How to disable Certificate Revocation Check for Windows SSTP VPN?
When using the native Windows SSTP VPN, which utilizes SSL/TLS certificates to authenticate the VPN server and to establish a secure channel between the client and host, Windows by default will first perform a CRL (certificate revocation list) check before finally establishing the connection with the VPN server.
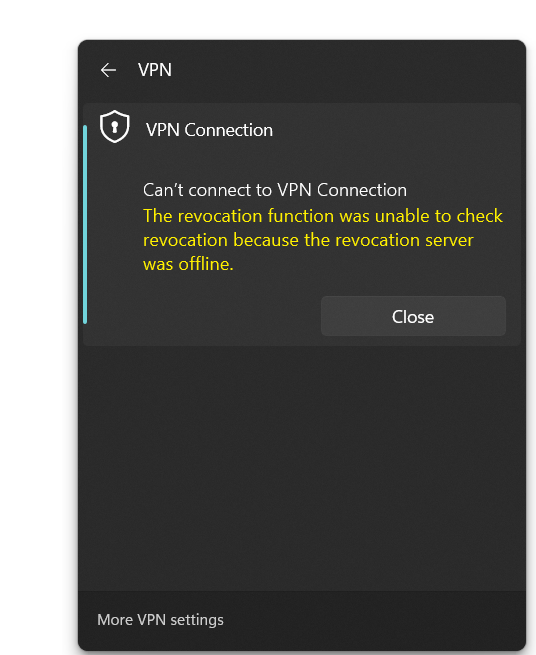
In case for whatever reason this check failed, maybe because like in the error message below the revocation server is really offline, you can use a little workaround in case you trust this VPN server by disabling the CRL (certificate revocation list) check explicitly just for VPN SSTP as shown below.
The revocation function was unable to check revocation because the revocation server was offline.
Open the following registry path and add a new DWORD named NoCertRevocationCheck and set its value to 1.
HKLMSYSTEMCurrentControlSetServicesSstpSvcParameters
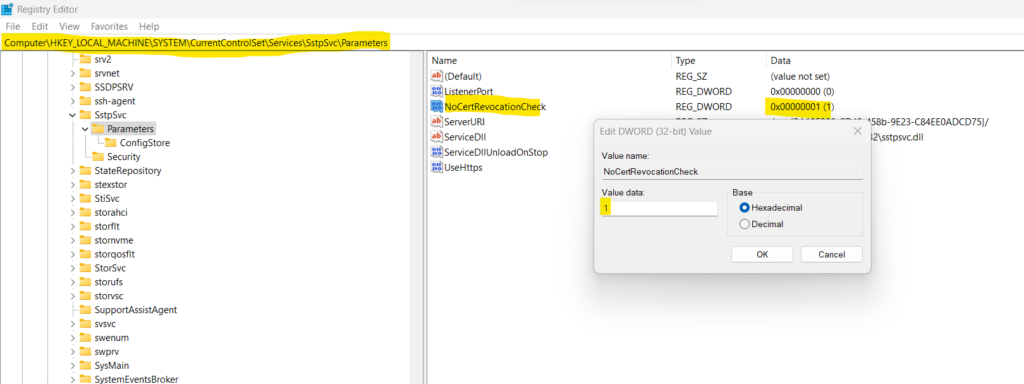
After adding this new entry to the registry, Windows will not perform any CRL (certificate revocation list) check anymore immediately, no reboot is needed to take effect.
How to check an SSL/TLS connection and server certificate
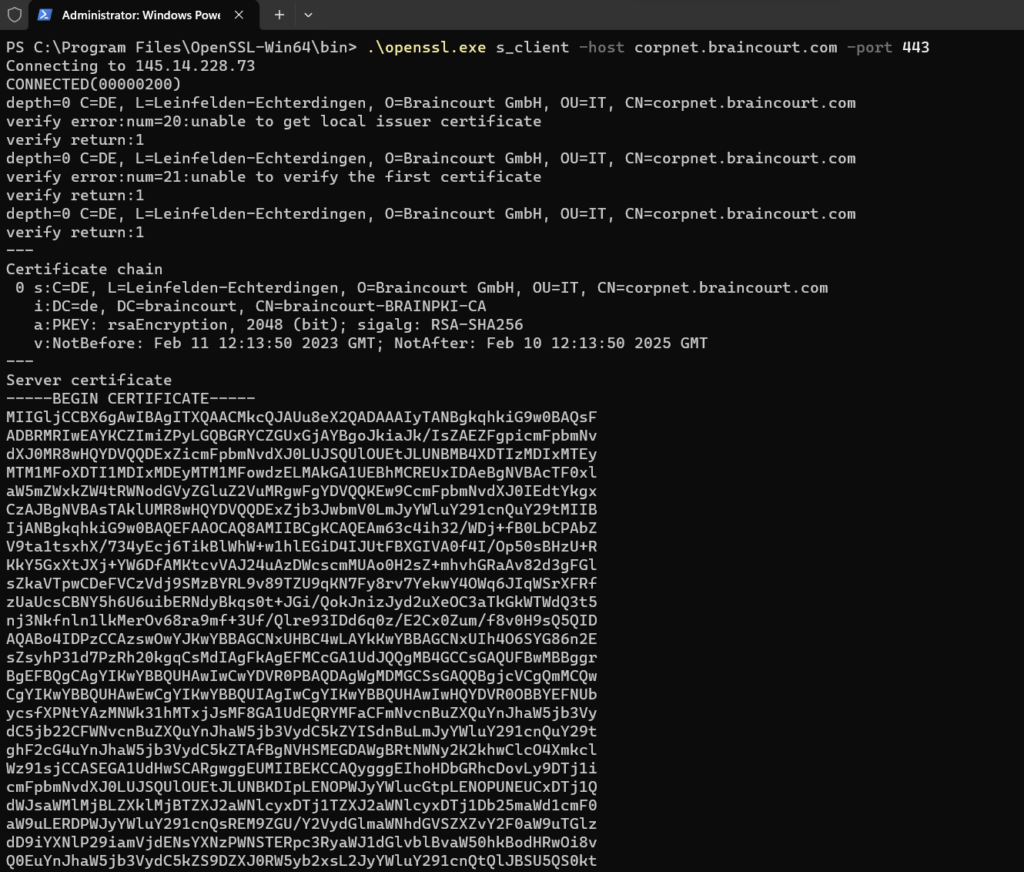
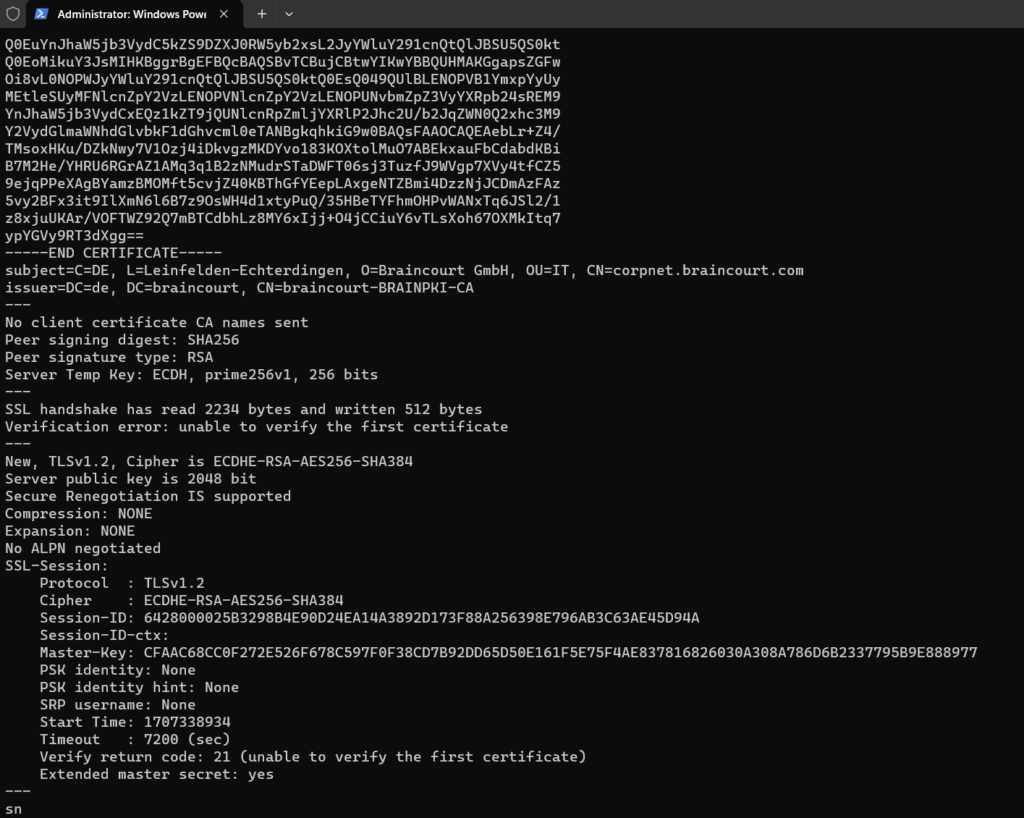
In case you first want to check which certificate this VPN (SSTP) server finally is using, you can use the s_client command and tool from OpenSSL.
The s_client command implements a generic SSL/TLS client which connects to a remote host using SSL/TLS. It is a very useful diagnostic tool for SSL servers.
Source: https://www.openssl.org/docs/man1.0.2/man1/openssl-s_client.html
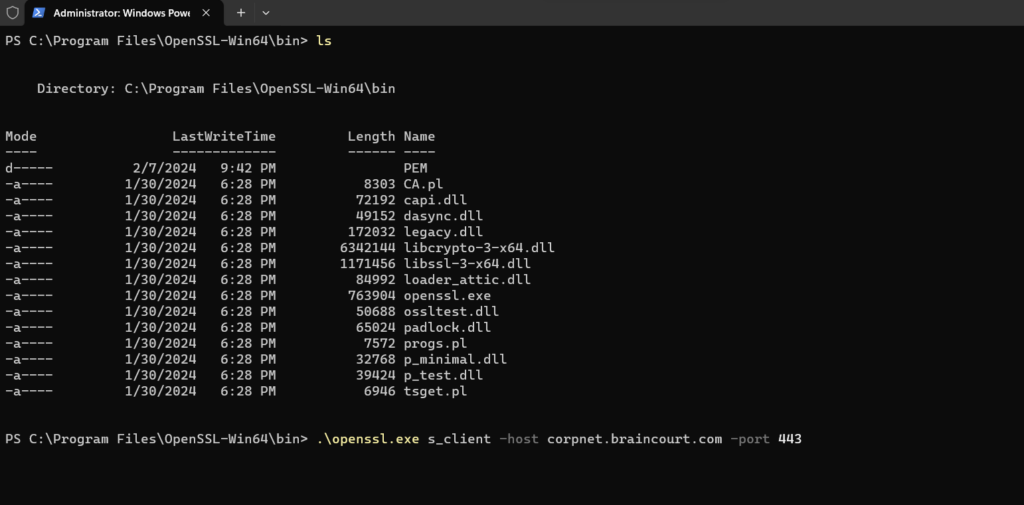
openssl.exe s_client -host <FQDN VPN Host> -port 443
This works by the way also for SMTP servers when using the following syntax: openssl s_client -connect mail.example.com:25 -starttls smtp
Links
Microsoft Secure Socket Tunneling Protocol (SSTP)
https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-sstp/4d0826a8-6214-48aa-80e5-ccd949fb7595s_client command
https://www.openssl.org/docs/man1.0.2/man1/openssl-s_client.htmlDownload Win32/Win64 OpenSSL
https://slproweb.com/products/Win32OpenSSL.html



