Explore the Microsoft Defender Family
In this post I want to give you a summary about what the Microsoft Defender family is exactly and what services and tools are included and covered by.
Originally known as Windows Defender, the suite has evolved and expanded to address the evolving landscape of cyber threats. Microsoft Defender now extends its protective reach beyond traditional desktop environments, offering solutions for servers, cloud services, and even mobile devices.
At first sight the whole product family can be a little bit overwhelming and it’s not easy to keep track of each included solution/tool and their capabilities.
Roughly said, the Microsoft Defender family is made up of 2 main suites, one is covering the Microsoft 365 services and named Microsoft Defender XDR (formerly Microsoft 365 Defender) and one is covering the Azure cloud workloads named Microsoft Defender for Cloud. As of Nov 15 2023 and mentioned below, Microsoft Defender XDR will “not only” covering Microsoft 365 services but also cloud workload alerts, signals and asset information from Microsoft Defender for Cloud.
!!! Note !!!
As of Nov 15 2023, Microsoft Defender XDR is the new name for Microsoft 365 Defender. I can only assume the rebranding is due to the fact, that since Nov 15 2023, also cloud workload alerts, signals and asset information from Microsoft Defender for Cloud are now natively integrated into Microsoft Defender XDR (formerly Microsoft 365 Defender), regarding the following two articles.Ignite news: XDR in an era of end-user-to-cloud cyberattacks and securing the use of AI
https://techcommunity.microsoft.com/t5/microsoft-defender-xdr-blog/ignite-news-xdr-in-an-era-of-end-user-to-cloud-cyberattacks-and/ba-p/3982002Microsoft Defender for Cloud in Microsoft Defender XDR
https://learn.microsoft.com/en-us/microsoft-365/security/defender/microsoft-365-security-center-defender-cloud
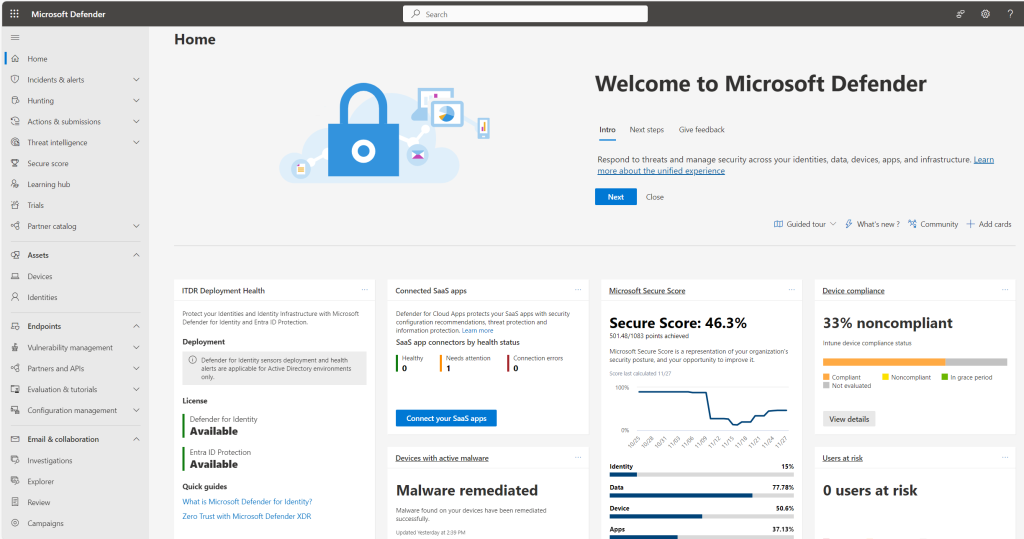
The Microsoft Defender portal at https://security.microsoft.com combines protection, detection, investigation, and response to email, collaboration, identity, device, and cloud app threats, in a central place. The Defender portal emphasizes quick access to information, simpler layouts, and bringing related information together for easier use.
- Introduction
- Microsoft Defender XDR (formerly Microsoft 365 Defender)
- Microsoft Defender for Cloud
- FAQs
- What is extended detection and response (XDR)?
- What is a Cloud Workload Protection Platform (CWPP)?
- What Is Cloud Security Posture Management (CSPM)?
- What's the difference between CWPP and CSPM?
- What is a security operations center (SOC)?
- What is Cloud-Native Application Protection Platforms?
- What is Security Posture?
- What is Continuous Threat Exposure Management (CTEM)?
- What is Secure Access Service Edge (SASE)?
- Links
Introduction
Microsoft Defender XDR (formerly Microsoft 365 Defender)
The Microsoft Defender XDR portal (formerly Microsoft 365 Defender) at https://security.microsoft.com combines protection, detection, investigation, and response to email, collaboration, identity, device, and cloud app threats, in a central place. The Defender portal emphasizes quick access to information, simpler layouts, and bringing related information together for easier use. It includes:
- Microsoft Defender for Office 365 Microsoft Defender for Office 365 helps organizations secure their enterprise with a set of prevention, detection, investigation and hunting features to protect email, and Office 365 resources.
- Microsoft Defender for Endpoint delivers preventative protection, post-breach detection, automated investigation, and response for devices in your organization.
- Microsoft Defender for Identity is a cloud-based security solution that uses your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
- Microsoft Defender for Cloud Apps is a comprehensive cross-SaaS and PaaS solution bringing deep visibility, strong data controls, and enhanced threat protection to your cloud apps.
As already mentioned, since Nov 15 2023 also cloud workload alerts, signals and asset information from Microsoft Defender for Cloud are now natively integrated into Microsoft Defender XDR (formerly Microsoft 365 Defender).
The goal of the portal is to centralize security.
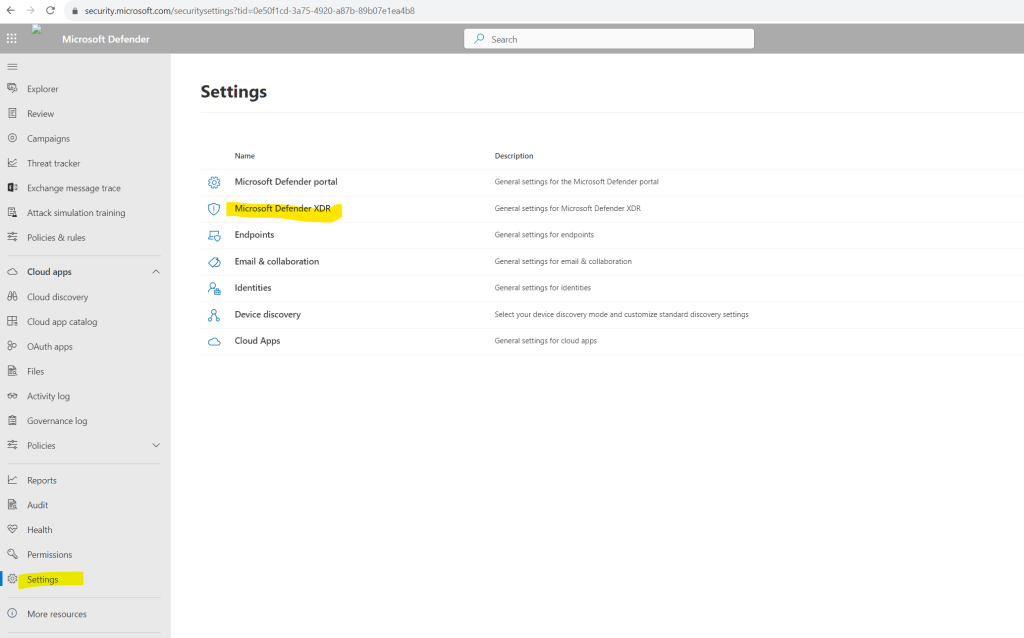
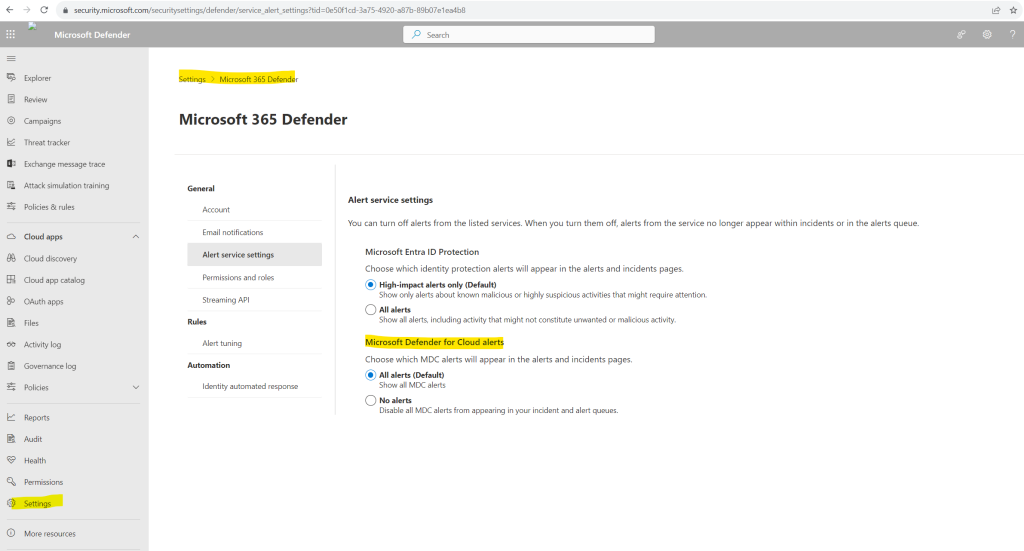
Turn off Defender for Cloud alerts in Microsoft Defender XDR
The alerts for Defender for Cloud are turned on by default. To maintain your subscription-based settings and avoid tenant-based sync or to opt out from the experience, perform the following steps:
In the Microsoft Defender XDR portal, go to Settings > Microsoft Defender XDR.
In Alert service settings, look for Microsoft Defender for Cloud alerts.
Select No alerts to turn off all Defender for Cloud alerts. Selecting this option stops the ingestion of new Defender for Cloud alerts to the portal. Alerts previously ingested remain in an alert or incident page.
Microsoft Defender for Cloud
Microsoft Defender for Cloud is a cloud-native application protection platform (CNAPP) with a set of security measures and practices designed to protect cloud-based applications from various cyber threats and vulnerabilities. Defender for Cloud combines the capabilities of:
- A development security operations (DevSecOps) solution that unifies security management at the code level across multicloud and multiple-pipeline environments
- A cloud security posture management (CSPM) solution that surfaces actions that you can take to prevent breaches
- A cloud workload protection platform (CWPP) with specific protections for servers, containers, storage, databases, and other workloads
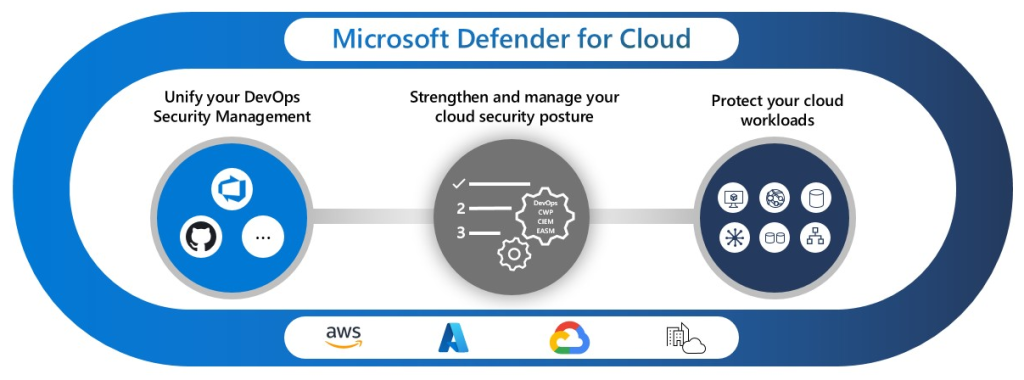
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/
As already mentioned, Multicloud alerts, signals, and asset information for Azure, AWS, and GCP from Microsoft Defender for Cloud are now natively integrated into Microsoft Defender XDR, the new name for Microsoft 365 Defender.
Security teams can now access Defender for Cloud alerts and incidents within the Microsoft Defender XDR portal, providing richer context to investigations that span cloud resources, devices, and identities. In addition, security teams can get the complete picture of an attack, including suspicious and malicious events that happen in their cloud environment, through immediate correlations of alerts and incidents.
Microsoft Defender XDR (formerly Microsoft 365 Defender) combines protection, detection, investigation, and response capabilities to protect attacks on devices, email, collaboration, identity, and cloud apps. The portal’s detection and investigation capabilities are now extended to cloud entities, offering security operations teams a single pane of glass to significantly improve their operational efficiency.
Moreover, the Defender for Cloud incidents and alerts are now part of Microsoft Defender XDR’s public API. This integration allows exporting of security alerts data to any system using a single API.
Microsoft Defender XDR (formerly Microsoft 365 Defender)
Microsoft Defender XDR (formerly Microsoft 365 Defender) is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.
Here’s a list of the different Microsoft Defender XDR products and solutions that Microsoft Defender XDR coordinates with:
- Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender Vulnerability Management
- Microsoft Entra ID Protection
- Microsoft Data Loss Prevention
- App Governance
Note that the coordination of alerts from Microsoft Entra ID Protection (Microsoft Entra IP) to Microsoft Defender XDR is in public preview and may be substantially modified before it’s commercially released. Microsoft Entra IP is available to customers only if they already have Microsoft Defender XDR.
With the integrated Microsoft Defender XDR solution, security professionals can stitch together the threat signals that each of these products receive and determine the full scope and impact of the threat; how it entered the environment, what it’s affected, and how it’s currently impacting the organization. Microsoft Defender XDR takes automatic action to prevent or stop the attack and self-heal affected mailboxes, endpoints, and user identities.
In order to explorer all the capabilities and features from Microsoft Defender XDR, a good point to start is the Microsoft Defender XDR interactive guide.
In this interactive guide, you’ll learn how to protect your organization with Microsoft Defender XDR. You’ll see how Microsoft Defender XDR can help you detect security risks, investigate attacks to your organization, and prevent harmful activities automatically.
Check out the interactive guide
Microsoft Defender for Endpoint
First of all Microsoft Defender for Endpoint is an enterprise endpoint security platform included within Microsoft Defender XDR.
Defender for Endpoint uses the following combination of technology built into Windows 10 (and later) and Microsoft’s robust cloud service:
- Endpoint behavioral sensors: Embedded in Windows 10 (and later), these sensors collect and process behavioral signals from the operating system and send this sensor data to your private, isolated, cloud instance of Microsoft Defender for Endpoint.
- Cloud security analytics: Leveraging big-data, device learning, and unique Microsoft optics across the Windows ecosystem, enterprise cloud products (such as Office 365), and online assets, behavioral signals are translated into insights, detections, and recommended responses to advanced threats.
- Threat intelligence: Generated by Microsoft hunters, security teams, and augmented by threat intelligence provided by partners, threat intelligence enables Defender for Endpoint to identify attacker tools, techniques, and procedures, and generate alerts when they are observed in collected sensor data.
More about you will find in my post below. In this post I will show how we can integrate Microsoft Defender for Endpoint with Microsoft Intune as a Mobile Threat Defense solution and how we can onboard devices either from Intune or directly to Microsoft Defender for Endpoint
Microsoft Defender for Office 365
Microsoft Defender for Office 365 is a seamless integration into your Office 365 subscription that protects against threats in email, links (URLS), attachments, or collaboration tools.
Microsoft 365 security builds on the core protections offered by EOP.
EOP is included in all Microsoft 365 organizations that have Exchange Online mailboxes.
More about you will find in my following post.
Microsoft Defender for Identity
Microsoft Defender for Identity, formerly Azure Advanced Threat Protection, is a cloud-based security solution. It uses your on-premises Windows Server Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Defender for Identity is fully integrated with Microsoft Defender XDR (formerly Microsoft 365 Defender), and leverages signals from both on-premises Active Directory and cloud identities to help you better identify, detect, and investigate advanced threats directed at your organization.
More about you will find in my following post.
Microsoft Entra ID Protection
Microsoft Entra ID Protection helps organizations detect, investigate, and remediate identity-based risks. These identity-based risks can be further fed into tools like Conditional Access to make access decisions or fed back to a security information and event management (SIEM) tool for further investigation and correlation.
Using this feature requires Microsoft Entra ID P2 licenses. More you will find here https://learn.microsoft.com/en-us/entra/id-protection/overview-identity-protection#license-requirements.
Source: https://learn.microsoft.com/en-us/entra/id-protection/overview-identity-protection
More details and how it works exactly you will find in the link above and in the following YouTube video by John Savill.
Microsoft Azure AD Identity Protection Deep Dive
https://www.youtube.com/watch?v=Nx2ych3xHl0&t=1328s
Microsoft Defender for Identity vs. Microsoft Entra ID Protection
You may wonder what’s exactly the difference between Microsoft Defender for Identity and Microsoft Entra ID Protection (formerly Azure AD Identity Protection)?
First of all both products will provide very similar protection for identity and access. Both will prevent, detect and remediate identity risks in your organization.
Microsoft Entra ID Protection (formerly Azure AD Identity Protection) can just be used exclusively to protect cloud native identities.
Microsoft Defender for Identity in contrast is primarily focused to secure on-premise identities but also capable to secure cloud native identities.
Microsoft Defender for Identity can secure on-premise identities by leveraging signals from sensors installed within the on-premise environment. In addition because Defender for Identity is fully integrated with Microsoft Defender XDR (formerly Microsoft 365 Defender), it is also able to leverage signals from cloud identities to get a holistic picture and single view what’s going on in your hybrid environment.
Microsoft Defender Vulnerability Management
Reducing cyber risk requires comprehensive risk-based vulnerability management to identify, assess, remediate, and track all your biggest vulnerabilities across your most critical assets, all in a single solution.
Defender Vulnerability Management delivers asset visibility, intelligent assessments, and built-in remediation tools for Windows, macOS, Linux, Android, iOS, and network devices. Leveraging Microsoft threat intelligence, breach likelihood predictions, business contexts, and devices assessments, Defender Vulnerability Management rapidly and continuously prioritizes the biggest vulnerabilities on your most critical assets and provides security recommendations to mitigate risk.
Vulnerability Management capabilities for servers
For Microsoft Defender for Cloud customers, Defender Vulnerability Management is natively integrated within Defender for Cloud to perform vulnerability assessments for cloud based virtual machines and recommendations will automatically populate in the Defender for Cloud portal.
Defender Vulnerability Management premium capabilities are available to server devices with Microsoft Defender for Servers Plan 2.
License Requirements
If the customer has Defender for Endpoint Plan 2 they have the core vulnerability management capabilities.
Defender Vulnerability Management is a separate solution from Defender for Endpoint (not included in Defender for Endpoint Plan 2) and is available as an add-on.
Microsoft Defender Vulnerability Management is available via two services:
- Microsoft Defender for Endpoint Plan 2 customers can seamlessly enhance their existing generally available vulnerability management capabilities with the Microsoft Defender Vulnerability Management add-on. This service provides consolidated inventories, expanded asset coverage, cross-platform support, and new assessment and mitigation tools. To sign up for the free 90-day trial, see Defender Vulnerability Management Add-on.
- For new customers or existing Defender for Endpoint P1 or Microsoft 365 E3 customers looking for a risk-based vulnerability management solution, Microsoft Defender Vulnerability Management Standalone helps you efficiently discover, assess, and remediate vulnerabilities and misconfigurations in one place. To sign up for the free 90-day trial, see Defender Vulnerability Management Standalone.
Onboard Devices to Microsoft Defender Vulnerability Management
To onboard devices to Defender Vulnerability Management you follow the same steps as you would for onboarding devices to Microsoft Defender for Endpoint as shown in my post below.
Microsoft Defender for Cloud Apps
Defender for Cloud Apps shows the full picture of risks to your environment from SaaS app usage and resources, and gives you control of what’s being used and when.
- Identify: Defender for Cloud apps uses data based on an assessment of network traffic and an extensive app catalog to identify apps accessed by users across your organization. Defender for Cloud Apps provides details on which apps are really being used both on and off your corporate network.Defender for Cloud Apps detects all your cloud services, assigns each a risk ranking, and also identifies all the users and third-party apps able to sign in.
- Assess: Evaluate discovered apps for more than 90 risk indicators, allowing you to sort through the discovered apps and assess your orgs security and compliance posture.
- Manage: Set policies that monitor apps around the clock. For example, if anomalous behavior happens, like unusual spikes in usage, you’re automatically alerted and guided to action.
For more information, see Set up cloud discovery.
While optimizing an organization’s security posture is a critical focus area, security teams are challenged by needing to research best practices for each app individually.
Defender for Cloud Apps helps you by surfacing misconfigurations and recommending specific actions to strengthen the security posture for each connected app. Recommendations are based on industry standards like the Center for Internet Security and follow best practices set by the specific app provider
More about Microsoft Defender for Cloud Apps you will find here https://learn.microsoft.com/en-us/defender-cloud-apps/
Microsoft Data Loss Prevention
Organizations have sensitive information under their control such as financial data, proprietary data, credit card numbers, health records, or social security numbers. To help protect this sensitive data and reduce the risk from oversharing, they need a way to help prevent their users from inappropriately sharing sensitive data with people who shouldn’t have it.
This practice is called data loss prevention (DLP).
In Microsoft Purview, you implement data loss prevention by defining and applying DLP policies. With a DLP policy, you can identify, monitor, and automatically protect sensitive items across:
- Microsoft 365 services such as Teams, Exchange, SharePoint, and OneDrive accounts
- Office applications such as Word, Excel, and PowerPoint
- Windows 10, Windows 11, and macOS (three latest released versions) endpoints
- non-Microsoft cloud apps
- on-premises file shares and on-premises SharePoint
- Power BI
DLP detects sensitive items by using deep content analysis, not by just a simple text scan. Content is analyzed:
- For primary data matches to keywords.
- By the evaluation of regular expressions
- By internal function validation
- By secondary data matches that are in proximity to the primary data match.
- DLP also uses machine learning algorithms and other methods to detect content that matches your DLP policies.
Source: https://learn.microsoft.com/en-us/purview/dlp-learn-about-dlp
Microsoft Data Loss Prevention is a risk and compliance solution which is included and unified within Microsoft Purview.
Microsoft Purview on his part is a comprehensive set of solutions that can help your organization govern, protect, and manage data, wherever it lives.
Microsoft Purview solutions provide integrated coverage and help address the fragmentation of data across organizations, the lack of visibility that hampers data protection and governance, and the blurring of traditional IT management roles.
More about Microsoft Purview and Microsoft Data Loss Prevention you will find soon in a dedicated post on my blog.
App Governance
App governance is included in Defender for Cloud Apps and is a set of security and policy management capabilities designed for OAuth-enabled apps registered on Azure Active Directory (Azure AD), Google, and Salesforce.
App governance delivers visibility, remediation, and governance into how these apps and their users access, use, and share sensitive data in Microsoft 365 and other cloud platforms through actionable insights and automated policy alerts and actions.
App governance also enables you to see which user-installed OAuth applications have access to data on Microsoft 365, Google Workspace, and Salesforce. It tells you what permissions the apps have and which users have granted access to their accounts.
App governance insights enable you to make informed decisions around blocking or restricting apps that present significant risk to your organization. For example:
- Insights: See a view of all non-Microsoft apps registered to Azure Active Directory, Google, or Salesforce in your organization on a single dashboard. You can see the status of apps and their activities, and react or respond to them.
- Governance: Create proactive or reactive policies for app and user patterns and behaviors and protect your users from using noncompliant or malicious apps and limiting the access of risky apps to your data.
- Detection: Be alerted and notified when there are anomalies in app activity and when noncompliant, malicious, or risky apps are used.
- Remediation: Along with automatic remediation capabilities, use remediation controls in a timely manner to respond to anomalous app activity detections.
More about App governance you will find in the following article from Microsoft https://learn.microsoft.com/en-us/defender-cloud-apps/app-governance-manage-app-governance.
Microsoft Defender for Cloud
Microsoft Defender for Cloud is a cloud-native application protection platform (CNAPP) with a set of security measures and practices designed to protect cloud-based applications from various cyber threats and vulnerabilities. Defender for Cloud combines the capabilities of:
- A development security operations (DevSecOps) solution that unifies security management at the code level across multicloud and multiple-pipeline environments
- A cloud security posture management (CSPM) solution that surfaces actions that you can take to prevent breaches
- A cloud workload protection platform (CWPP) with specific protections for servers, containers, storage, databases, and other workloads

Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/
More about Microsoft Defender for Cloud and all workloads (eg. APIs, Servers, Containers, Storage Accounts, …) it will protect, you will find in my following post.
FAQs
What is extended detection and response (XDR)?
Extended detection and response, often abbreviated (XDR), is a software as a service (SaaS) tool that offers holistic, optimized security by integrating security products and data into simplified solutions. As enterprises increasingly encounter an evolving threat landscape and complex security challenges with workforces in multicloud, hybrid environments, XDR security presents a more efficient, proactive solution.
In contrast to systems like endpoint detection and response (EDR), XDR broadens the scope of security. XDR software integrates protection across a wider range of products, including an organization’s endpoints, servers, cloud applications, emails, and more.
From there, XDR combines prevention, detection, investigation, and response, providing visibility, analytics, correlated incident alerts, and automated responses to improve data security and combat threats.
Source: https://www.microsoft.com/en/security/business/security-101/what-is-xdr
What is a Cloud Workload Protection Platform (CWPP)?
A Cloud Workload Protection Platform (CWPP) is a security solution designed to protect cloud-based workloads, applications, and data. CWPP solutions typically include features such as antivirus, intrusion detection and prevention, application control, and integrity monitoring. They are designed to provide runtime protection for the workloads in the cloud environment.
What Is Cloud Security Posture Management (CSPM)?
Cloud security posture management tools help in the identification and remediation of risks across cloud infrastructures, including Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS). These tools continuously assess the security posture across multi-cloud environments by maintaining a current inventory of the cloud assets for proactive analysis and risk assessment to detect any misconfigurations. Once these misconfigurations are identified, security controls are developed and implemented. CSPM solutions also integrate with DevOps tools, streamlining the incident response process and ensuring continuous compliance with regulatory requirements and security frameworks by providing visibility of the cloud environment’s security posture.
Source: https://www.gartner.com/reviews/market/cloud-security-posture-management-tools
What’s the difference between CWPP and CSPM?
CWPP (Cloud Workload Protection Platform) and CSPM (Cloud Security Posture Management) are two different but complementary approaches to securing cloud environments. They address different aspects of cloud security, focusing on different stages of the cloud security lifecycle.
CWPP is primarily concerned with securing the workloads or applications running in the cloud. It aims to protect the actual applications, processes, and data within virtual machines (VMs) or containers.
CSPM, on the other hand, is focused on ensuring that the overall configuration and setup of the cloud infrastructure adhere to security best practices and compliance requirements.
What is a security operations center (SOC)?
A security operations center (SOC) can be defined both as a team, often operating in shifts around the clock, and a facility dedicated to and organized to prevent, detect, assess and respond to cybersecurity threats and incidents, and to fulfill and assess regulatory compliance.
What Is a Security Operations Center (SOC) Analyst?
A SOC Analyst is a cybersecurity professional responsible for monitoring an organization’s IT infrastructure, networks, and systems for security threats and incidents. The primary goal of a SOC Analyst is to ensure the confidentiality, integrity, and availability of the organization’s information assets.
What is Cloud-Native Application Protection Platforms?
Cloud-native application protection platforms (CNAPPs) are a unified and tightly integrated set of security and compliance capabilities designed to secure and protect cloud-native applications across development and production. CNAPPs consolidate a large number of previously siloed capabilities, including container scanning, cloud security posture management, infrastructure as code scanning, cloud infrastructure entitlement management, runtime cloud workload protection and runtime vulnerability/configuration scanning.
Source: https://www.gartner.com/reviews/market/cloud-native-application-protection-platforms
What is Security Posture?
Security Posture is a term which describes how well an organization is prepared and protected against cybersecurity threats. It involves the overall strength and effectiveness of security measures, encompassing policies, procedures, technologies, and practices to safeguard information systems and assets.
What is Continuous Threat Exposure Management (CTEM)?
The first thing to say is that it isn’t a new tool or a new technology. It’s more of a fully joined-up thinking approach to managing cybersecurity in an age when our threat surfaces are growing broader by the day. CTEM is a cybersecurity strategy that involves constantly exposing an organization’s networks, systems, and assets to simulated attacks to identify vulnerabilities and weaknesses. The goal of CTEM is to improve the organization’s overall security posture by identifying and addressing these areas of concern before they can be exploited by real attackers.
Source: https://www.reflectiz.com/blog/what-is-ctem/
Gartner® describes CTEM as a “program that surfaces and actively prioritizes whatever most threatens your business“
Source: https://www.ibm.com/products/randori-recon/threat-exposure-management
What is Secure Access Service Edge (SASE)?
Secure access service edge (SASE) is a cloud-native architecture that unifies SD-WAN with security functions like SWG, CASB, FWaaS, and ZTNA into one service.
A SASE (secure access service edge) architecture combines networking and security as a service functions into a single cloud-delivered service at the network edge. This enables an organization to support dispersed remote and hybrid users automatically by connecting them to nearby cloud gateways as opposed to backhauling traffic to corporate data centers. It also provides consistent secure access to all applications while maintaining full visibility and inspection of traffic across all ports and protocols.
The model radically simplifies management and reduces complexity, which are two of the main goals of SASE. It transforms the perimeter into a consistent set of cloud-based capabilities that can be deployed where and when they’re needed. This is a more streamlined alternative to establishing a perimeter around the data center using a collection of disparate, point-product security appliances.
Because it’s cloud-based, secure access service edge enables a more dynamic and high-performing network that adapts to changing business requirements, an evolving threat landscape, and the new innovations that will shape the future of your network.
Source: https://www.paloaltonetworks.com/cyberpedia/what-is-sase
Palo Alto Networks CEO says Microsoft has a long way to go on cybersecurity
https://www.cnbc.com/2023/07/13/palo-alto-networks-ceo-says-microsoft-has-a-way-to-go-on-cybersecurity.html
2023 Gartner® Magic Quadrant™ for Single-Vendor SASE
https://www.forcepoint.com/resources/industry-analyst-reports/gartner-sase-magic-quadrant-2023
What is secure access service edge (SASE)?
Secure access service edge, often abbreviated (SASE), is a security framework that converges software-defined wide area networking (SD-WAN) and Zero Trust security solutions into a converged cloud-delivered platform that securely connects users, systems, endpoints, and remote networks to apps and resources.The difference between SASE and SSE
Security service edge (SSE) is a standalone subset of SASE that focuses exclusively on cloud security services. SSE delivers secure access to the internet by way of a protected web gateway, safeguards SaaS and cloud apps via a CASB, and secures remote access to private apps through ZTNA. SASE also features these components, but expands to include SD-WAN, WAN optimization, and quality of service (QoS) elements.Source: https://www.microsoft.com/en/security/business/security-101/what-is-sase
Links
Microsoft Defender for Office 365 documentation
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-securityMicrosoft Defender Vulnerability Management
https://learn.microsoft.com/en-us/microsoft-365/security/defender-vulnerability-managementMicrosoft Defender for Cloud documentation
https://learn.microsoft.com/en-us/azure/defender-for-cloud/Microsoft Defender for Endpoint
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpointMicrosoft 365 security
https://learn.microsoft.com/en-us/microsoft-365/security
Tags In
Related Posts
Follow me on LinkedIn


