Set up a route-based Site-to-Site IPSec VPN Tunnel in Azure
In this post I want to show step by step how you can configure a Site-to-Site IPSec route based VPN Tunnel in Azure which will finally connect my Azure VNet with my on-premise lab network.
For the on-premise VPN device I will use here a pfSense appliance (virtual machine).
I already wrote a post in January 2020 about this topic shown below, but because some steps will now differ and also new features were added, I wanted to write a new updated version.
Configure your Virtual Network
We first need to create a gateway subnet within our virtual network which we want to connect finally to our on-premise network.
The virtual network gateway requires a specific subnet named GatewaySubnet. The gateway subnet is part of the IP address range for your virtual network and contains the IP addresses that the virtual network gateway resources and services use. Specify a gateway subnet that’s /27 or larger.
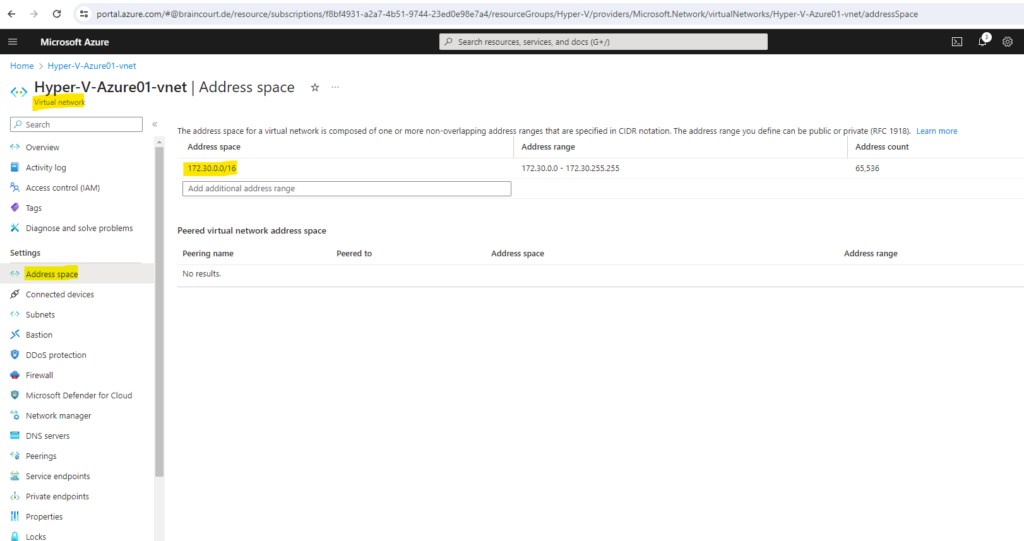
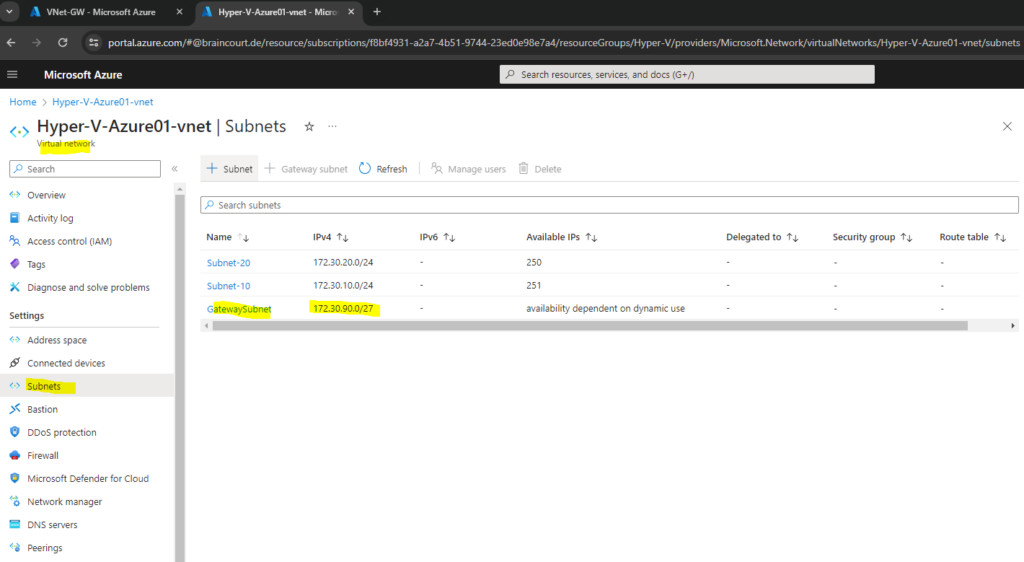
We can add the Gateway Subnet within the Subnets menu of our virtual network by clicking on the Gateway subnet link below.
Create and Configure a Virtual Network Gateway
Next we need to add a virtual network gateway.
SKU: From the dropdown list, select the gateway SKU that supports the features you want to use. See Gateway SKUs. In the portal, the SKUs available in the dropdown list depend on the VPN type you select. The Basic SKU can only be configured using Azure CLI or PowerShell. You can’t configure the Basic SKU in the Azure portal.
Select the generation you want to use. We recommend using a Generation2 SKU. For more information, see Gateway SKUs.
Virtual network: From the dropdown list, select the virtual network to which you want to add this gateway. If you can’t see the virtual network for which you want to create a gateway, make sure you selected the correct subscription and region in the previous settings.
Source: https://learn.microsoft.com/en-us/azure/vpn-gateway/tutorial-site-to-site-portal#create-the-gateway
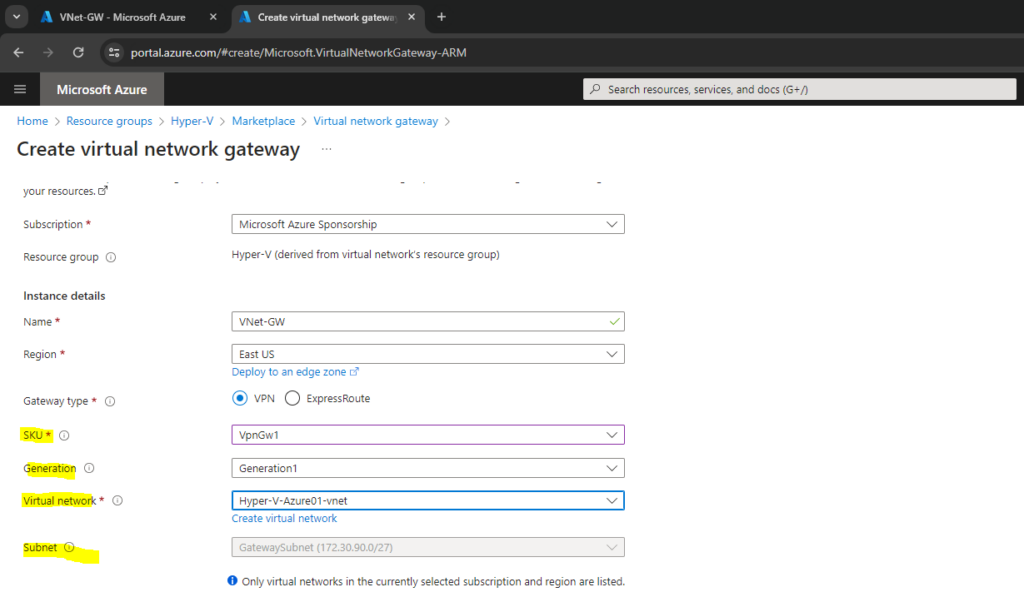
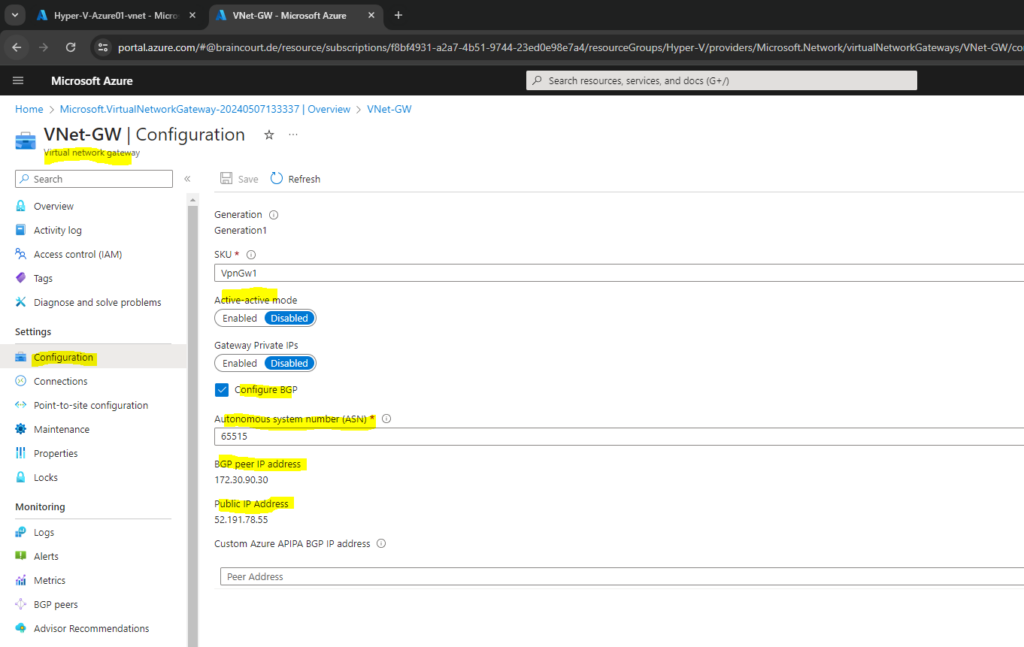
The Azure APIPA BGP IP address field below I will leave blank because my pfSense appliance in my on-premise network will not a APIPA BGP IP address.
The Azure APIPA BGP IP address field is optional. If your on-premises VPN devices use APIPA address for BGP, you must select an address from the Azure-reserved APIPA address range for VPN, which is from 169.254.21.0 to 169.254.22.255.
If you’re creating an active-active VPN gateway, the BGP section will show an additional Second Custom Azure APIPA BGP IP address. Each address you select must be unique and be in the allowed APIPA range (169.254.21.0 to 169.254.22.255). Active-active gateways also support multiple addresses for both Azure APIPA BGP IP address and Second Custom Azure APIPA BGP IP address. Additional inputs will only appear after you enter your first APIPA BGP IP address.
Source: https://learn.microsoft.com/en-us/azure/vpn-gateway/bgp-howto
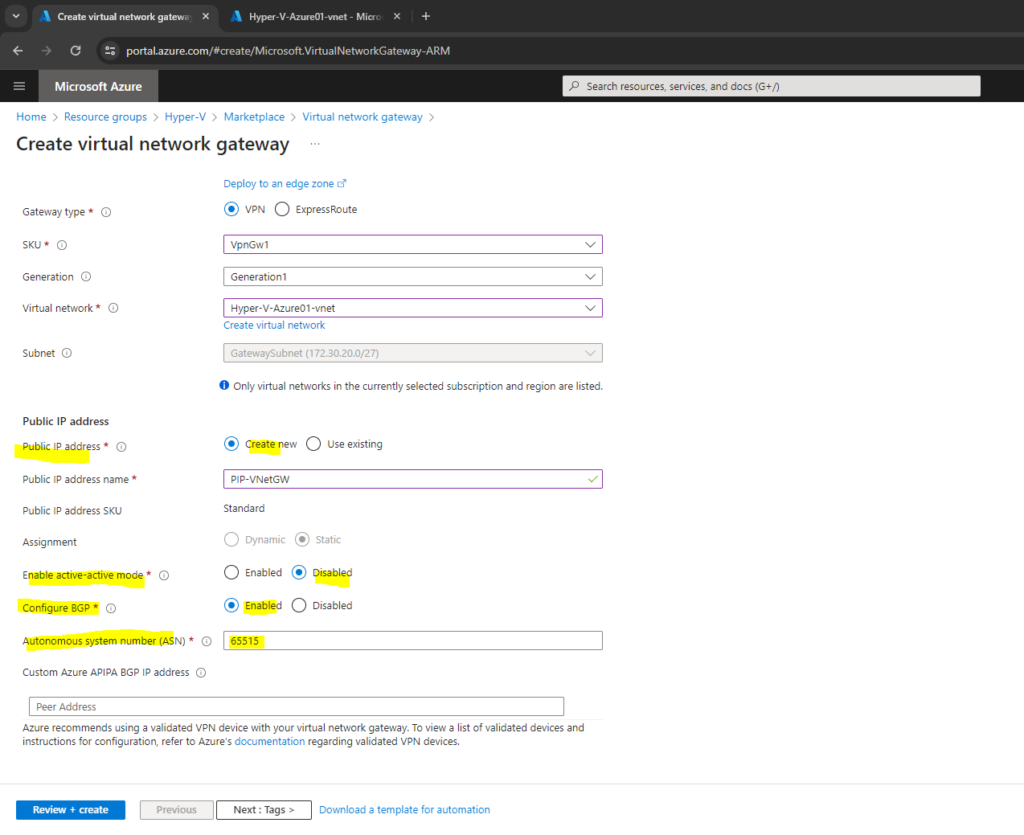
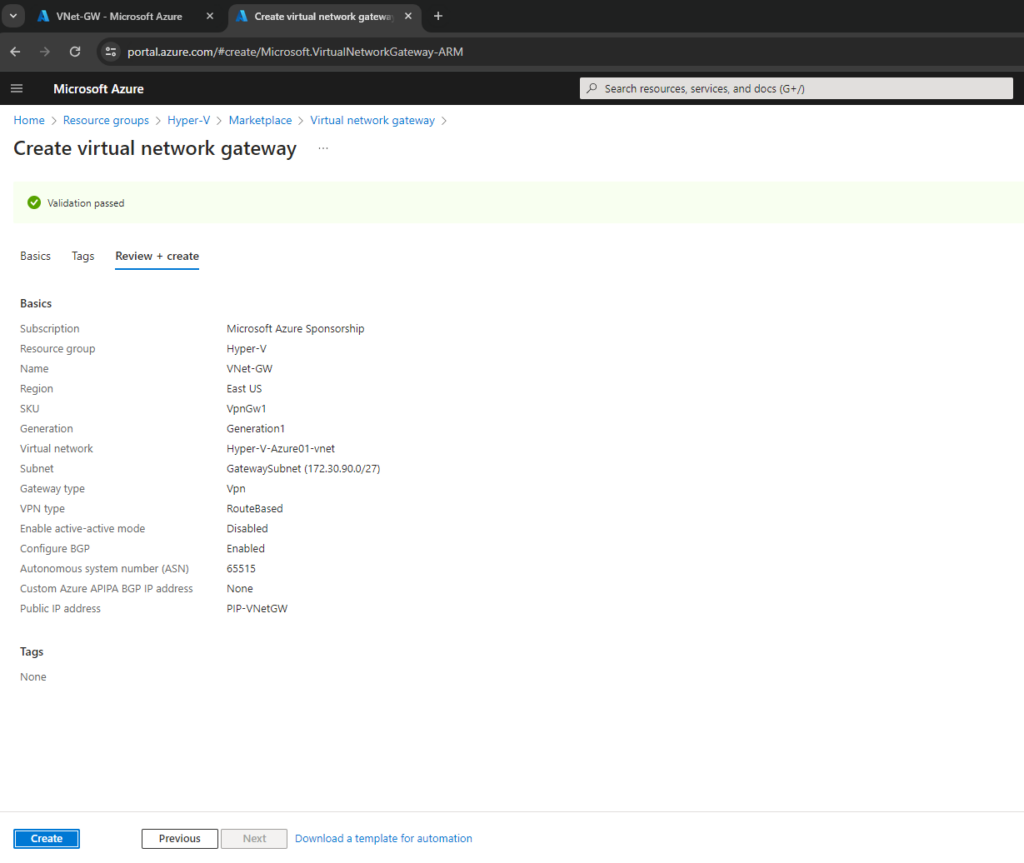
Creating a gateway can often take 45 minutes or more, depending on the selected gateway SKU.
Source: https://learn.microsoft.com/en-us/azure/vpn-gateway/tutorial-site-to-site-portal#VNetGateway
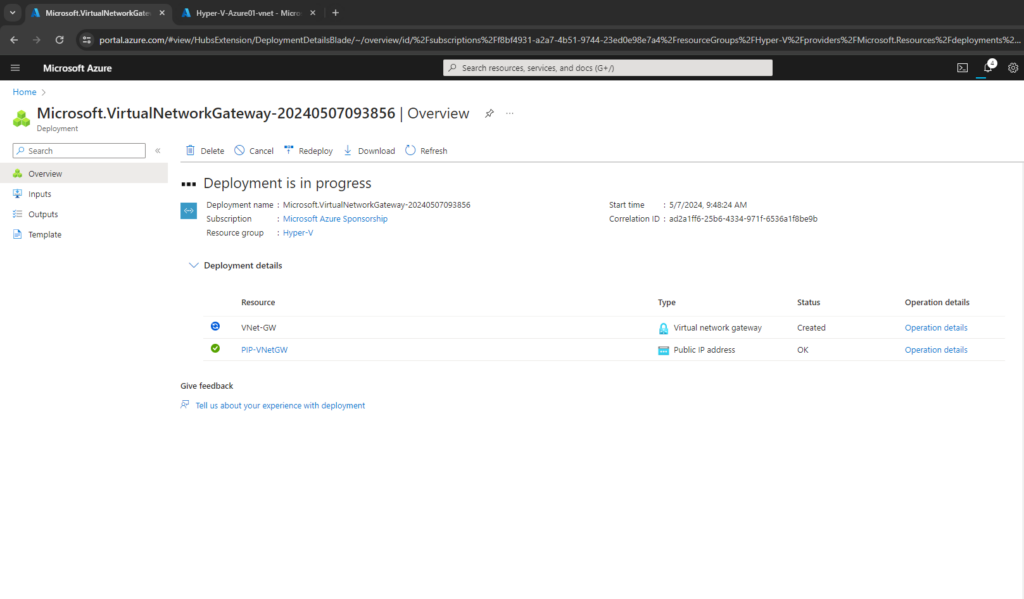
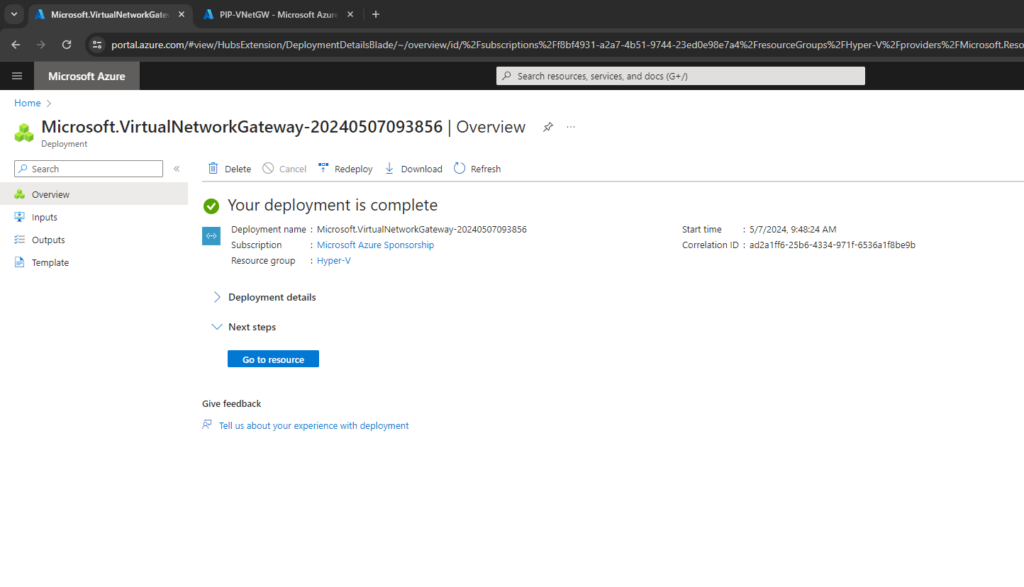
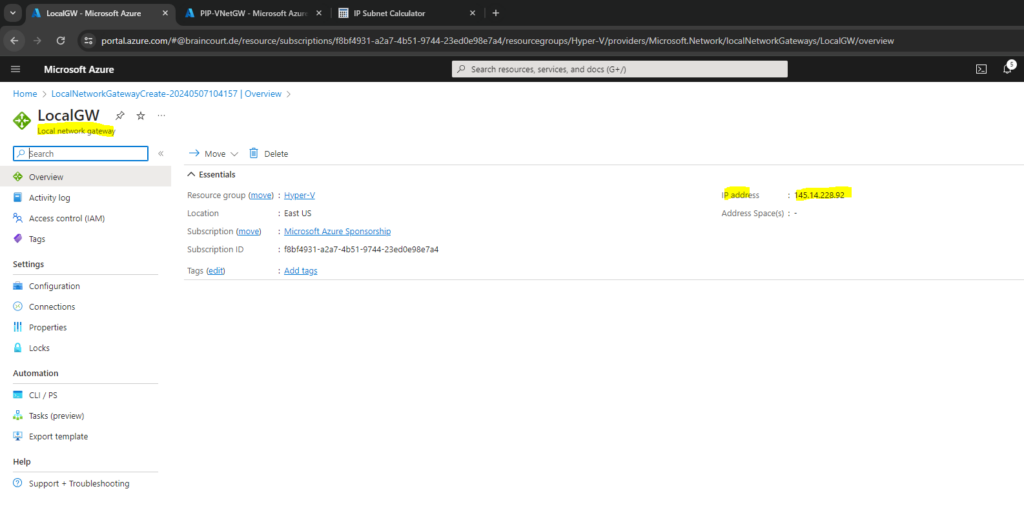
You can determine the gateway public IP address on the Overview page for your gateway.
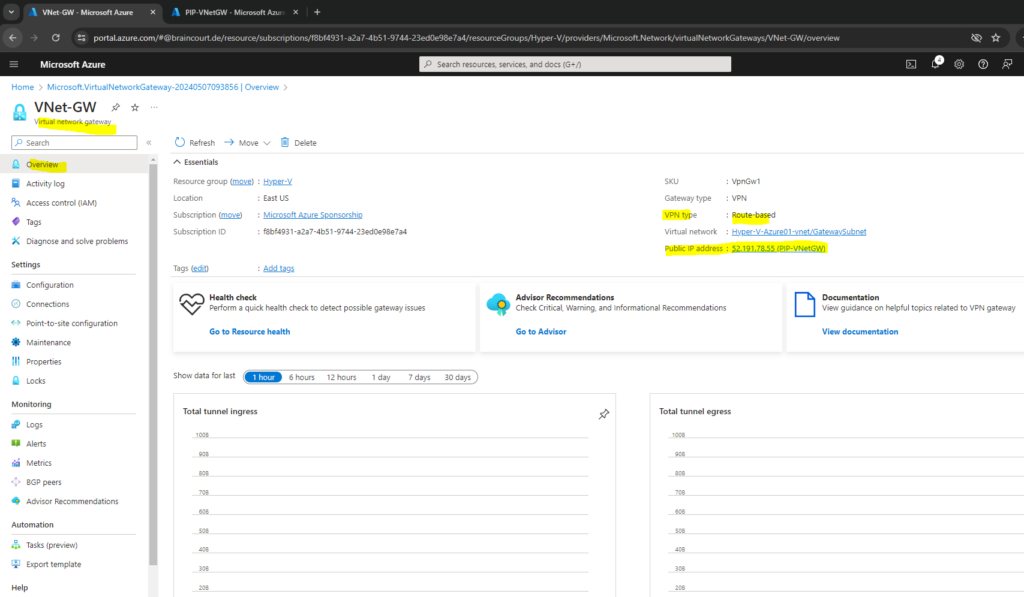
Once the gateway is created, you can obtain the BGP Peer IP addresses on the VPN gateway as shown below within the configuration section. These addresses are needed to configure your on-premises VPN devices to establish BGP sessions with the VPN gateway.
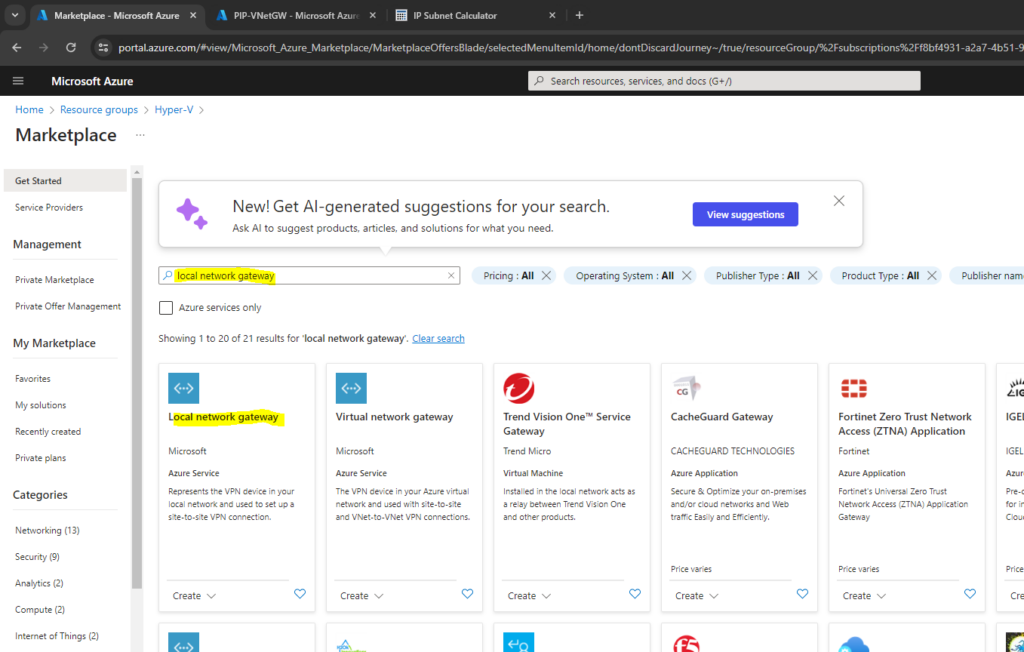
Create and Configure a Local Network Gateway
The local network gateway is a specific object that represents your on-premises location (the site) for routing purposes. You give the site a name by which Azure can refer to it, and then specify the IP address of the on-premises VPN device to which you create a connection.
Source: https://learn.microsoft.com/en-us/azure/vpn-gateway/tutorial-site-to-site-portal#LocalNetworkGateway
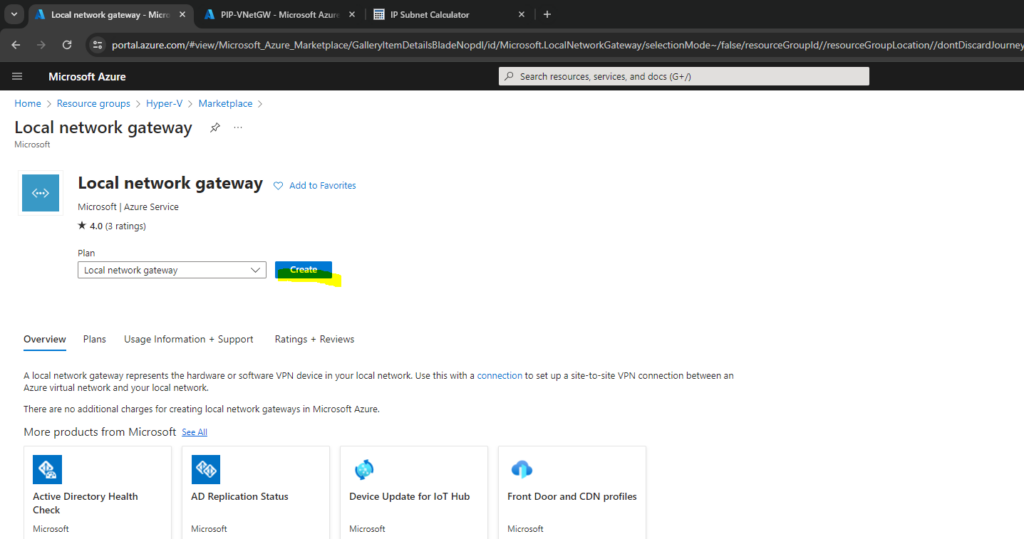
Because we previously configured for our virtual network gateway to use BGP, we do not need to enter an address space below and can leave this blank. Click on Next: Advanced to enable BGP on the local network gateway.
Address spaces: If BGP is enabled, no address space is required.
One or more IP address ranges (in CIDR notation) that define your local network’s address space. For example: 192.168.0.0/16. If you plan to use this local network gateway in a BGP-enabled connection, then the minimum prefix you need to declare is the host address of your BGP Peer IP address on your VPN device.
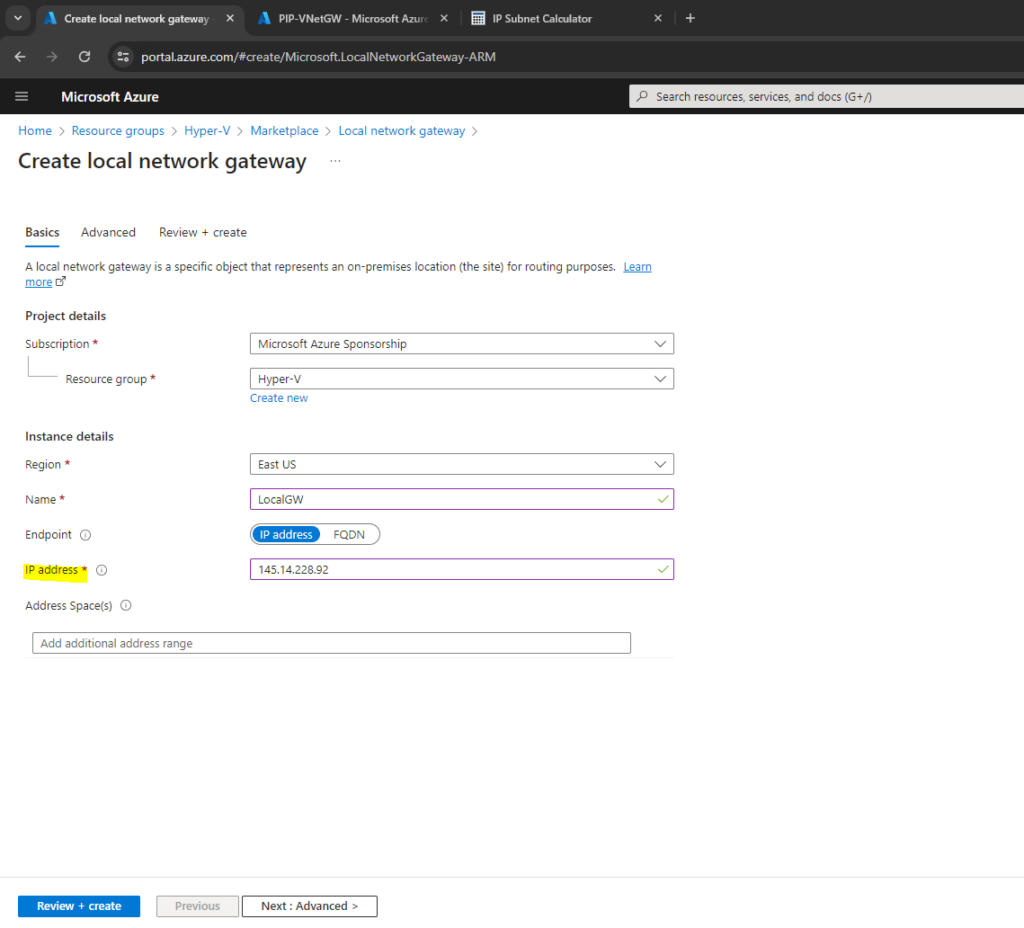
As mentioned, because we will use BGP to advertise the routes of our local network, we can leave the field for the address space(s) below blank.
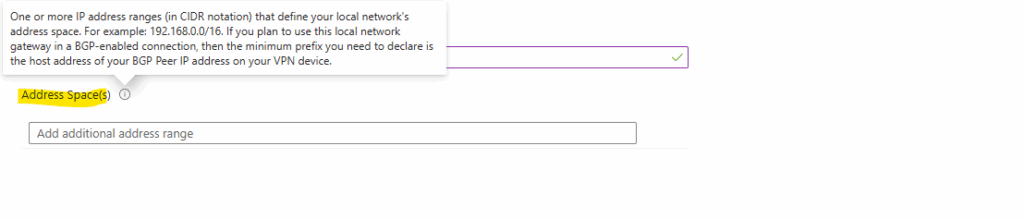
In case we do not want to use BGP and therefore want to define the networks/subnets we want to route through the tunnel by hand, we need to add here all on-premise local networks which should be routed through the tunnel with Azure.
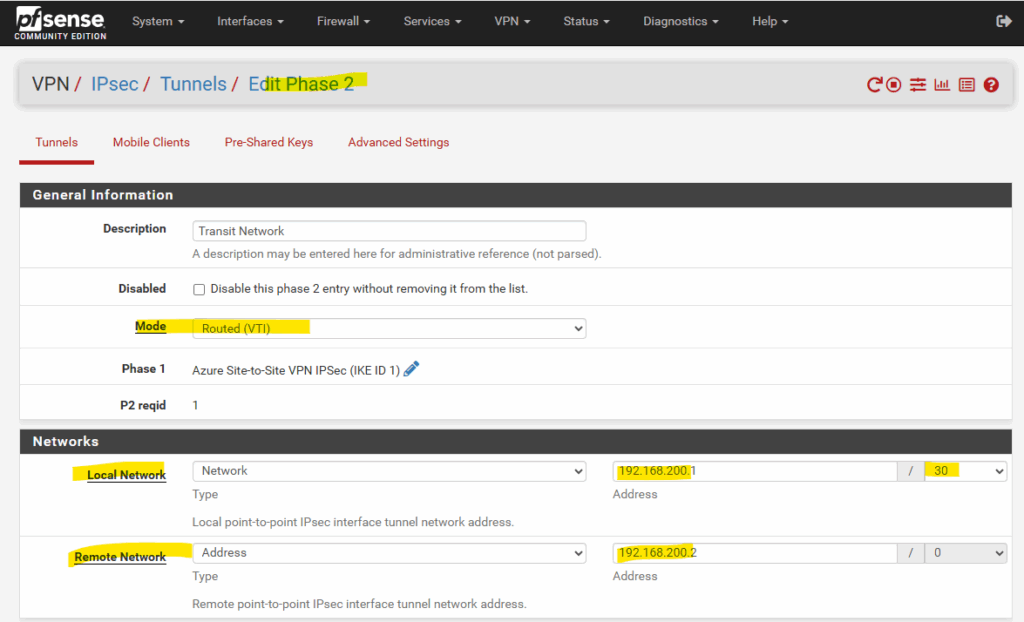
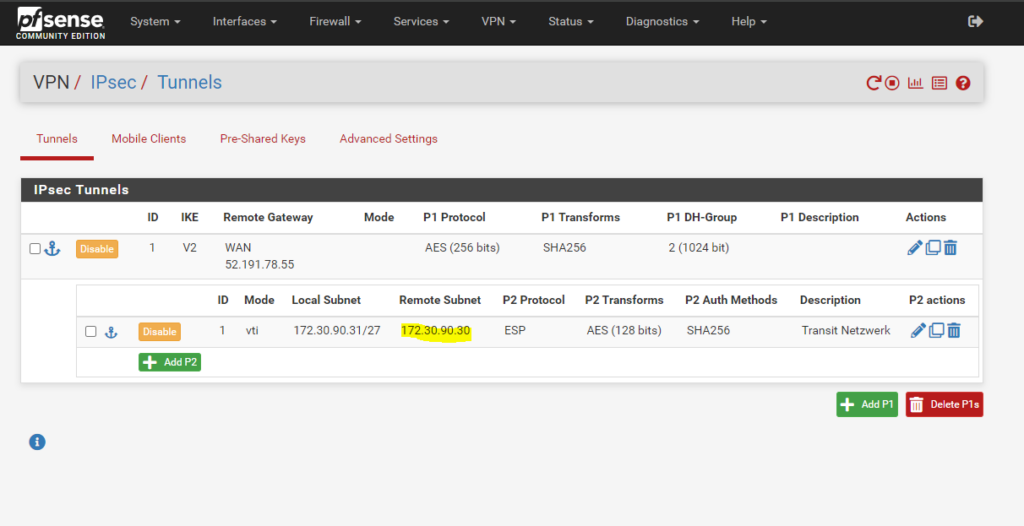
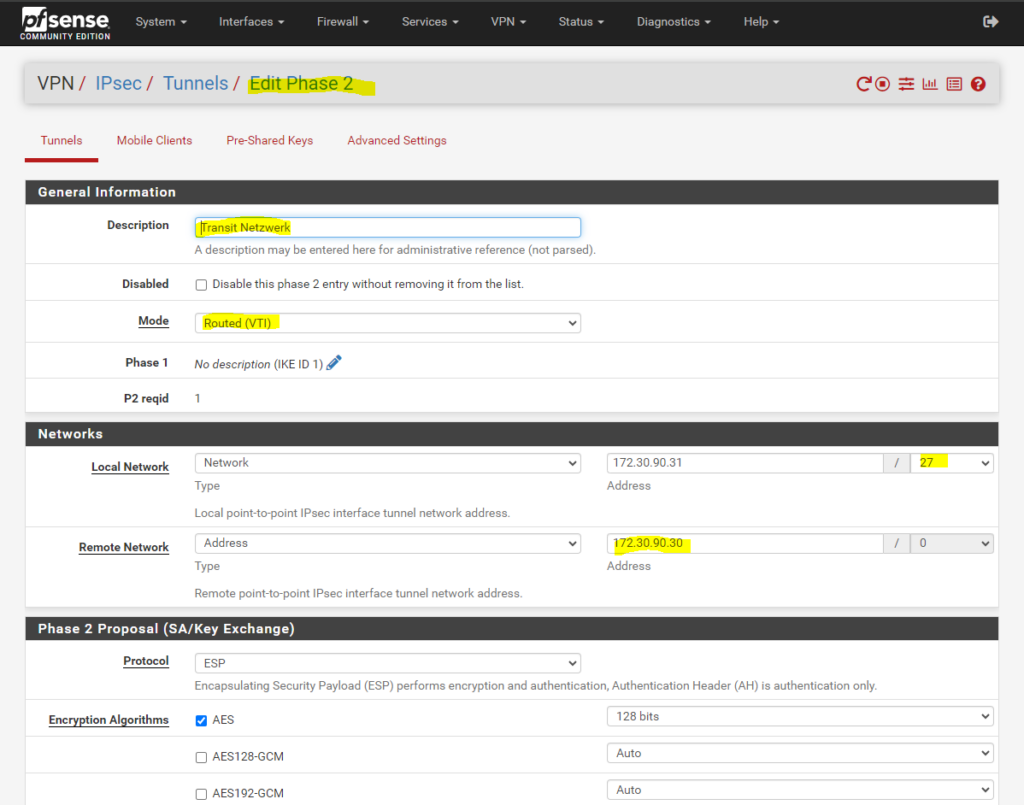
We also need to add here the transit network (IKEv2 phase 2 tunnel), configured on the local on-premise VPN device, through which the local networks and Azure networks will be routed.
For the transit network I will use below for example the network 192.168.200.0/30. This network will finally have two host addresses I can use for with 192.168.200.1 and 192.168.200.2 (192.168.200.0 is the network address and 192.168.200.3 the broadcast address.)
The transit network should not overlap with our on-premise local networks or the Azure networks.
On the on-premise VPN device (in my case pfSense) the configuration for the transit network on the phase 2 tunnel will looks like this.
The remote network IP for the transit network below, we do not need to configure directly in Azure on the local network gateway, it just needs to be defined in the address space(s) field as shown above.
Now back to our configuration by using BGP.
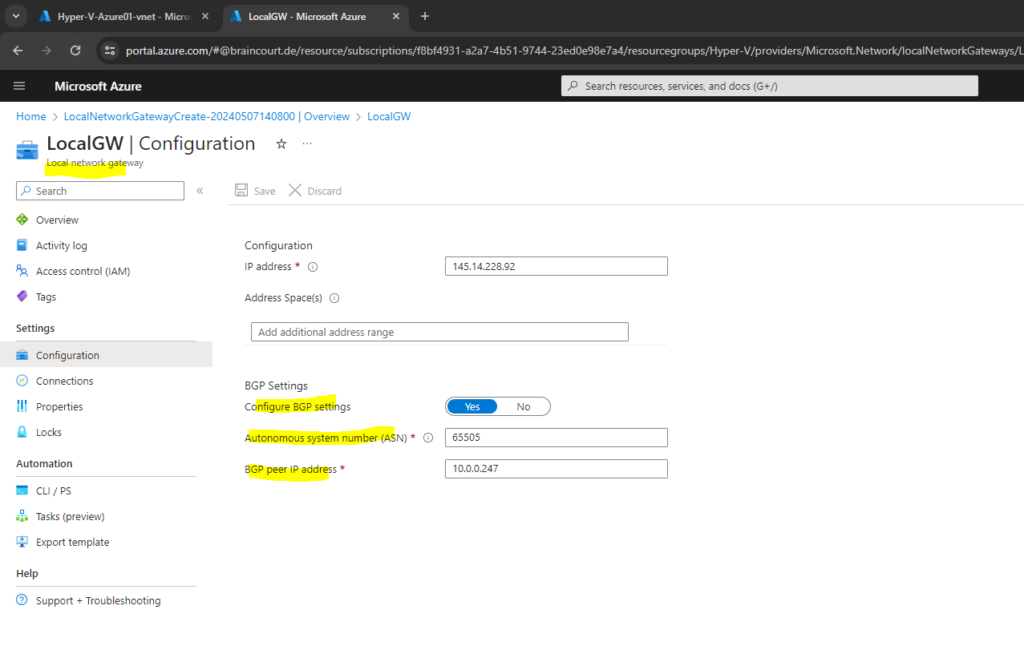
On the Advanced tab below enable BGP and enter the ASN number and BGP peer IP address of your local on-premise VPN device, in my case my pfSense appliance. Then click on Review + create.
The ASN and BGP peer IP address of the local network gateway we will get from our on-premise VPN appliance, in my case here pfSense. The configuration of the pfSense IPSec site-to-site VPN tunnel we will see further down.
!!! Note when using pfSense as on-premise VPN Gateway like me !!!
The BGP peer IP address you need to enter below must be the internal IP address of your pfSense appliance (its LAN interface). So in my case this is the IP address 10.0.0.247 as shown below.For most routers/firewalls (Cisco, Juniper, FortiGate, etc.), this must be typically the VTI interface IP (from the /30 transit subnet used for the ikev2 phase 2 tunnel aka transit network), in my case the IP 172.30.90.31, which is closest to the Azure peer, on the Azure site on the virtual network gateway this is the IP 172.30.90.30)
Unlike Cisco, Juniper, FortiGate, others, pfSense’s FRR implementation (BGP) does not reliably bind BGP sessions to the VTI IP. The VTI is managed by strongSwan, but FRR (the BGP process) is separate and doesn’t inherently bind to that interface.
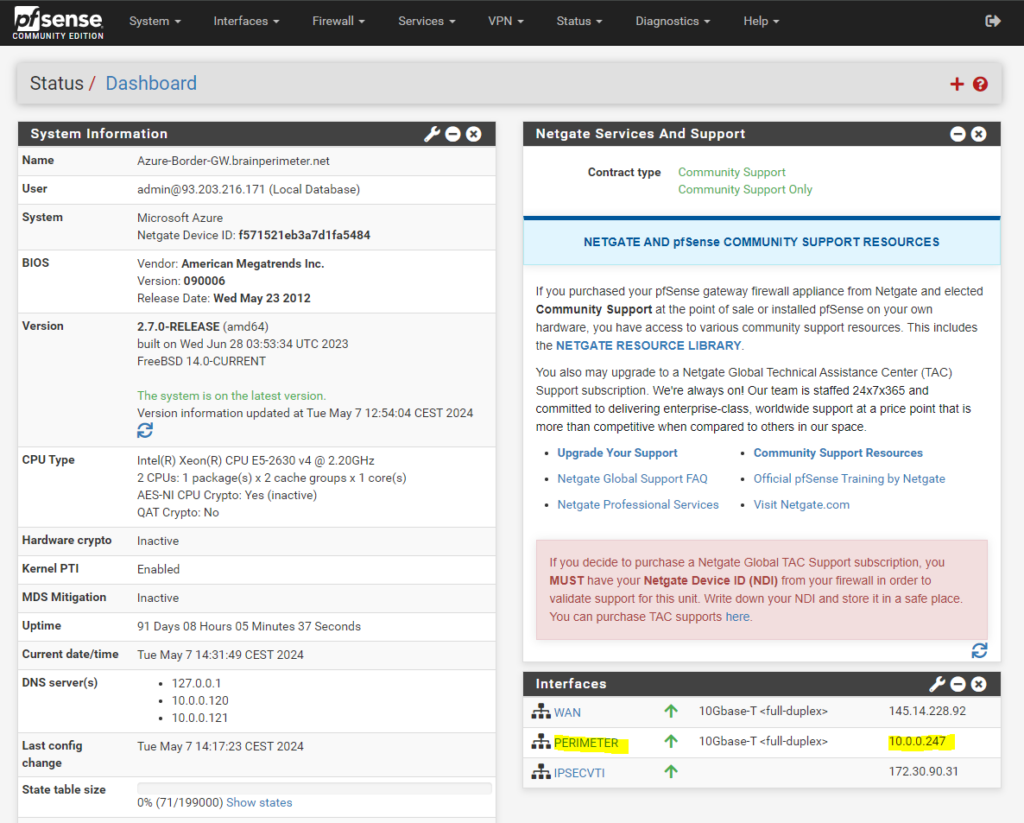
As mentioned above the BGP peer IP address is my internal IP address 10.0.0.247 of the pfSense appliance and its internal interface shown above and not the IP address of the IPSECVTI interface of the IPSec Phase 2 transit network as for most routers/firewalls (Cisco, Juniper, FortiGate, etc.) it is typically.
A BGP-enabled connection between two network gateways requires that their ASNs be different. Additionally, the following ASNs are reserved by Azure: 8075, 8076, 12076 (public), 65515, 65517, 65518, 65519, 65520 (private). You cannot specify these ASNs for your on-premises VPN devices when connecting to Azure VPN gateways. While setting up IPsec connectivity from virtual network gateways to Azure virtual WAN VPN, the ASN for Local Network Gateway is required to be 65515.
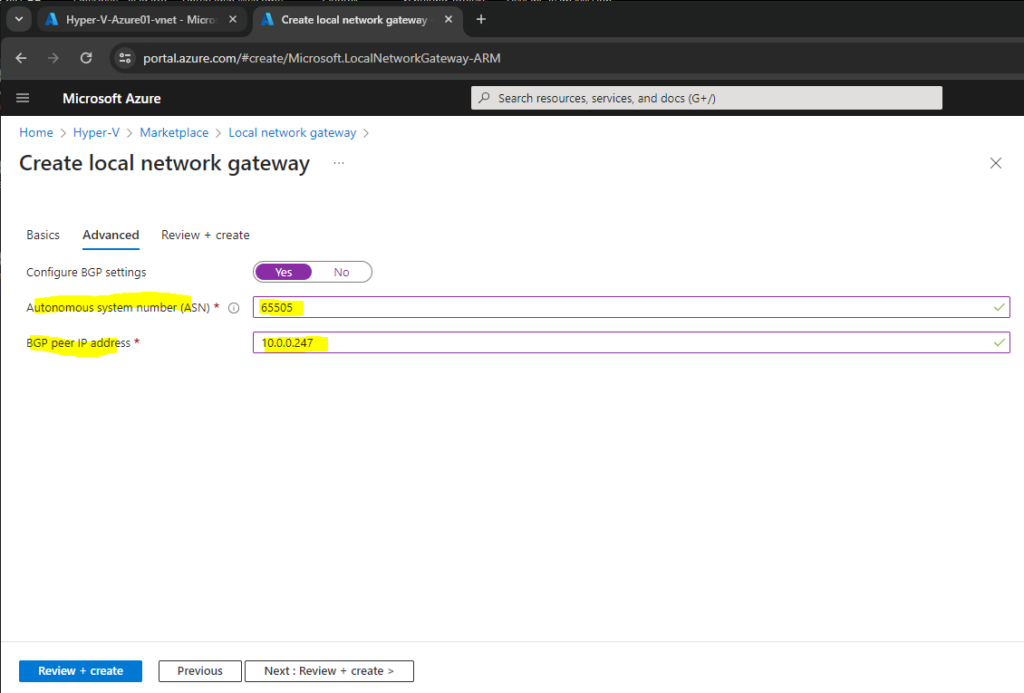
Finally click on Create.
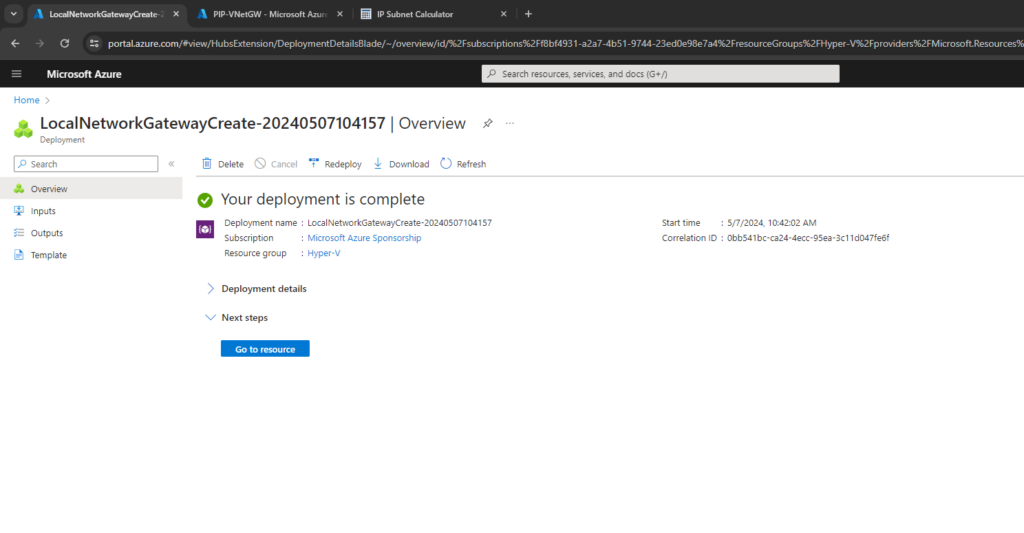
Finally the local network gateway is created.
You can review and change the settings within the Configuration menu. The next step is to create the actual tunnel between your on-premise VPN device and the Azure virtual network gateway within the Connections menu as shown in the next section.
Configure an S2S connection with BGP enabled
Create a site-to-site VPN connection between your virtual network gateway and your on-premises VPN device.
Within the Connections menu of the local network gateway click on Add.
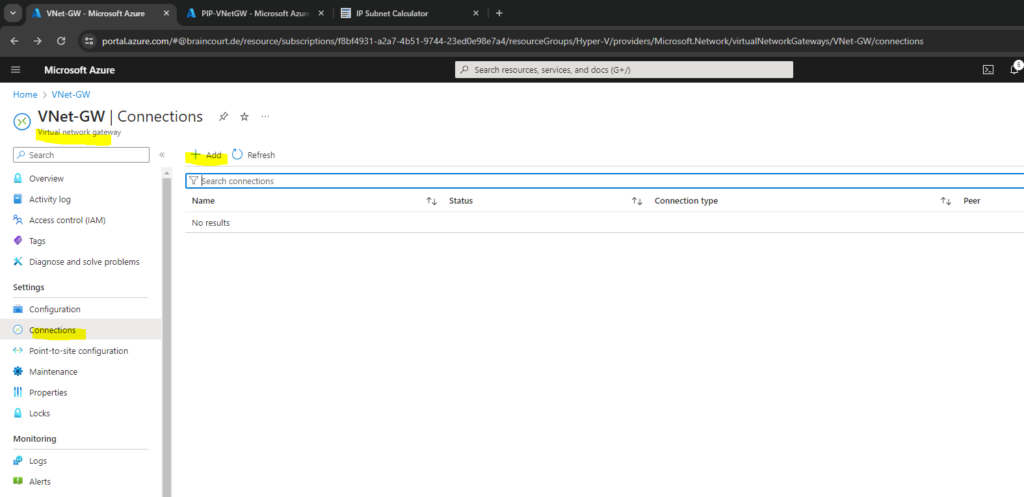
For the connection type select Site-to-site (IPsec).
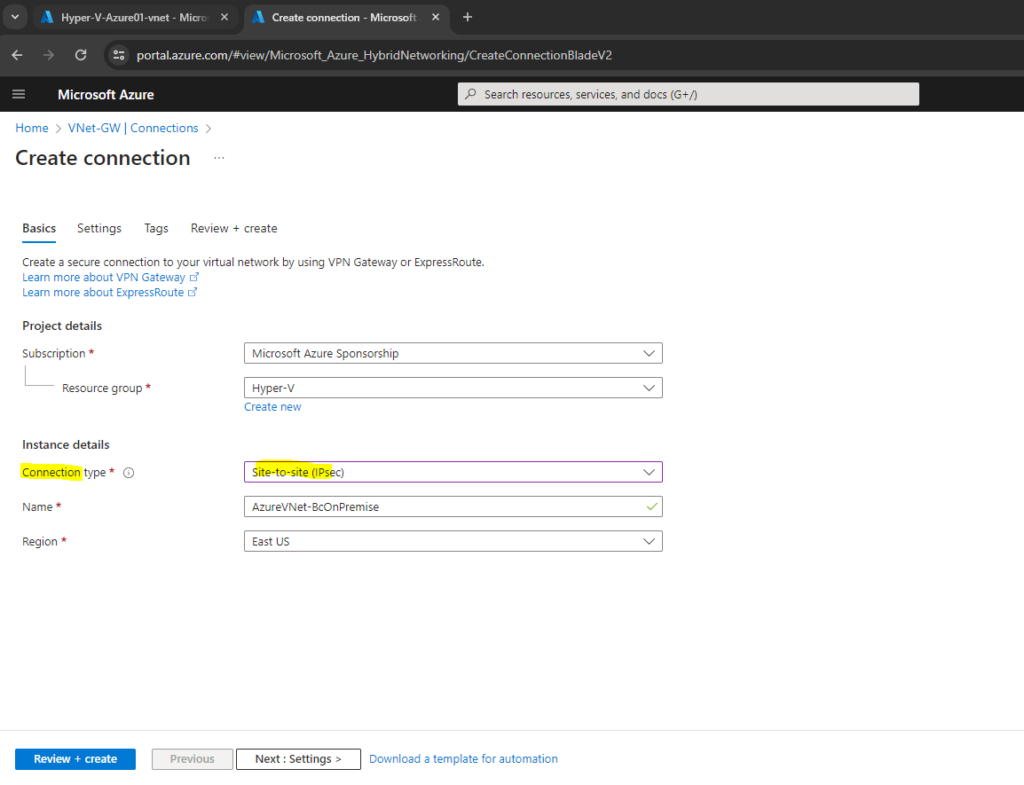
For the IPsec / IKE policy I will use the Default policy. Click on Review + create.
The default policy set for Azure VPN gateway is listed in the article: About VPN devices and IPsec/IKE parameters for Site-to-Site VPN Gateway connections.
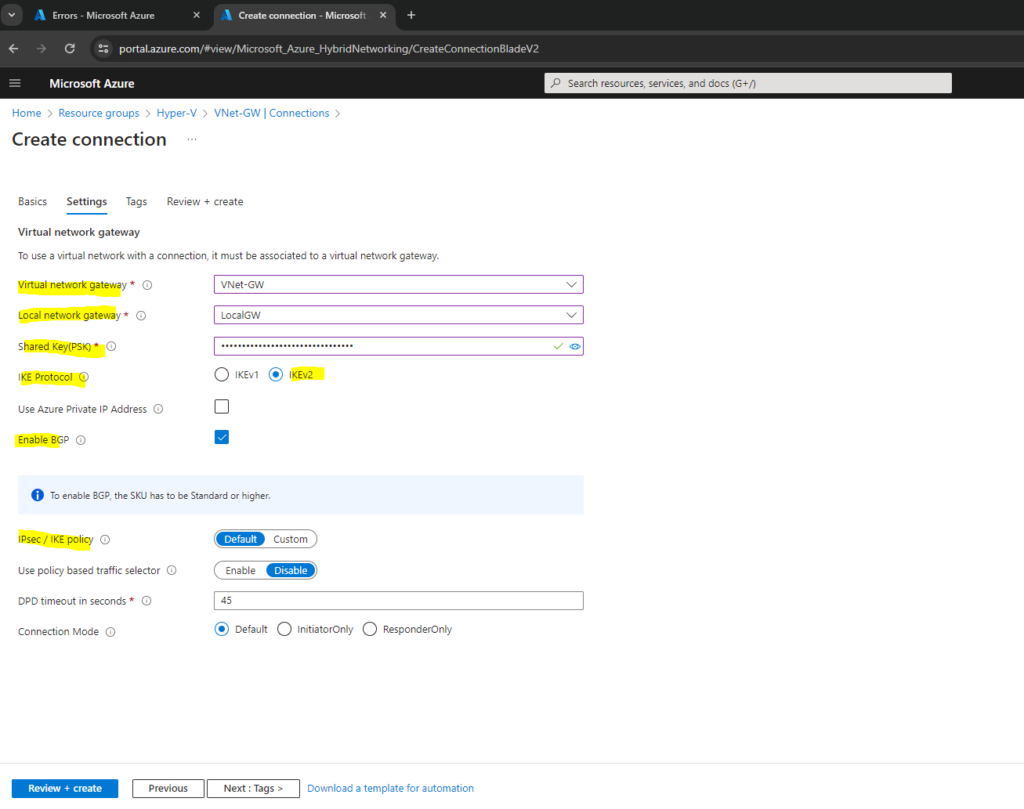
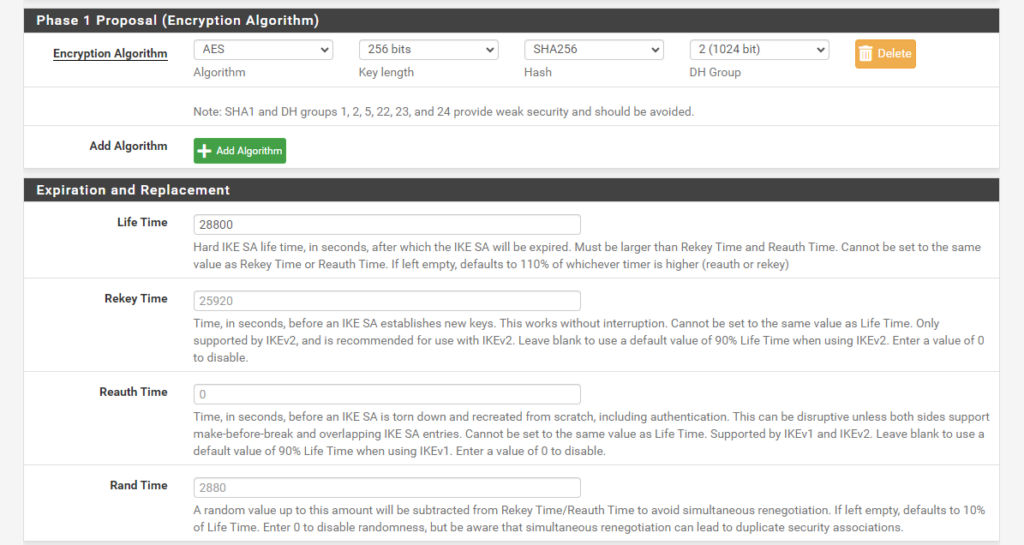
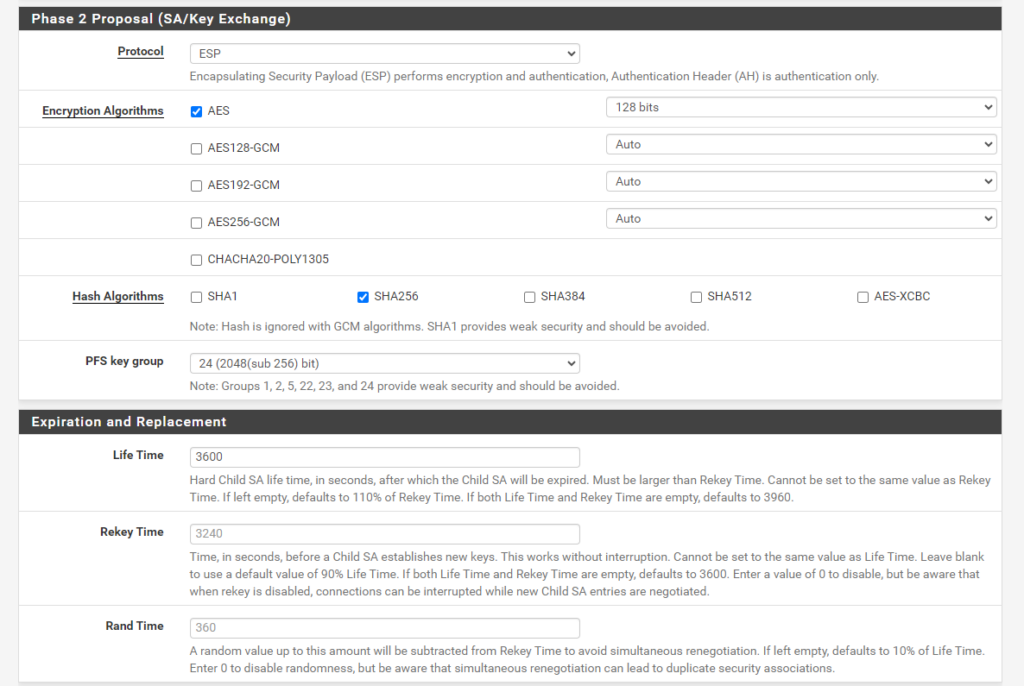
On pfSense the IPsec / IKE policy looks in my case as shown below. These settings are working and are supported by the Azure default policy.
Phase 1.
Phase 2.
Finally the site-to-site VPN connection is created.
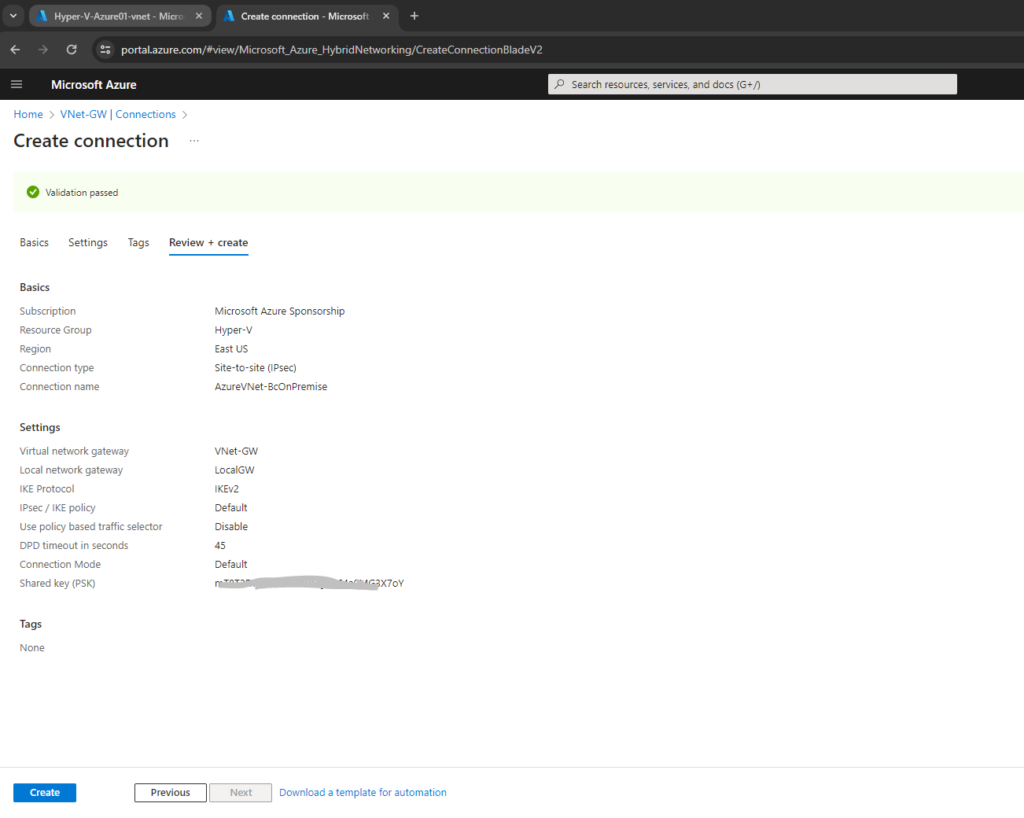
In case also the on-premise VPN device (pfSense appliance in my case) is configured correctly, the Site-To-Site IPSec VPN tunnel should be established .
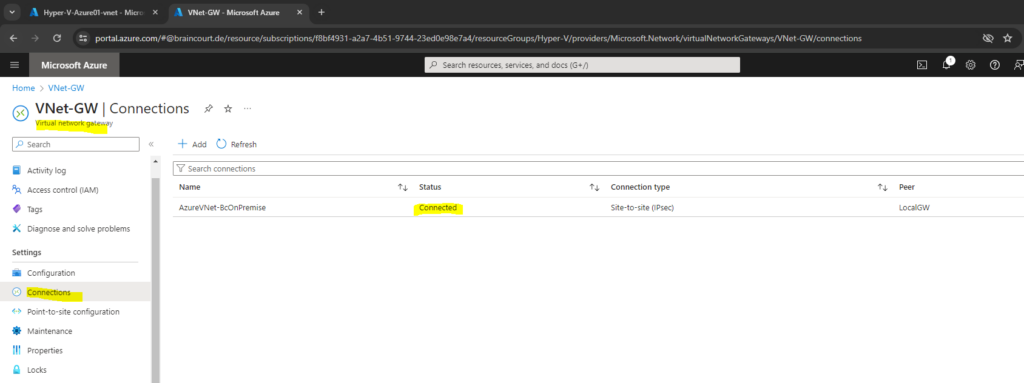
In Azure you can check this on the virtual network gateway under Connections as shown below.
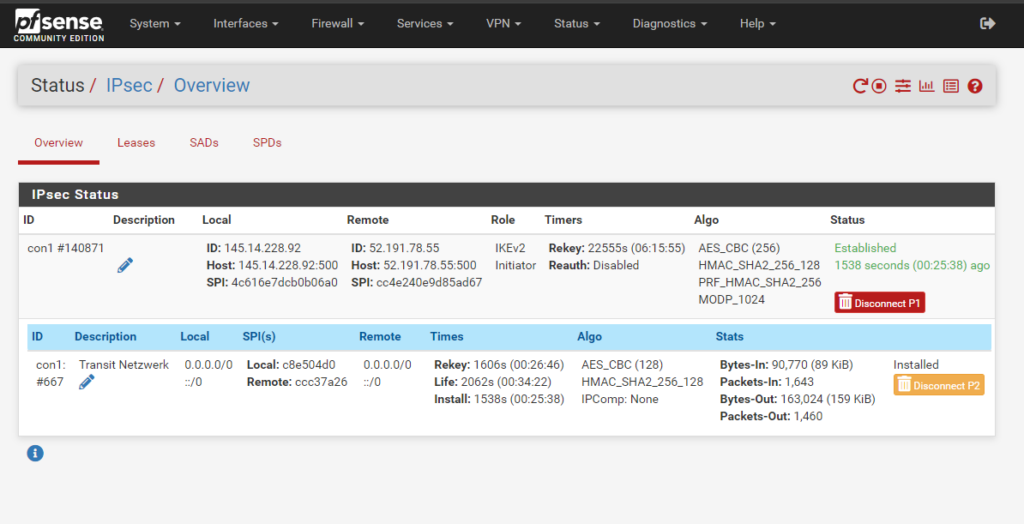
On my on-premise VPN device (pfSense appliance), I can also check if the Site-To-Site IPSec VPN tunnel is established .
Check if BGP is correctly advertising Routes on both Sites
If BGP is working correctly we can check on pfSense by using the Status – FRR page as shown below.
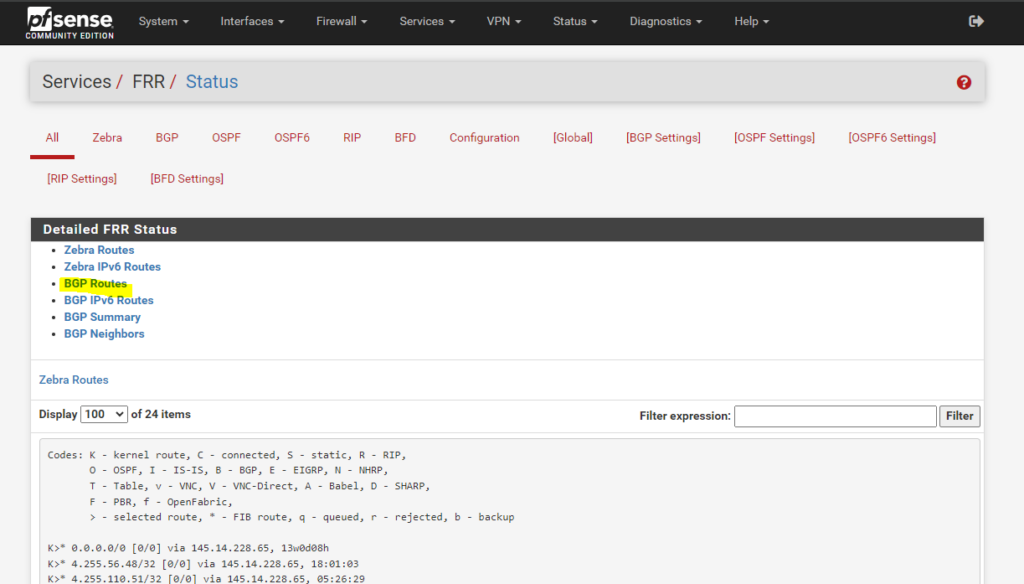
Click on BGP Routes.
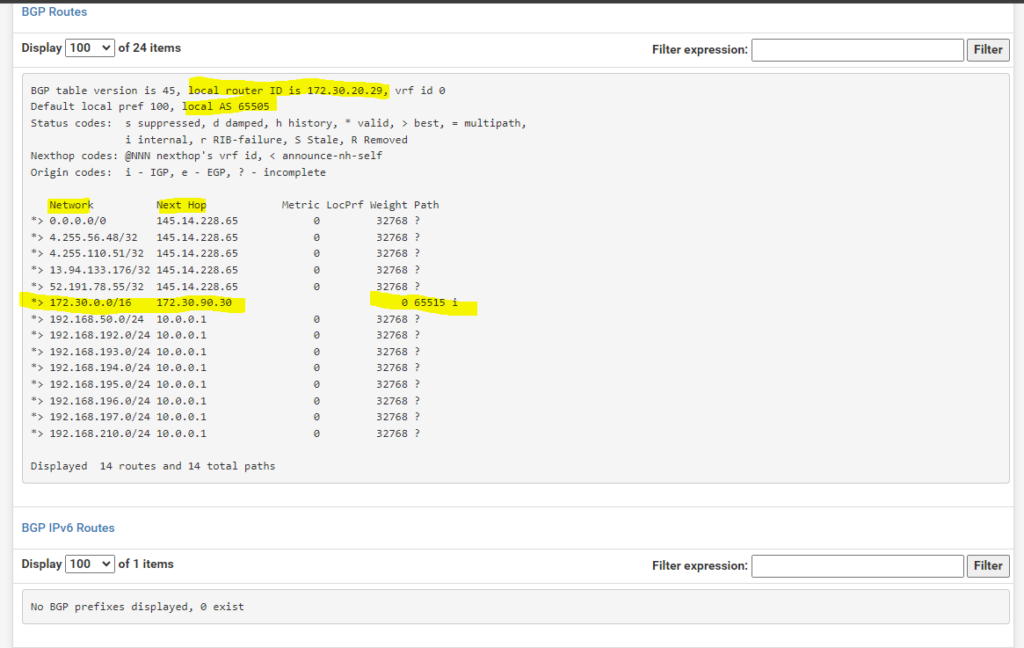
Below you can see that the Azure virtual network gateway is advertising my 172.30.0.0/16 virtual network to my on-premise VPN device (pfSense appliance). Under Path you can see the AS number from the Azure BGP peer which is 65515 (Private ASN reserved by Azure).
About how to configure BGP on pfSense by using the FRR service (OpenBGPD is now deprecated), you can read my following post.
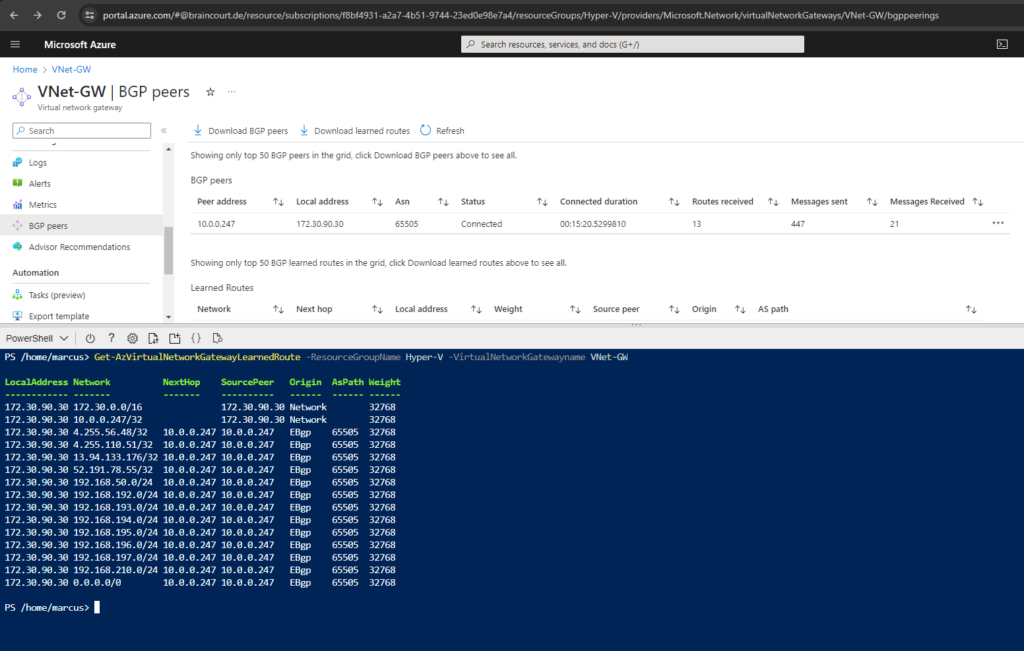
In Azure we can check the advertised routes from our on-premise VPN device by navigating to the virtual network gateway and here under the BGP peers menu as shown below.
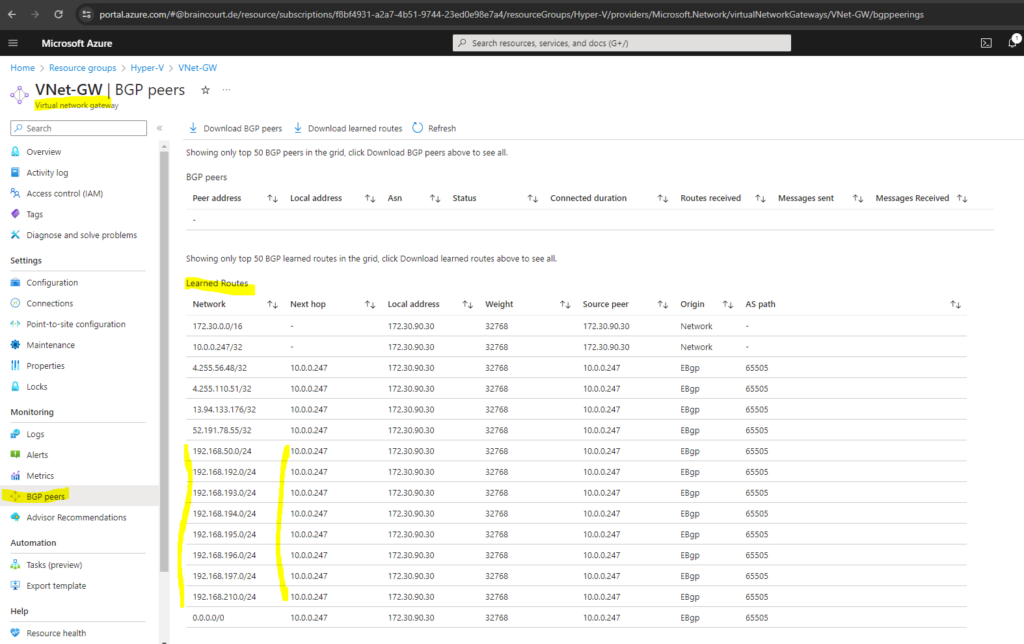
We can also check what routes will be advertised from Azure to our on-premise VPN device by clicking also from the BGP peers menu from the virtual network gateway on the three dots right of the BGP peers line as shown below.
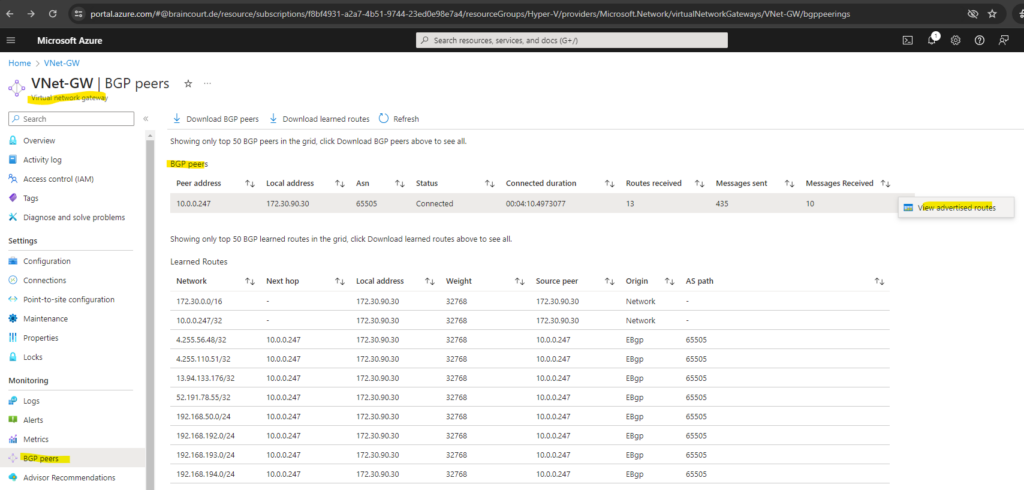
Here we can see that my VNet 172.30.0.0/16 will be advertised to my on-premise VPN device.
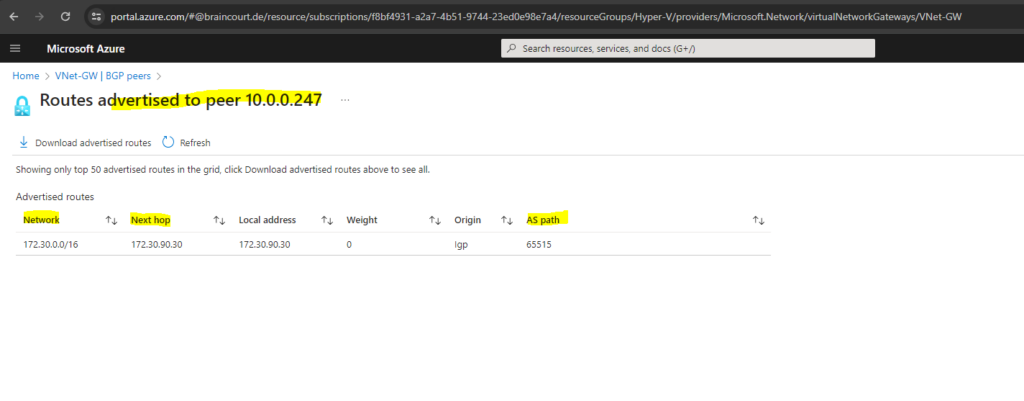
The next hop Azure will use to advertise these routes is the IP address of the Azure BGP peer and configured on my VPN device (pfSense appliance) as remote subnet for the transit network (IPSec Phase 2 tunnel).
You can also use the Cloud Shell and PowerShell cmdlets to view all BGP peers, the status and all the routes the gateway has learnt through BGP.
Use Get-AzVirtualNetworkGatewayLearnedRoute to view all the routes that the gateway has learnt through BGP.
Get-AzVirtualNetworkGatewayLearnedRoute -ResourceGroupName <resourceGroup> -VirtualNetworkGatewayname <gatewayName>
Get-AzVirtualNetworkGatewayLearnedRoute -ResourceGroupName Hyper-V -VirtualNetworkGatewayname VNet-GW
Source: https://learn.microsoft.com/en-us/azure/vpn-gateway/bgp-diagnostics#powershell
Links
Tutorial: Create a site-to-site VPN connection in the Azure portal
https://learn.microsoft.com/en-us/azure/vpn-gateway/tutorial-site-to-site-portalTutorial: Create and manage a VPN gateway by using the Azure portal
https://learn.microsoft.com/en-us/azure/vpn-gateway/tutorial-create-gateway-portalHow to configure BGP for Azure VPN Gateway
https://learn.microsoft.com/en-us/azure/vpn-gateway/bgp-howtoConfigure active-active VPN gateways using the portal
https://learn.microsoft.com/en-us/azure/vpn-gateway/active-active-portalView BGP metrics and status
https://learn.microsoft.com/en-us/azure/vpn-gateway/bgp-diagnosticsAbout VPN devices and IPsec/IKE parameters for Site-to-Site VPN Gateway connections
https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-devicesAbout cryptographic requirements and Azure VPN gateways
https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-compliance-crypto?WT.mc_id=Portal-Microsoft_Azure_HybridNetworking
Tags In
Related Posts
Follow me on LinkedIn


