Upgrade Windows Server 2016 Domain Controllers and AD Schema to Windows Server 2019 | Raise Active Directory domain and forest functional levels
To update a domain controller, best practice is to install a server with the newer version of Windows Server and promote it to a domain controller, then demote the older domain controller.
Another way is to do an in-place upgrade from Windows Server to a newer version.
Below I will go through the separate steps to upgrade the domain controllers by using the best practices method.
First I will join the new Windows Server 2019 as a normal member server to the existing Windows Server 2016 Active Directory domain.
After that, I will adding the Active Directory Domain Services (ADDS) role.
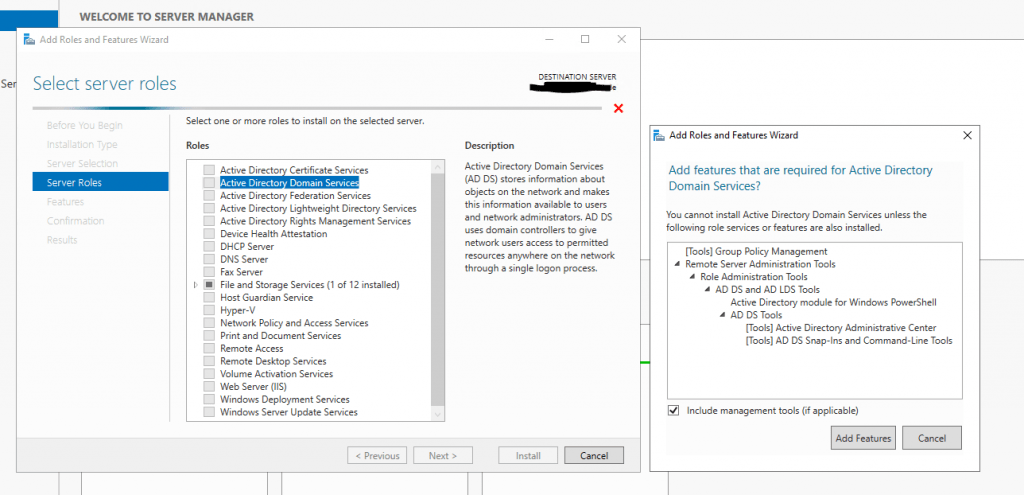
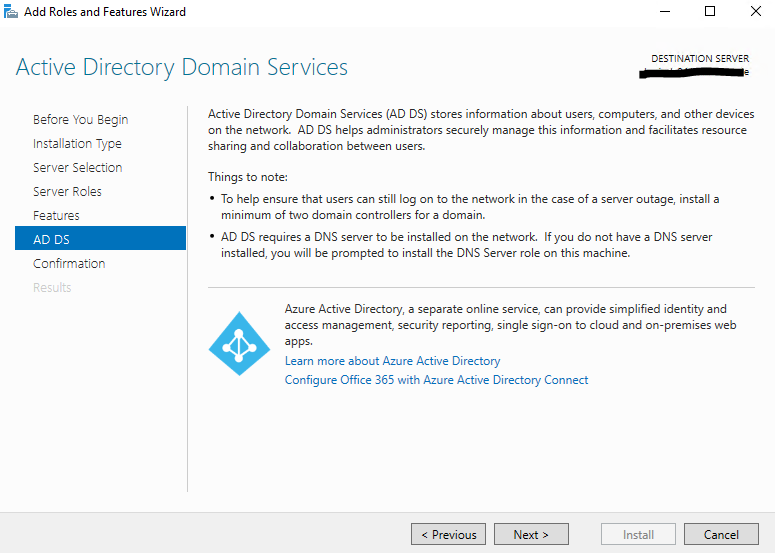
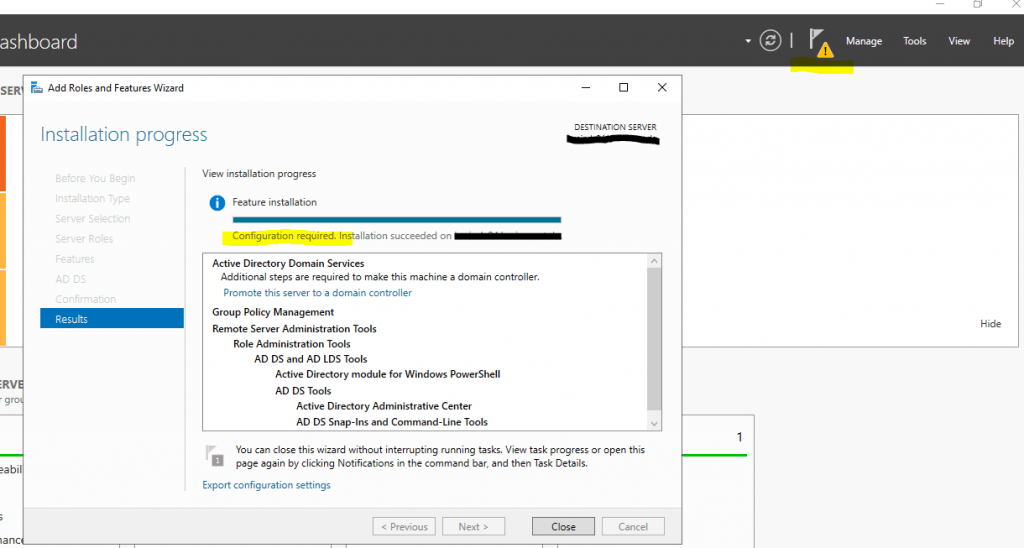
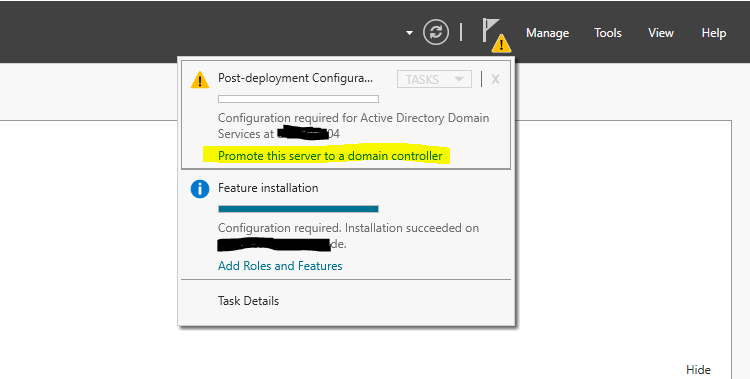
After the features where installed successfully, we need to promote the server to a domain controller. Therefore click on the warning icon on the right top of the server manager and on the link Promote this server to a domain controller.
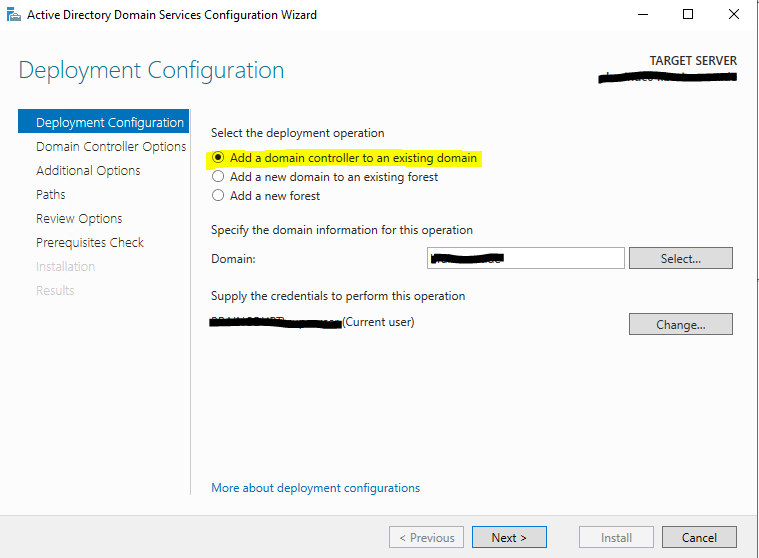
We want to add this domain controller to our existing domain.
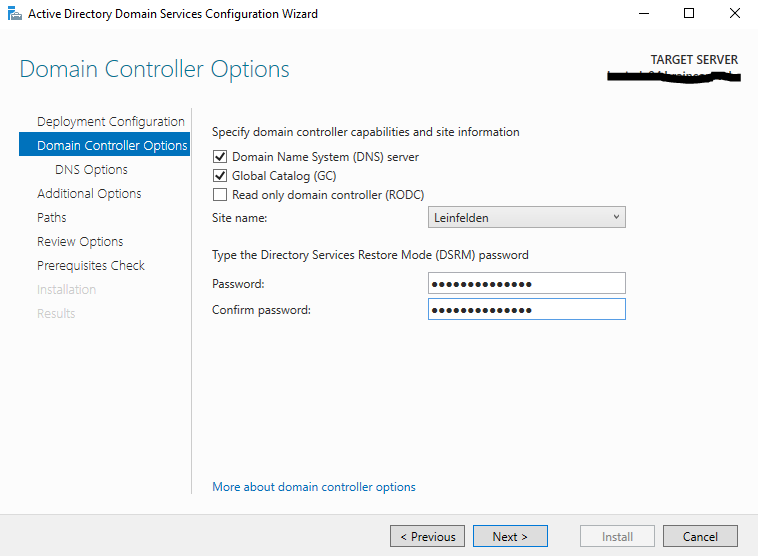
In the next step we keep the default settings to setup a DNS server and Global Catalog on the new domain controller, further we need to provide a Directory Sevices Restore Mode (DSRM) password in case you need to repair or recover the Active Directory database.
You can also reset the password later as described in the following article.
How to reset the Directory Services Restore Mode administrator account password in Windows Server
https://docs.microsoft.com/en-us/troubleshoot/windows-server/identity/reset-directory-services-restore-mode-admin-pwd
We will replicate from any domain controller to the new one.
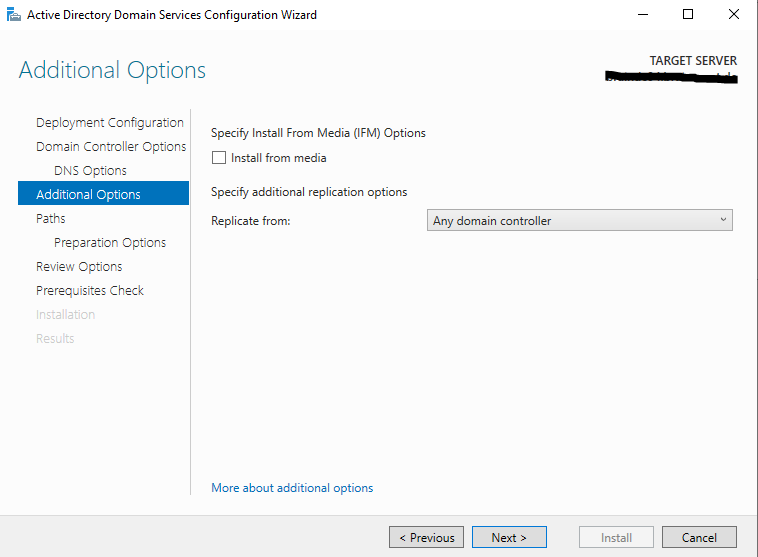
Here you can specify the location of the AD DS database, log files and SYSVOL, I will use the default locations.
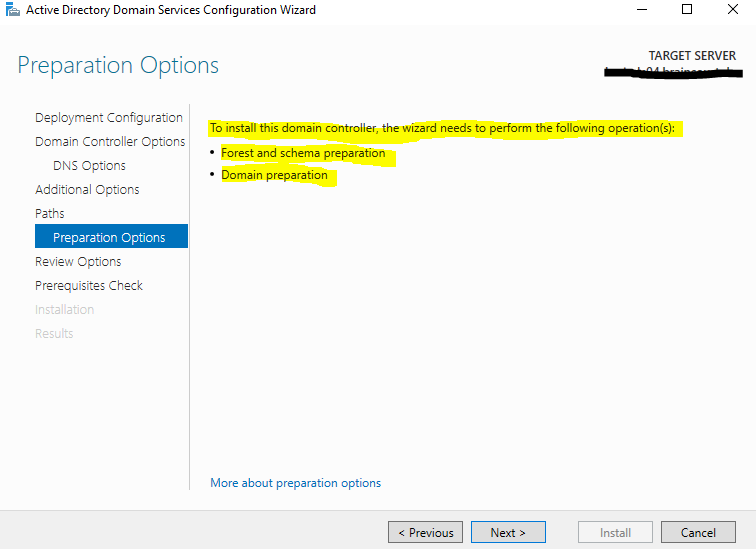
The existing domain is on the AD Schema version Windows Server 2016 (87), so for promoting this Windows Server 2019 domain controller, the existing Forest and Domain Schema must be prepared for the new version from Windows Server 2019 (88).
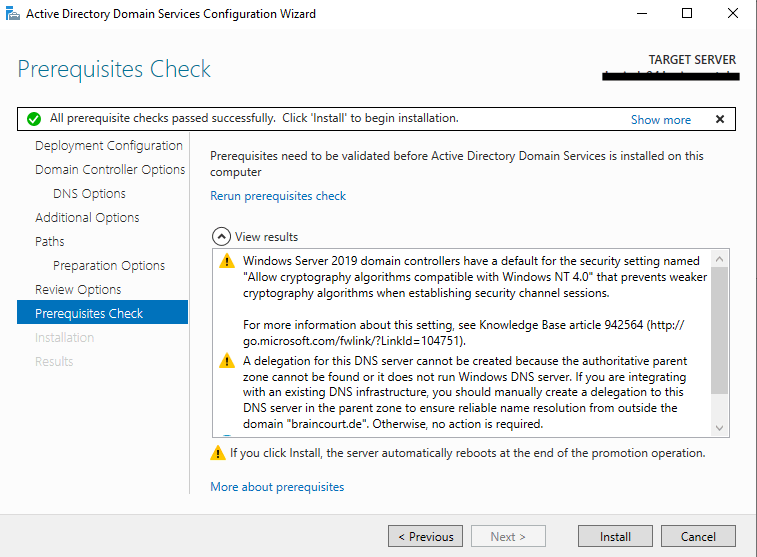
Finally we can click on Install to promote the server to a DC.
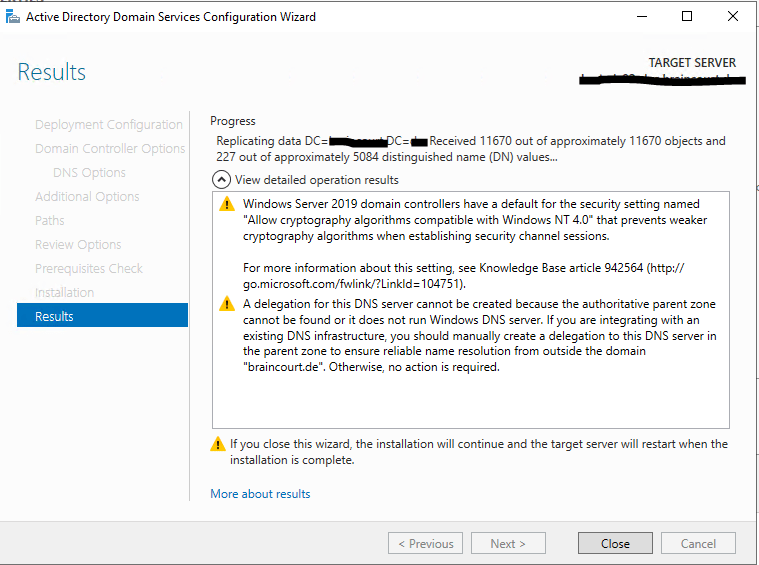
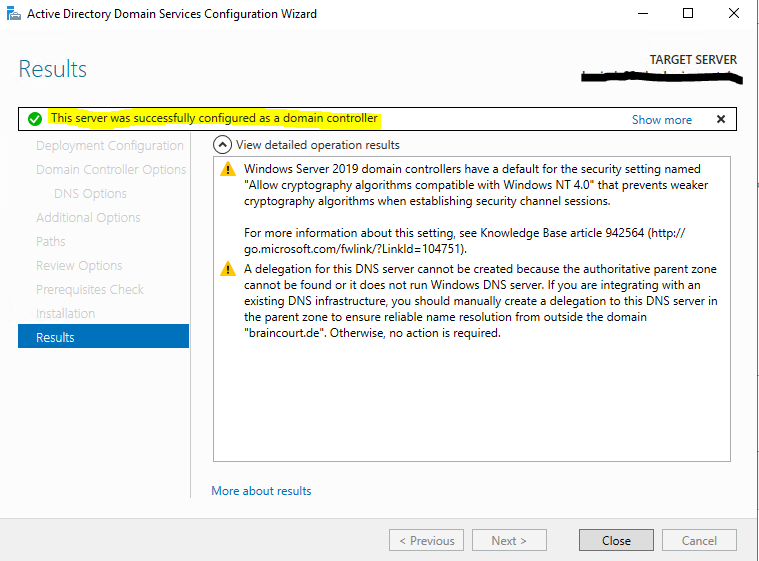
The server is now successfully configured as a domain controller and will finally restart to complete the promotion.
Now we can transfer the five Flexible Single Master Operations (FSMO) roles to our new Windows Server 2019 domain controller.
PDC Emulator (Primary Domain Controller)
RID Master – (Relative ID)
Infrastructure Master
Schema Master
Domain Naming MasterSource: https://en.wikipedia.org/wiki/Flexible_single_master_operation
Therefore you can use
- Active Directory Users and Computers console
- Command Prompt
- PowerShell (since 2008 R2)
Using PowerShell
Move-ADDirectoryServerOperationMasterRole -Identity <destination DC> -OperationMasterRole SchemaMaster,RIDMaster,InfrastructureMaster,DomainNamingMaster,PDCEmulator
Instead naming all roles you can also use the command with the numbers of the roles
PDCEmulator -> 0
RIDMaster -> 1
InfrastructureMaster -> 2
SchemaMaster -> 3
DomainNamingMaster -> 4
Move-ADDirectoryServerOperationMasterRole -Identity <destination DC> -OperationMasterRole 0,1,2,3,4
That command works only if the source domain controller is online, in case you cannot move the roles online, you can use the same command with the force parameter as follow:
Move-ADDirectoryServerOperationMasterRole -Identity <destination DC> -OperationMasterRole SchemaMaster,RIDMaster,InfrastructureMaster,DomainNamingMaster,PDCEmulator -Force
List the domain controller which hosts the FSMO roles
Get-ADForest | select SchemaMaster,DomainNamingMaster
Get-ADDomain | select PDCEmulator,RIDMaster,Infrastructuremaster
How to find the current Schema Version
Get-ADObject (Get-ADRootDSE).schemaNamingContext -Property objectVersion
Get-ItemProperty ‘AD:CN=Schema,CN=Configuration,DC=contoso,DC=local’ -Name objectVersion
dsquery * “cn=schema,cn=configuration,dc=contoso,dc=local” -scope base -attr object Version
Use ADSIEdit.msc or LDP.exe to navigate to:
CN=Schema,CN=Configuration,DC=contoso,DC=local.
right click on it and review objectVersion attribute.
Source: https://docs.microsoft.com/en-us/troubleshoot/windows-server/identity/find-current-schema-version
Windows Server 2000 -> 13
Windows Server 2003 -> 30
Windows Server 2003 R2 -> 31
Windows Server 2008 -> 44
Windows Server 2008 R2 -> 47
Windows Server 2012 -> 56
Windows Server 2012 R2 -> 69
Windows Server 2016 -> 87
Windows Server 2019 -> 88
Windows Server 2022 -> 88 (no upgrade of the schema version)
Demote old Domain Controller
Now we can demote the old domain controller.
Demoting Domain Controllers and Domains
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/deploy/demoting-domain-controllers-and-domains–level-200-
In the server manager on the old domain controller click on Manage -> Remove Roles and Features
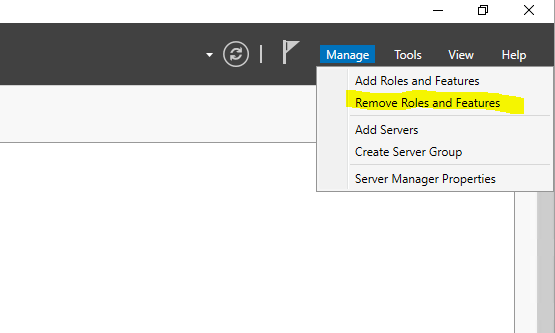
Clear the Active Directory Domain Services check box to remove the features in order to be able to demote the domain controller.
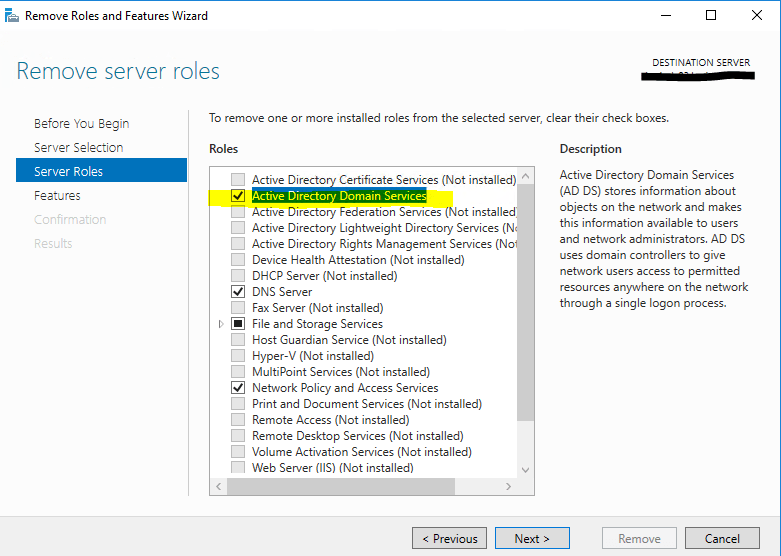
If the server is currently a domain controller, this does not remove the AD DS role and instead switches to a Validation Results dialog with the offer to demote. Otherwise, it removes the binaries like any other role feature.
- Do not remove any other AD DS-related roles or features – such as DNS, GPMC, or the RSAT tools – if you intend to promote the domain controller again immediately. Removing additional roles and feature increases the time to re-promote, as Server Manager reinstalls these features when you reinstall the role.
- Remove unneeded AD DS roles and features at your own discretion if you intend to demote the domain controller permanently. This requires clearing the check boxes for those roles and features.The full list of AD DS-related roles and features include:
- Active Directory Module for Windows PowerShell feature
- AD DS and AD LDS Tools feature
- Active Directory Administrative Center feature
- AD DS Snap-ins and Command-line Tools feature
- DNS Server
- Group Policy Management Console
The equivalent ADDSDeployment and ServerManager Windows PowerShell cmdlets are:
Uninstall-addsdomaincontroller Uninstall-windowsfeature
The validation process will inform you that it found problems on the server and that you first have to demote the domain controller in order to remove the features.
Therefore click on Demote this domain controller
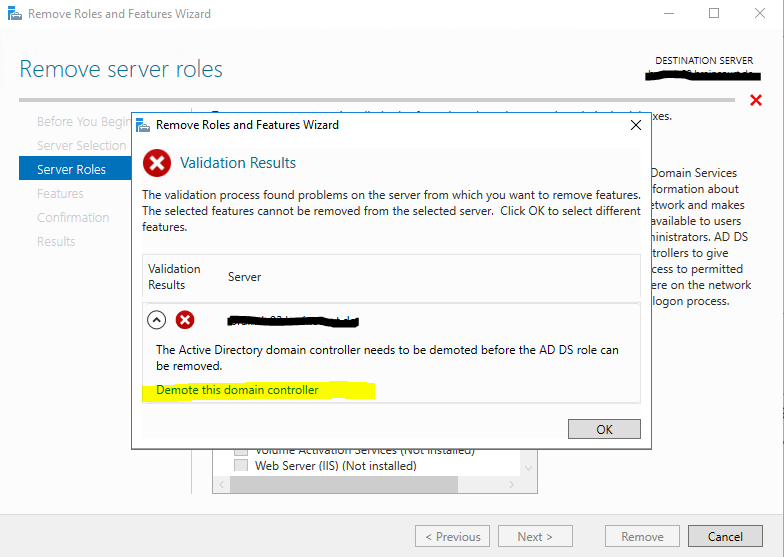
Don’t check the Force the removal of this domain controller checkbox!
This feature you will only need if the domain controller can’t be demoted the normal way.
If you check this, you will have to clean up the Active Directory Domain Controller server metadata by hand as shown in the following article from Microsoft.
Clean up Active Directory Domain Controller server metadata
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/deploy/ad-ds-metadata-cleanup
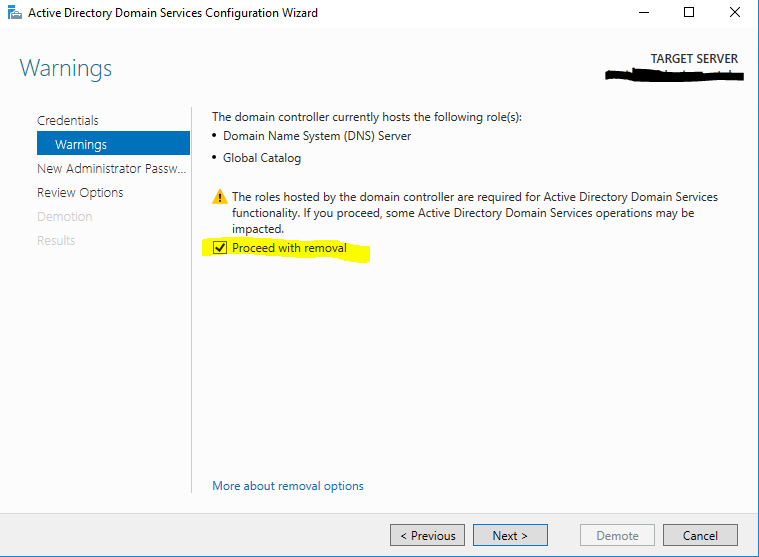
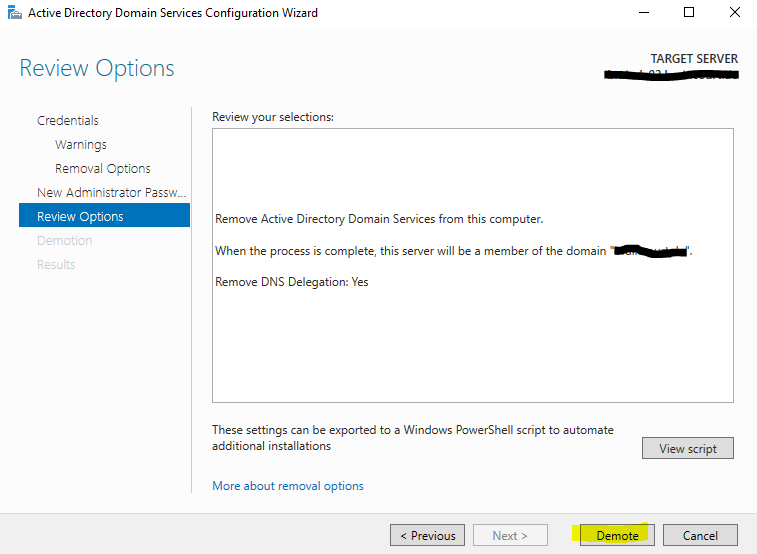
Check Proceed with removal
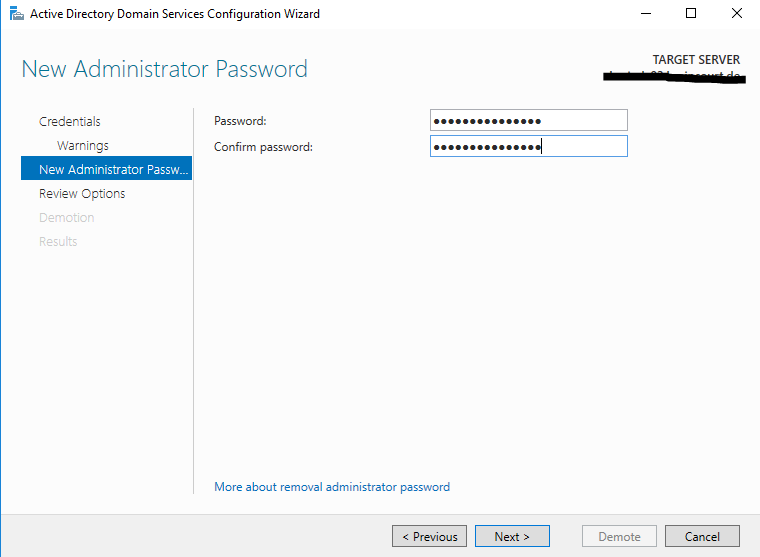
The next step is to set a password for the built-in local computer’s Administrator account, which will be created during demotion. DC’s doesn’t have a built-in local administrator account once promoted to a DC.
New Administrator Password
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/deploy/ad-ds-installation-and-removal-wizard-page-descriptions#BKMK_NewAdminPwdPage
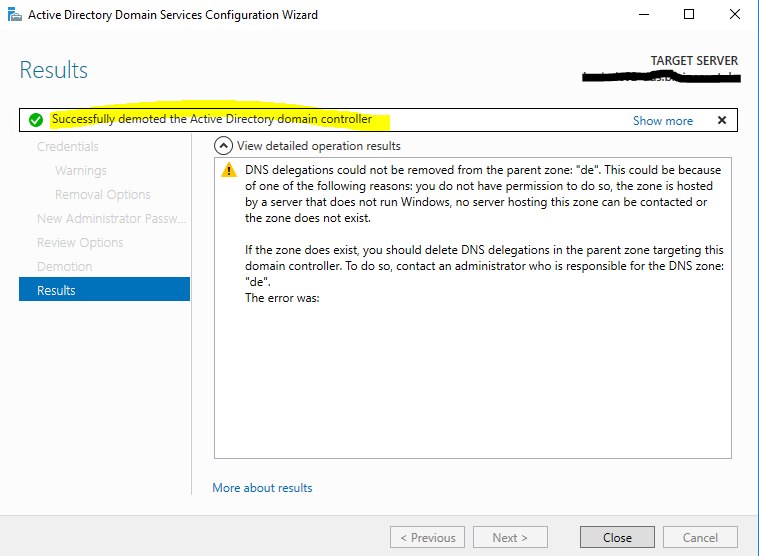
After that the server is a normal member server in your domain and will get restarted. In most cases you will remove it after that completely from the domain and network.
Raise Active Directory domain and forest functional levels
If all domain controllers running the newest Windows Server operating system version in your network, you can raise the domain and forest level.
Functional levels are an extension of the mixed mode and the native mode concepts that were introduced in Microsoft Windows 2000 Server to activate new Active Directory features. Some additional Active Directory features are available when all the domain controllers are running the newest Windows Server version in a domain or in a forest, and when the administrator activates the corresponding functional level in the domain or in the forest.
To activate the newest domain features, all the domain controllers must be running the newest Windows Server operating system version in the domain. If this requirement is met, the administrator can raise the domain functional level.
The most common method to enable the domain and forest functional levels is to use the graphical user interface (GUI) administration tools that are documented in the TechNet article about Windows Server 2003 Active Directory functional levels. This article discusses Windows Server 2003. However, the steps are the same in the newer the operating system versions. Additionally, the functional level can be manually configured or can be configured by using Windows PowerShell scripts. For more information about how to manually configure the functional level, see the “View and set the functional level” section.
For more information about how to use Windows PowerShell script to configure the functional level, view Raise the Forest Functional Level.
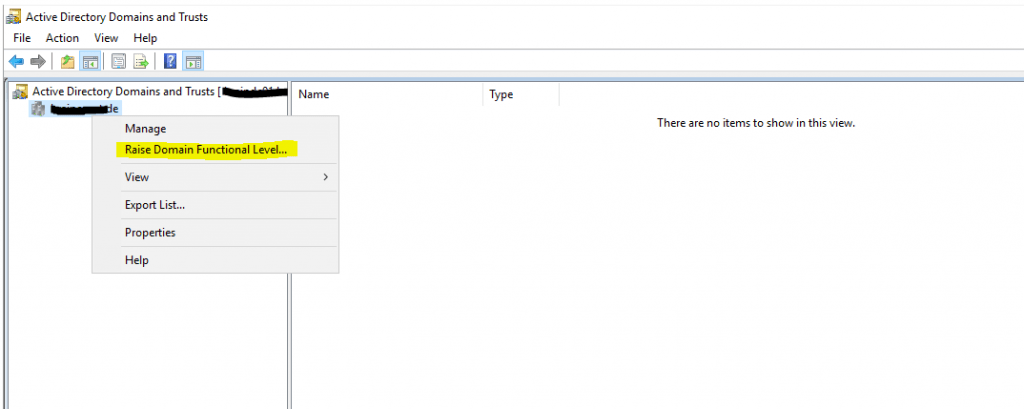
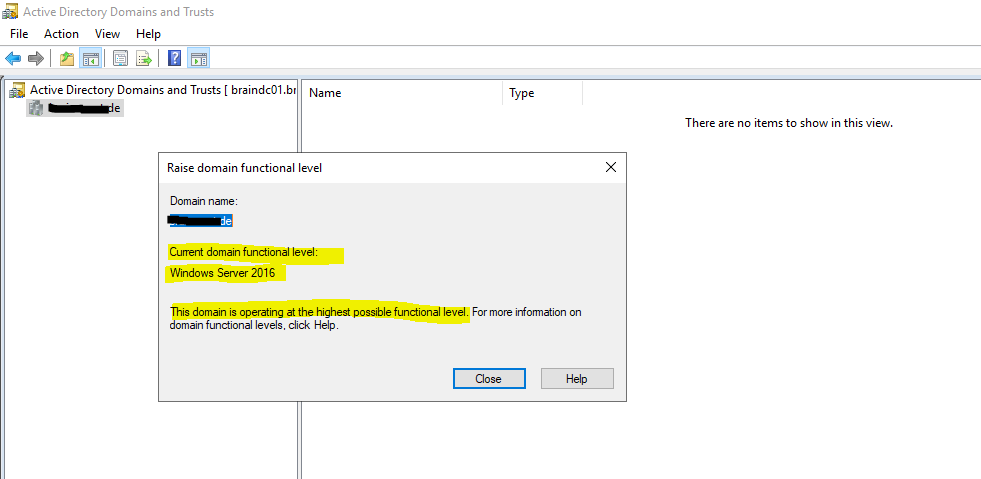
Raise Domain Functional Level, right click on your domain and select Raise Domain Functional Level …
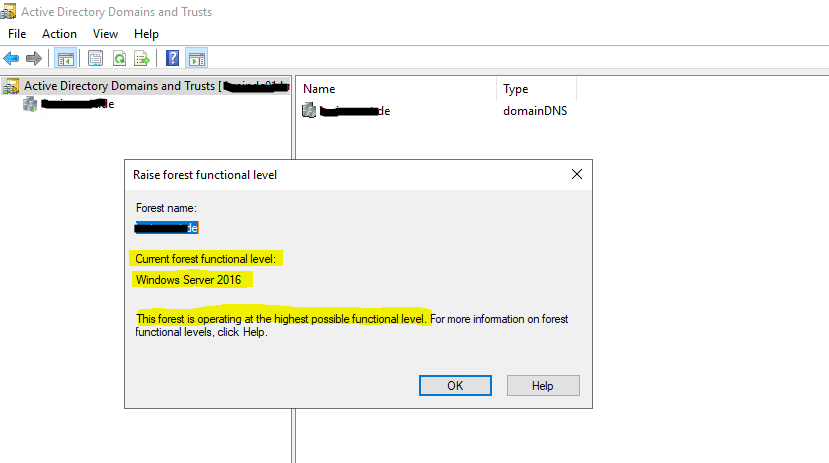
Raise Forest Functional Level, right click on Active Directory Domains and Trust and select Raise Forest Functional Level …
For Windows Server 2019 there is no new Forest Function Level (FFL) or Domain Function Level (DFL) when upgrading from Windows Server 2016 to 2019.
The latest level is Windows Server 2016.
Only the AD Schema is moved from version 87 in Windows Server 2016 to version 88 in Windows Server 2019. For Windows Server 2022 there is even no schema update.
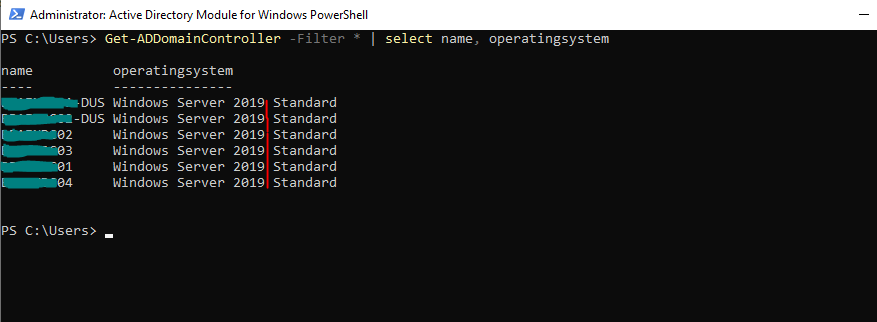
Get-ADDomainController -Filter * | select name, operatingsystem
Links
Upgrade Domain Controllers to Windows Server 2016
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/deploy/upgrade-domain-controllers
How to Add Windows Server 2022 as a Domain Controller
https://petri.com/windows-server-2022-as-a-domain-controller
Demoting Domain Controllers and Domains
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/deploy/demoting-domain-controllers-and-domains–level-200-
Clean up Active Directory Domain Controller server metadata
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/deploy/ad-ds-metadata-cleanup
AD DS Installation and Removal Wizard Page Descriptions
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/deploy/ad-ds-installation-and-removal-wizard-page-descriptions#BKMK_NewAdminPwdPage
How to raise Active Directory domain and forest functional levels
https://docs.microsoft.com/en-us/troubleshoot/windows-server/identity/raise-active-directory-domain-forest-functional-levels



