to Microsoft Defender portal and go to Settings > Endpoints > Configuration Management > Enforcement Scope and enable the platforms for security settings management.
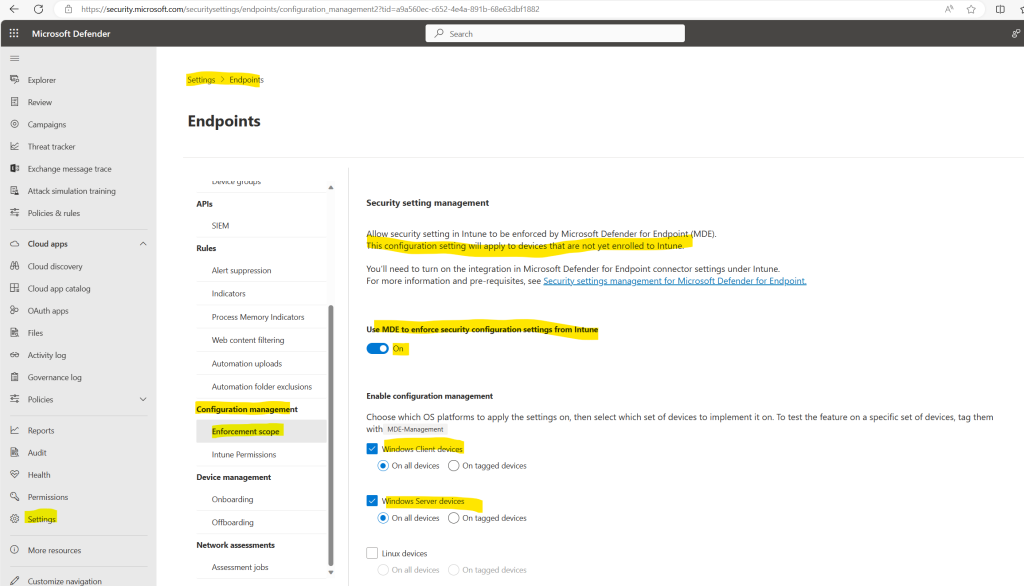
Configure the feature for Microsoft Defender for Cloud onboarded devices and Configuration Manager authority settings to fit your organization’s needs:
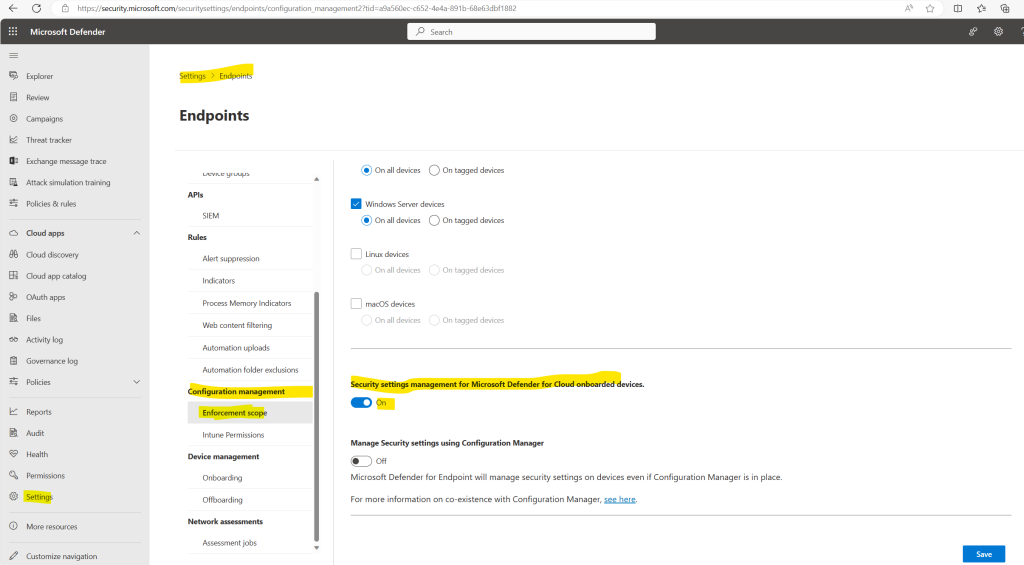
As mentioned we must enable communication in both consoles.
So also sign in to the Microsoft Intune admin center.
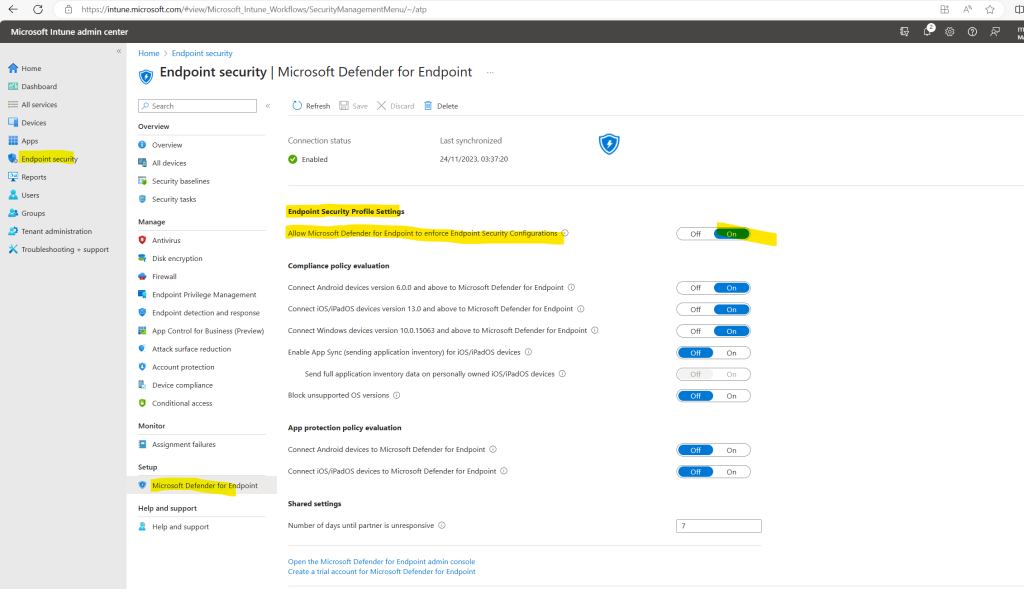
Select Endpoint security > Microsoft Defender for Endpoint, and set Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations to On.
When you set this option to On, all devices in the platform scope for Microsoft Defender for Endpoint that aren’t managed by Microsoft Intune qualify to onboard to Microsoft Defender for Endpoint.
In order to onboard devices they are not enrolled to Microsoft Intune we can use a local script which we need to run on these devices.
You can download the script directly from the Microsoft Defender portal -> Settings -> Endpoints -> Onboarding.
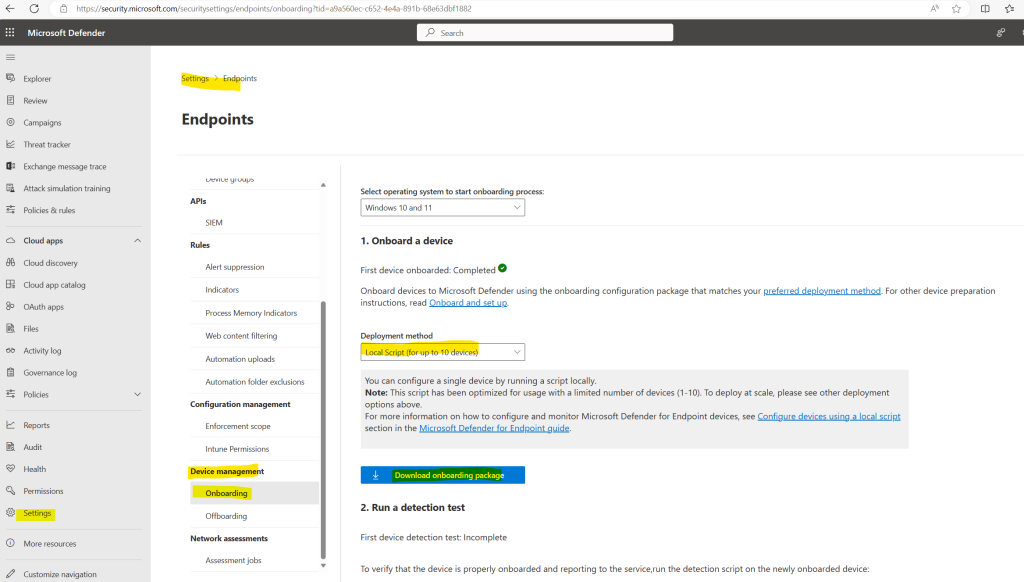
Extract the script and copy it to the device you want to onboard directly to Microsoft Defender for Endpoint.
Regarding this information the machine should be shown up in the Microsoft Defender for Endpoint portal within 5-30 minutes.
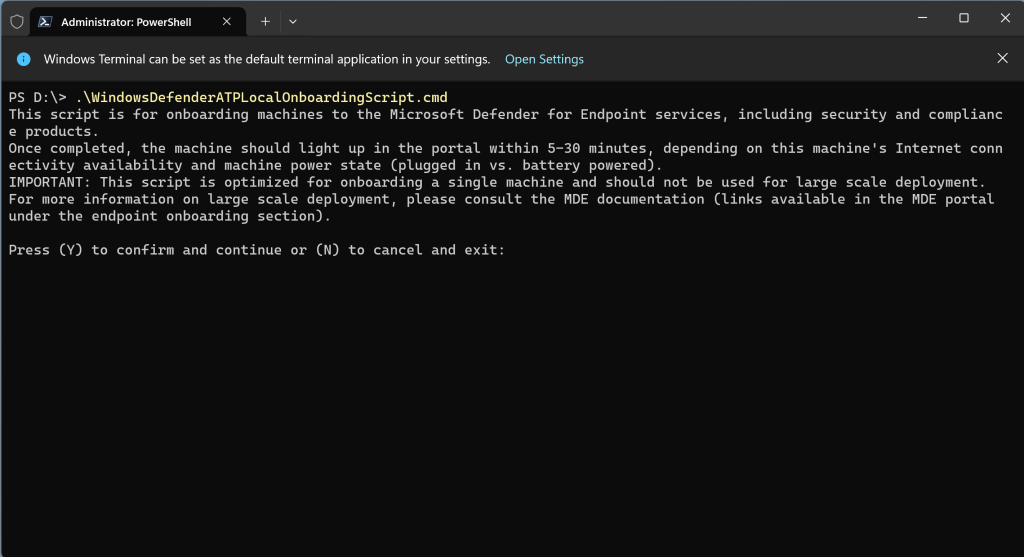
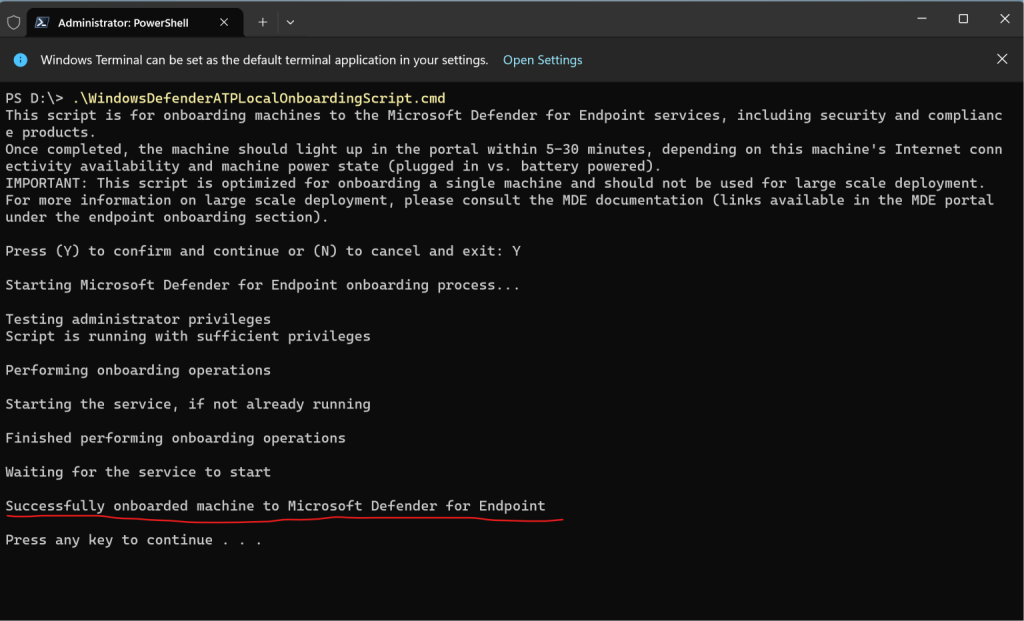
The device in my case is shown up immediately but so far as unknown by which solution the security configuration management will be enforced. This should be here normally MDE as we onboard the device directly to Microsoft Defender for Endpoint.
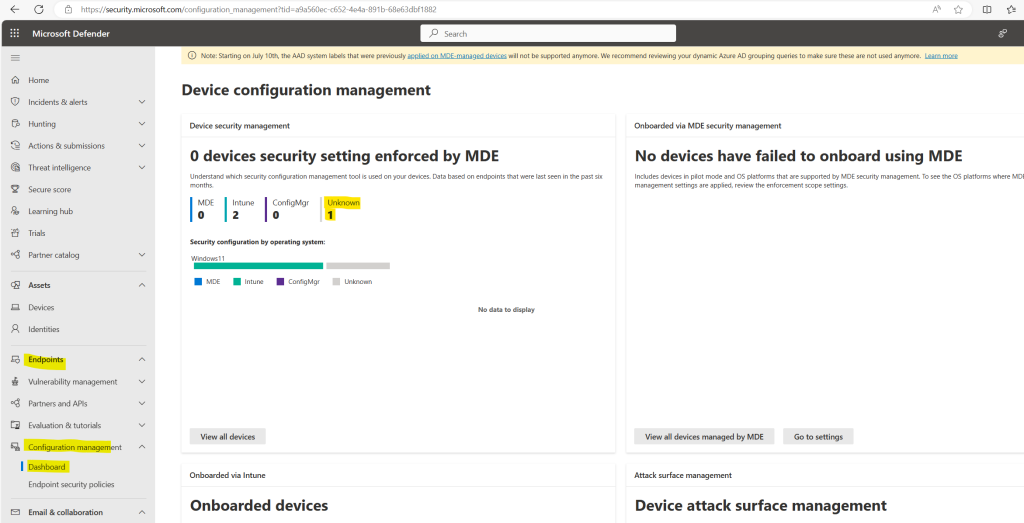
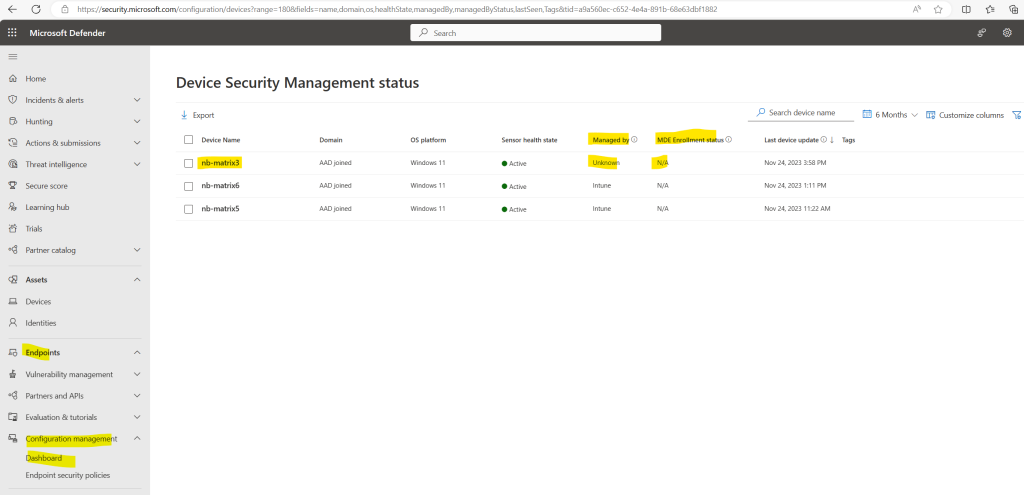
A while later the Dashboard shows that one devices security settings are enforced by MDE. This must be my lab device named nb-matrix3 on which I was previously executing the onboard script locally.
When clicking on View all devices shown in the screenshot above, nb-matrix3 is still shown up with N/A for the MDE Enrollment status. So it seams it takes some time to reflect the status on all places within the portal.

Meanwhile the device is also shown up in Microsoft Intune and Managed by is now updated correctly to Microsoft Defender for Endpoint (MDE).
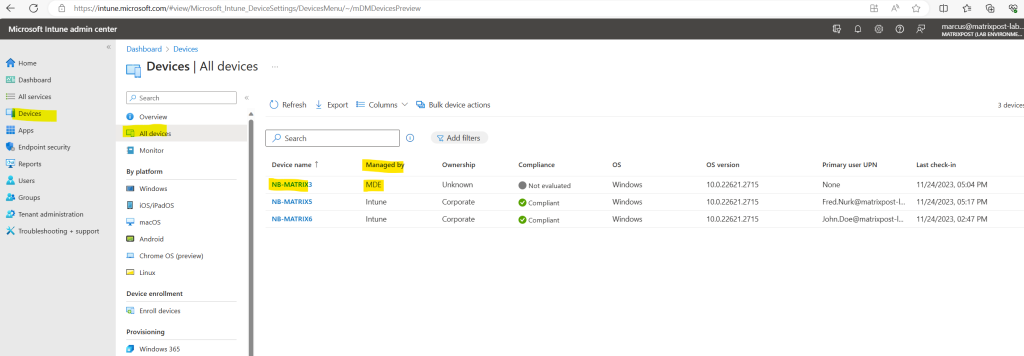
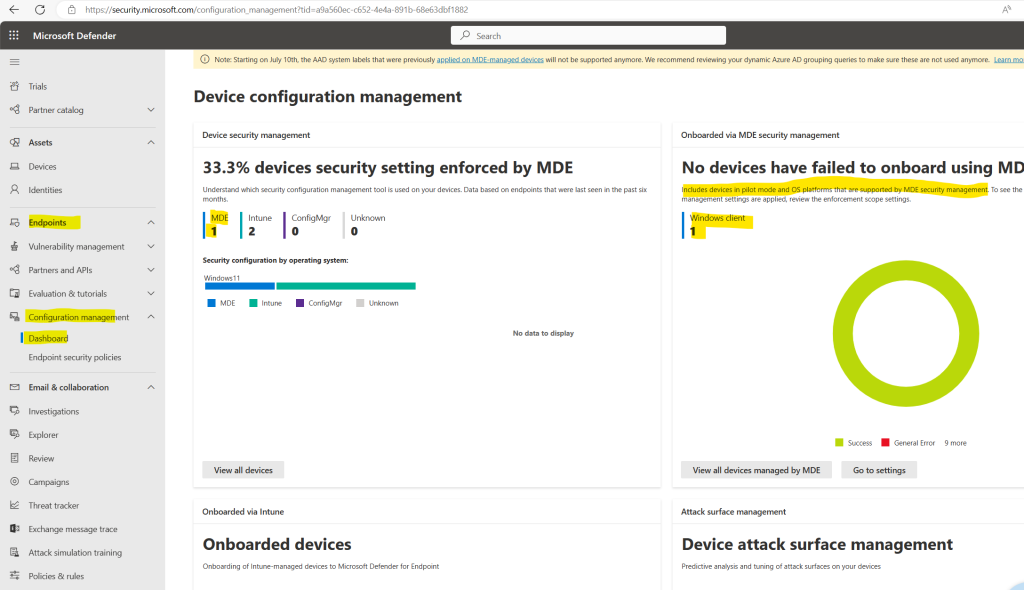
And also but about 2h later after executing the script, the nb-matrix3 device is finally also shown up in the Defender Portal correctly with Managed by set to MDE and for the MDE Enrollment status is shown Success.
As already mentioned further above, the MDE Enrollment status can be a little bit confusing, it is just used for devices they were enrolled directly to MDE by using the MDE security configuration management we did right now for the nb-matrix3 device.
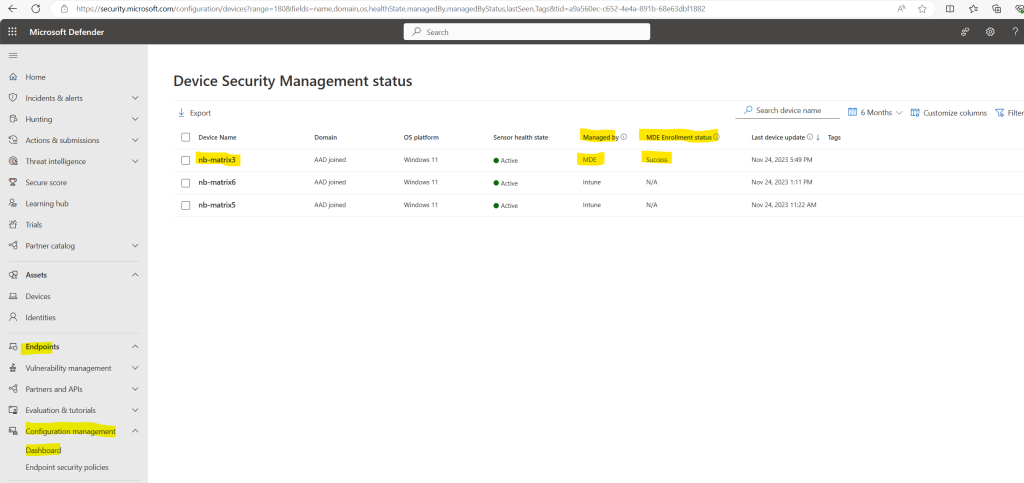
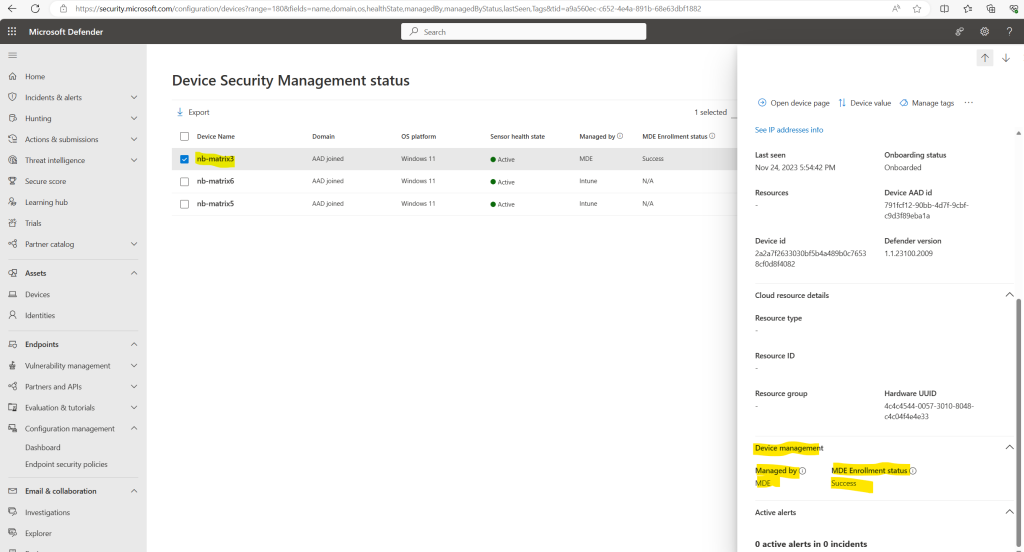
Verify the device is onboarded successfully to Microsoft Defender for Endpoint
When you add a device to the Microsoft Defender for Endpoint service for management, this is also called onboarding devices. Onboarding allows devices to report signals about their health status to the service.
Making sure, or verifying, that a device has been added to the service successfully is a critical step in the entire deployment process. It assures that all the devices expected are being managed.
To test if a device is successfully onboarded, you can use either a PowerShell script or the notorious EICAR Anti-Virus Test File.
By using a PowerShell Script
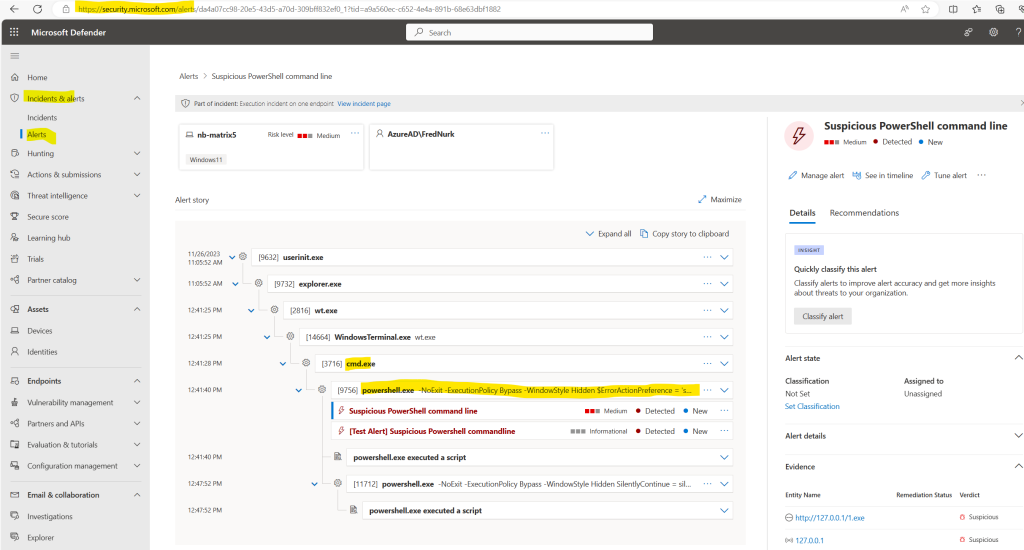
Run the following PowerShell script on a newly onboarded device to verify that it’s properly reporting to the Defender for Endpoint service. This PowerShell command line should be classified as suspicious by Microsoft Defender for Endpoint.
Open an elevated command-line prompt on the device and run the script.
At the prompt, copy and run the following command:
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference = 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('http://127.0.0.1/1.exe', 'C:\test-MDATP-test\invoice.exe');Start-Process 'C:\test-MDATP-test\invoice.exe'The Command Prompt window closes automatically. If successful, a new alert appears in the portal for the onboarded device in about 10 minutes.
In my case this took also about 10 minutes to show up in the alerts of Microsoft Defender for Endpoint.
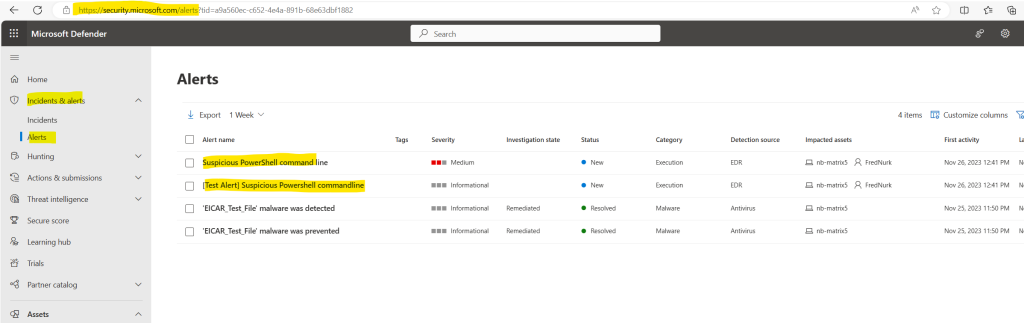
As you can see here I was using an elevated Window Terminal session (WindowsTerminal.exe) and then opened a Command Prompt session (cmd.exe) within to execute the PowerShell command line.
By using the EICAR Anti-Virus Test File
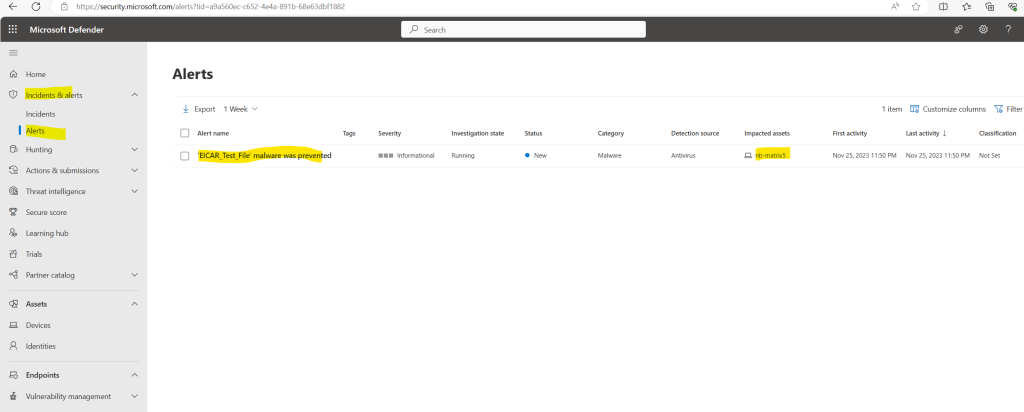
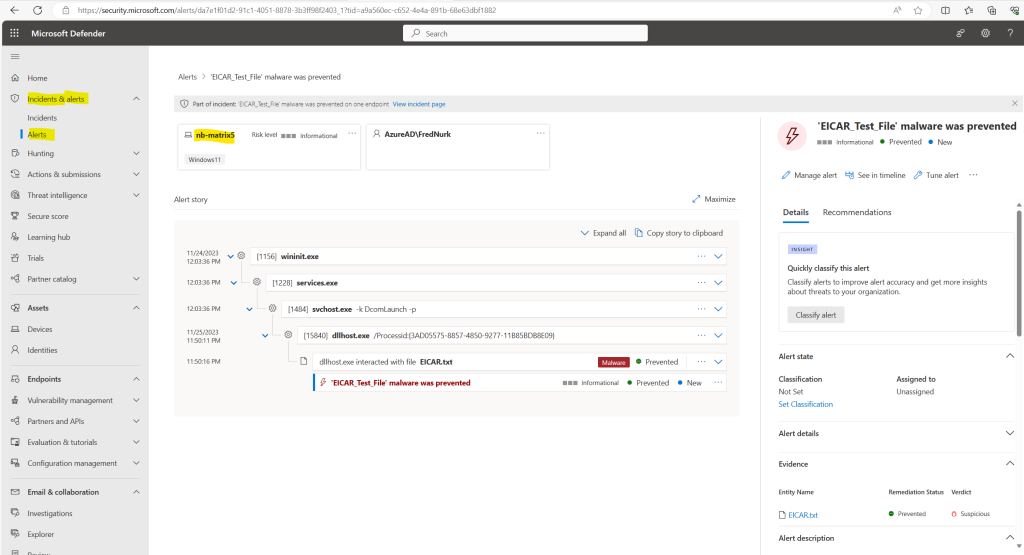
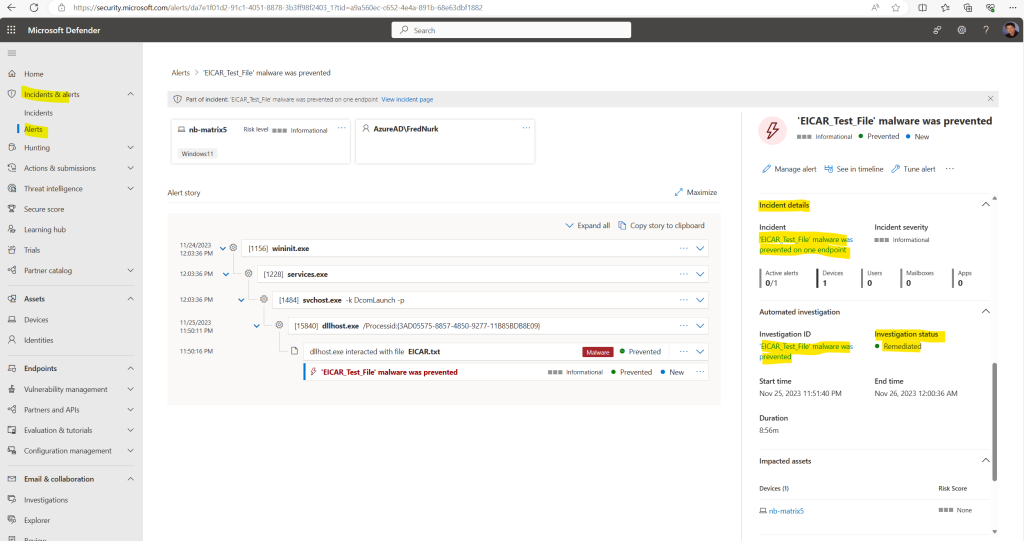
To perform this test create a text file and paste the EICAR line into, then save the file as an executable file to your endpoint’s local drive. You will receive a test endpoint notification and an alert in the Microsoft Defender portal.
EICAR test file
https://en.wikipedia.org/wiki/EICAR_test_fileDownload file (string)
https://www.eicar.org/download-anti-malware-testfile/
In my case the alert is immediately shown up in the Microsoft Defender portal.
Troubleshoot Microsoft Defender for Endpoint onboarding issues
You might need to troubleshoot the Microsoft Defender for Endpoint onboarding process if you encounter issues.
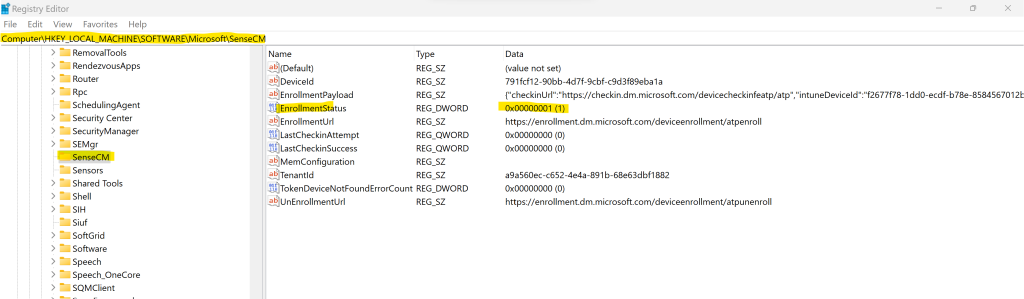
The enrollment status to Microsoft Defender for Endpoint you can also check on the device directly by using the following registry setting.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SenseCM\EnrollmentStatus
EnrollmentStatus 1 -> Device is enrolled to AAD and/or Microsoft Endpoint Manager (MEM)
EnrollmentStatus 3 -> Device is managed by MDM Agent (like Intune)
Troubleshoot onboarding issues related to Security Management for Microsoft Defender for Endpoint
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/troubleshoot-security-config-mgt?view=o365-worldwide#general-troubleshooting
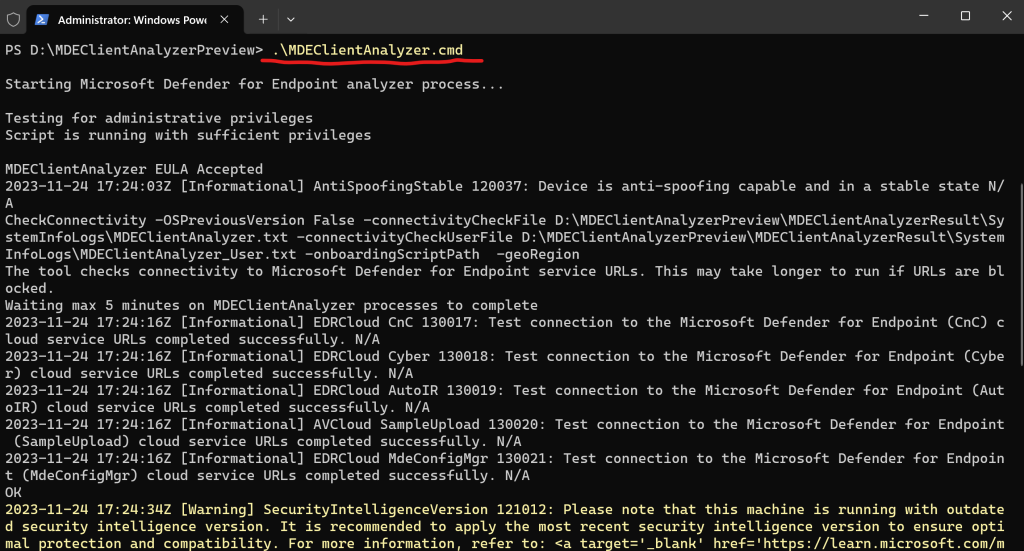
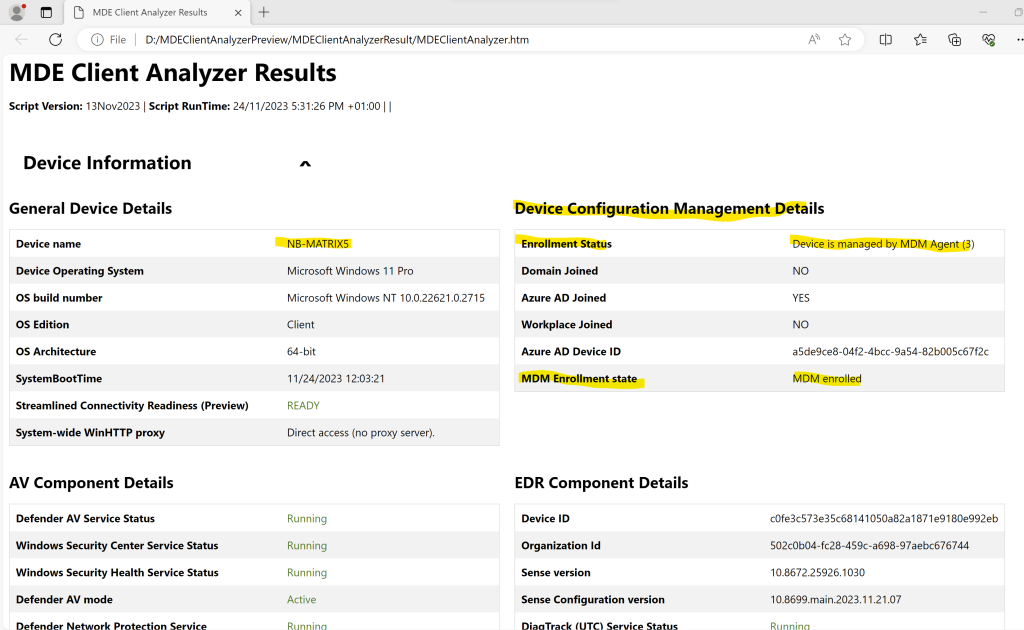
You can also run the client analyzer on the device in case of Windows.
Run the client analyzer on Windows
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/run-analyzer-windowsDownload the MDE Client Analyzer tool or Beta MDE Client Analyzer tool to the Windows device you want to investigate.
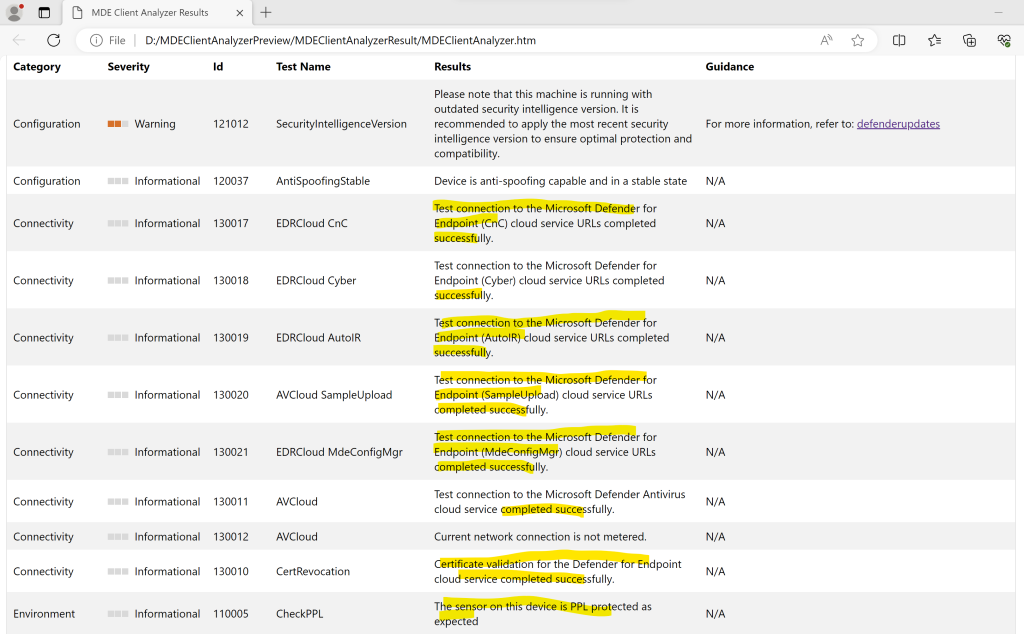
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/troubleshoot-onboarding
Links
What is Microsoft Defender for Endpoint?
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpointTroubleshoot Microsoft Defender for Endpoint onboarding issues
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/troubleshoot-onboarding
Tags In
Related Posts
Follow me on LinkedIn


