Set up Microsoft Defender for Office 365
In this post I want to give you a summary about what Microsoft Defender for Office 365 is exactly and how you can quickly set up and configure it by using Microsoft’s best practices.
Microsoft Defender for Office 365 is a seamless integration into your Office 365 subscription that protects against threats in email, links (URLS), attachments, or collaboration tools.
Microsoft 365 security builds on the core protections offered by EOP.
EOP is included in all Microsoft 365 organizations that have Exchange Online mailboxes.
The Microsoft Defender family is made up of 2 main suites, one is covering the Microsoft 365 services and is named Microsoft 365 Defender and one is covering the Azure cloud and is named Microsoft Defender for Cloud.
Microsoft Defender for Office 365 is part of and coordinated by Microsoft 365 Defender. In order to manage and monitor Microsoft Defender for Office 365 you will therefore use the Microsoft 365 Defender portal at https://security.microsoft.com.
The portal combines protection, detection, investigation, and response to email, collaboration, identity, device, and cloud app threats, in a central place. The Defender portal emphasizes quick access to information, simpler layouts, and bringing related information together for easier use. It includes:
- Microsoft Defender for Office 365 Microsoft Defender for Office 365 helps organizations secure their enterprise with a set of prevention, detection, investigation and hunting features to protect email, and Office 365 resources.
- Microsoft Defender for Endpoint delivers preventative protection, post-breach detection, automated investigation, and response for devices in your organization.
- Microsoft Defender for Identity is a cloud-based security solution that uses your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
- Microsoft Defender for Cloud Apps is a comprehensive cross-SaaS and PaaS solution bringing deep visibility, strong data controls, and enhanced threat protection to your cloud apps.
The goal of this portal is to centralize security.
Introduction
Every Microsoft 365 subscription comes with security capabilities. The goals and available actions depend on the focus of these different subscriptions. In Microsoft 365 security, there are three main security services (or products) tied to your subscription type:
- Exchange Online Protection (EOP)
Exchange Online Protection is the foundation for Microsoft Defender for Office 365 protection, providing malware and spam filtering, Data loss prevention, and Advanced Threat Protection against phishing and other threats. - Microsoft Defender for Office 365 Plan 1 (Defender for Office 365 P1)
Plan 1 builds upon the security of Exchange Online Protection by incorporating supplementary prevention measures, advanced detection features, and real-time investigations to enable comprehensive monitoring. Plan 1 adds anti-malware policies, anti-phishing policies, business email compromise protection, safe attachments and safe links including time of click protection in email, Microsoft 365 clients and Teams. - Microsoft Defender for Office 365 Plan 2 (Defender for Office 365 P2)
Microsoft Defender for Office 365 Plan 2 builds on top of Plan 1 and Exchange Online Protection by adding more prevention tools, extra forms of detection and real-time detections for investigations including Threat explorer, Campaigns, Automated investigation and remediation, Reporting and Attack Simulation Training
See Microsoft Defender for Office 365 service description for detailed information on Plans 1 and 2.
Exchange Online Protection (EOP) is the cloud-based filtering service that protects your organization against spam, malware, phishing and other email threats.
EOP is included in all Microsoft 365 organizations that have Exchange Online mailboxes.
EOP is also available by itself to protect on-premises mailboxes and in hybrid environments to protect on-premises Exchange mailboxes. For more information, see Standalone Exchange Online Protection.
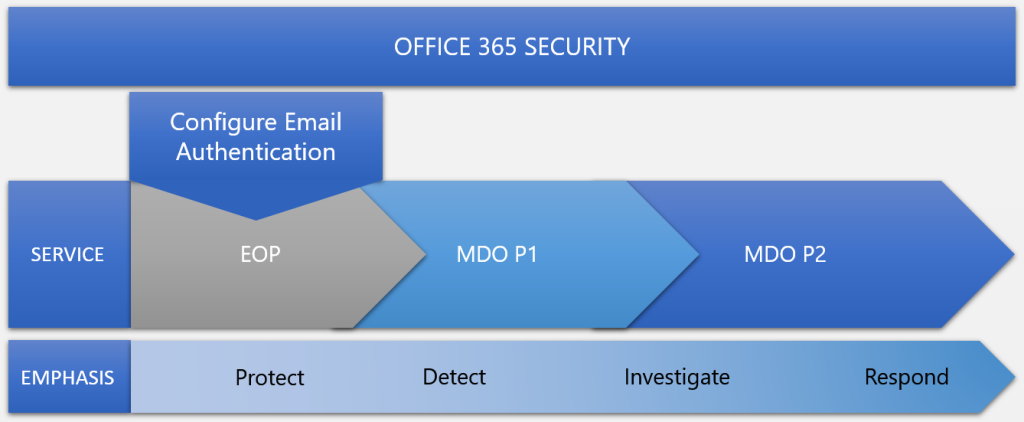
Source: https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/mdo-security-comparison
Though each of these services emphasizes a goal from among Protect, Detect, Investigate, and Respond, all the services can carry out any of the goals of protecting, detecting, investigating, and responding.
The core of Microsoft 365 security is EOP protection. Defender for Office 365 P1 contains EOP. Defender for Office 365 P2 contains P1 and EOP plus more features. The structure is cumulative. That’s why, when configuring this product, you should start with EOP and work up to Defender for Office 365 Plan 2.
Though email authentication configuration takes place in public DNS, it’s important to configure this feature to help defend against spoofing. If you have EOP, you should configure email authentication.
You can check which licenses are enabled in your Microsoft 365 tenant by using the following URL https://admin.microsoft.com/Adminportal/Home#/subscriptions which forwarded you to the Billing -> Your products blade.
Source: https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/mdo-security-comparison
About how to configure email authentication (DMARC, DKIM & SPF) you can also read my following posts.
Licenses / Subscriptions
If your subscription doesn’t include Defender for Office 365, you can get Defender for Office 365 as an add-on.
Defender for Office 365 is included in certain subscriptions. For example, Microsoft 365 E5, Office 365 E5, Office 365 A5, and Microsoft 365 Business Premium.
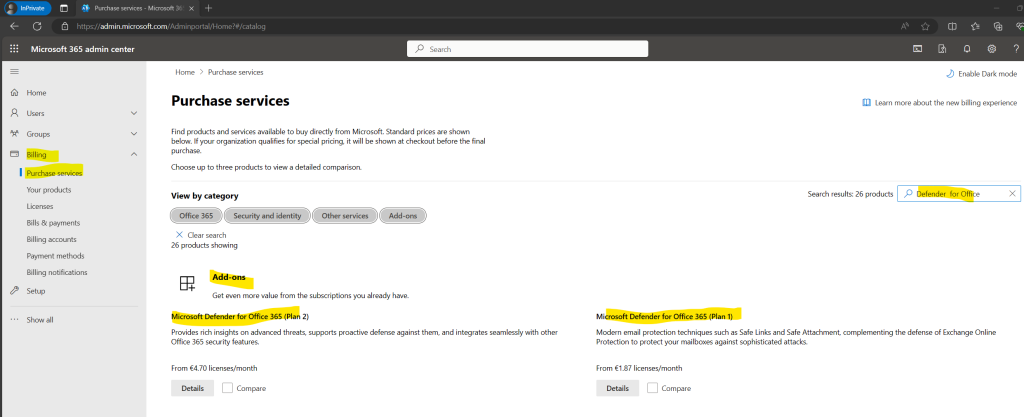
If you have for example a Microsoft 365 Business Basic subscription which doesn’t include Defender for Office 365, you can first check which apps and services included in your subscription by clicking the link shown below View apps and services included with this subscription.
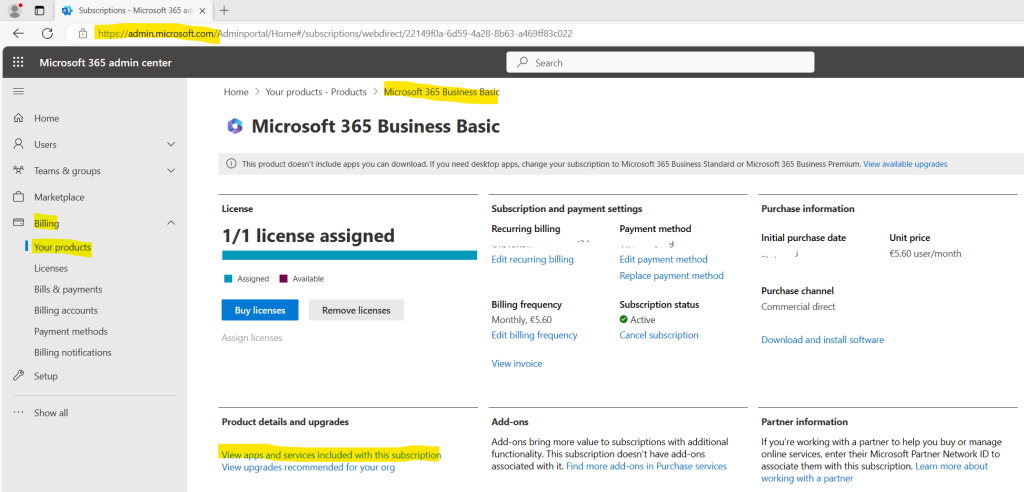
As already mentioned Exchange Online Protection (EOP) is included in all Microsoft 365 organizations that have Exchange Online mailboxes. In other words each subscription containing an Exchange Online Plan will also have included EOP.
Below you can see that the Microsoft 365 Business Basic and Standard subscription will also include the Exchange Online Plan 1. In contrast Microsoft 365 E3 and E5 for example will have included Exchange Online Plan 2.
Compare Exchange Online plans
https://www.microsoft.com/en-us/microsoft-365/exchange/compare-microsoft-exchange-online-plans
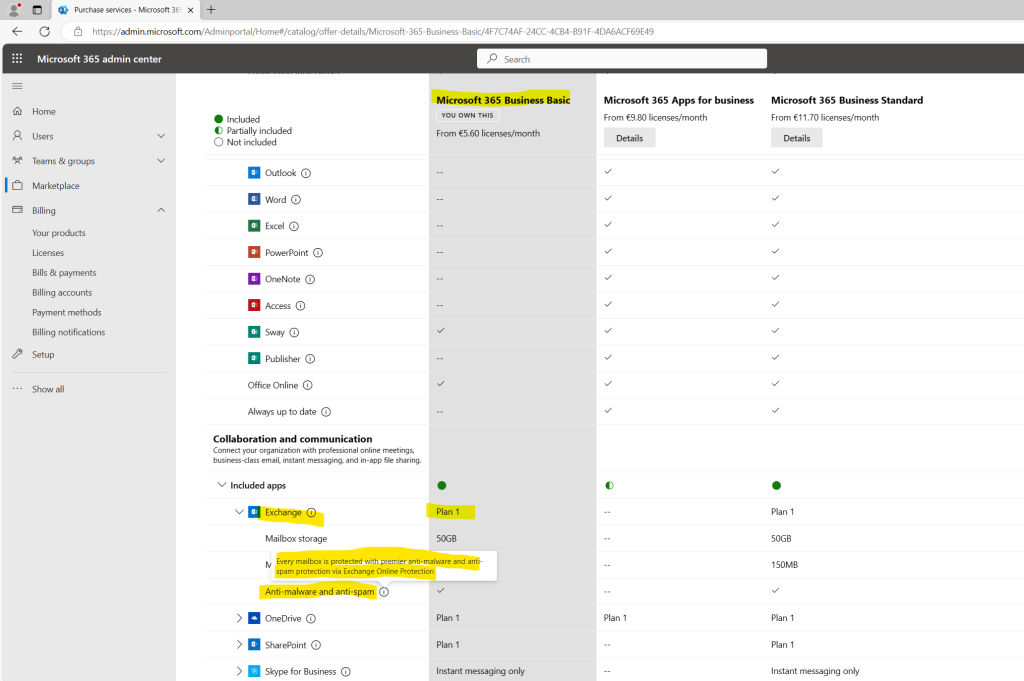
Here you can click on Add-ons to see all Add-ons which you can add to your existing subscription.
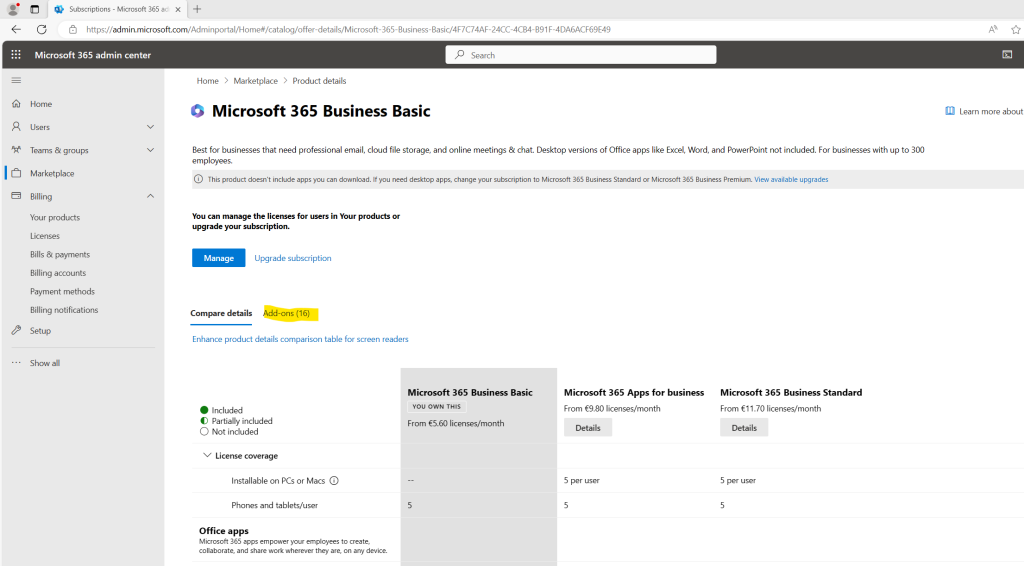
Because Defender for Office is not included in my Microsoft 365 Business Basic subscription, both Defender for Office Add-ons (Plan1 & Plan2) will be listed here and can be added to my existing subscription.
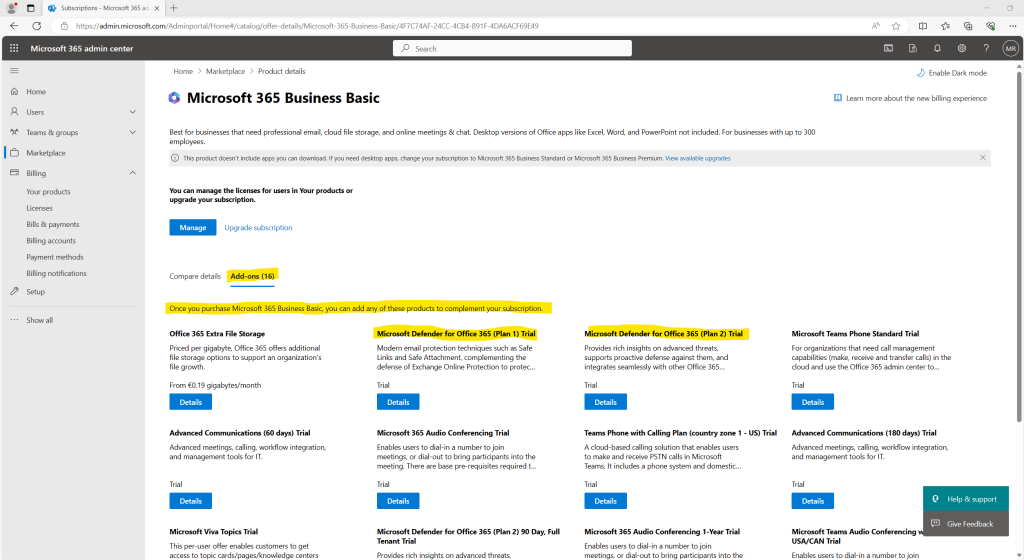
Source: https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security
Why adding a Defender for Office 365 Plan?
Because Exchange Online Protection (EOP) which is included by default in any subscription which contains an Exchange Online Plan, you may wonder what benefits you will have when adding in addition a Defender for Office 365 (Plan1 or Plan2) to your subscription in case not already included like when purchasing a Microsoft 365 E3 or E5 license.
Finally all three services, EOP, Defender for Office 365 Plan 1 and Plan 2 will cover protection-, detection-, investigation- and respond-attack features.
Defender for Office 365 P1 will expand the prevention features and adds extra forms of detection. Further it also adds Real-time detections for investigations.
Defender for Office 365 P2 will expand the investigation and response features and adds a new hunting strength: Automation.
The capabilities of all three services you will see in the following article https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/mdo-security-comparison?view=o365-worldwide#the-microsoft-365-security-ladder-from-eop-to-defender-for-office-365.
For example the presence of Real-time detections as a selection in the Microsoft 365 Defender portal means you have Defender for Office 365 P1 . If you will see instead the presence of Explorer (also known as Threat Explorer) it means you have Defender for Office 365 P2.
If your organization has Microsoft Defender for Office 365, and you have the permissions, you can use Explorer (also known as Threat Explorer) or Real-time detections to detect and remediate threats.
Because I have requested a Microsoft Defender for Office 365 (Plan 2) 90 Day, Full Tenant Trial for my tenant, I can select below the Explorer (also known as Threat Explorer) feature by clicking on Explorer.
Explorer is only included in Defender for Office 365 Plan 2.
The Real-time detections report is included in Defender for Office 365 Plan 1.
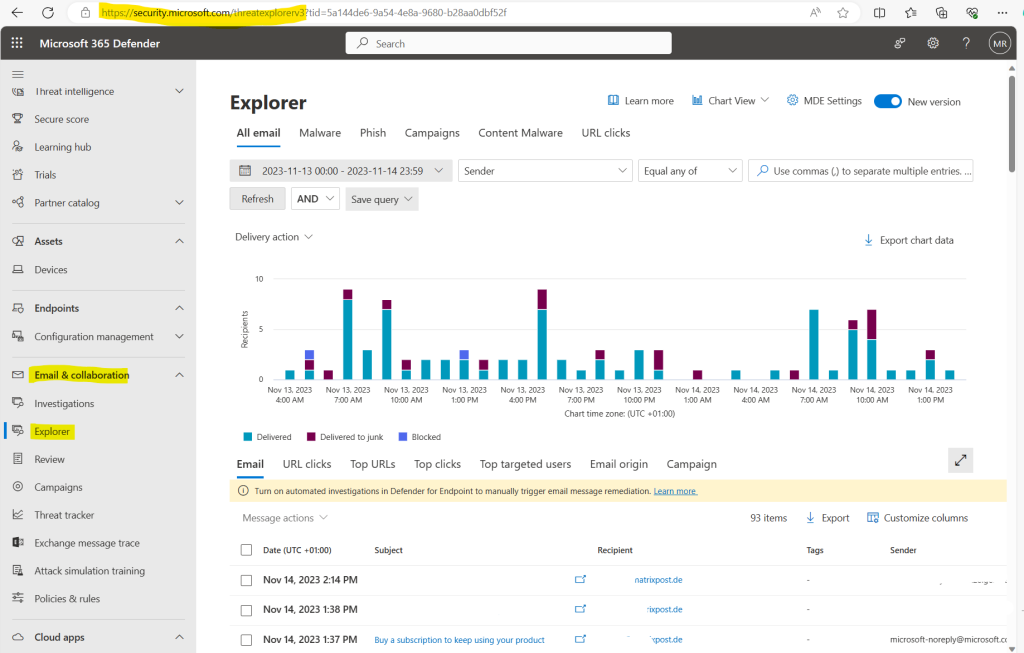
In the Microsoft 365 Defender portal at https://security.microsoft.com, go to Email & collaboration, and then choose Explorer or Real-time detections. To go directly to the page, use https://security.microsoft.com/threatexplorer or https://security.microsoft.com/realtimereports.
With these tools, you can:
- See malware detected by Microsoft 365 security features.
- View phishing URL and click verdict data.
- Start an automated investigation and response process from a view in Explorer.
- Investigate malicious email, and more.
For more information, see Email security with Explorer.
Here for example you can see my lab tenant without Microsoft Defender for Office 365 has much less menu items within the Email & collaboration menu.
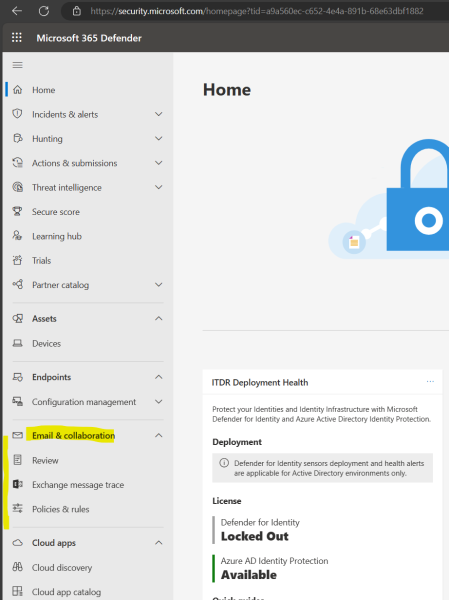
Differences between Explorer and Real-time detections
- Real-time detections is a reporting tool available in Defender for Office 365 Plan 1. Threat Explorer is a threat hunting and remediation tool available in Defender for Office 365 Plan 2.
- The Real-time detections report allows you to view detections in real time. Threat Explorer does this as well, but it provides additional details for a given attack, such as highlighting attack campaigns, and gives security operations teams the ability to remediate threats (including triggering an Automated Investigation and Response investigation.
- An All email view is available in Threat Explorer, but not included in the Real-time detections report.
- Rich filtering capabilities and remediation actions are included in Threat Explorer. For more information, see Microsoft Defender for Office 365 Service Description: Feature availability across Defender for Office 365 plans.
Microsoft Defender for Office 365 step-by-step guide
To configure and deploy Microsoft Defender for Office 365 we can also use the following Microsoft Defender for Office 365 step-by-step guide which will provides us with the same best practices that Microsoft 365 FastTrack onboarding specialists share in individual interactions.
All advanced deployment guides are available in the Microsoft 365 admin center as described in the section below, and most guides can also be found in the Microsoft 365 Setup portal.
!!! Note !!!
This guides will not really perform the actual configuration and setup, it will just guides you through each step to setup and configure the services with additional information where and what you can configure all.
To start the guide first navigate to Setup within the Microsoft 365 admin center.
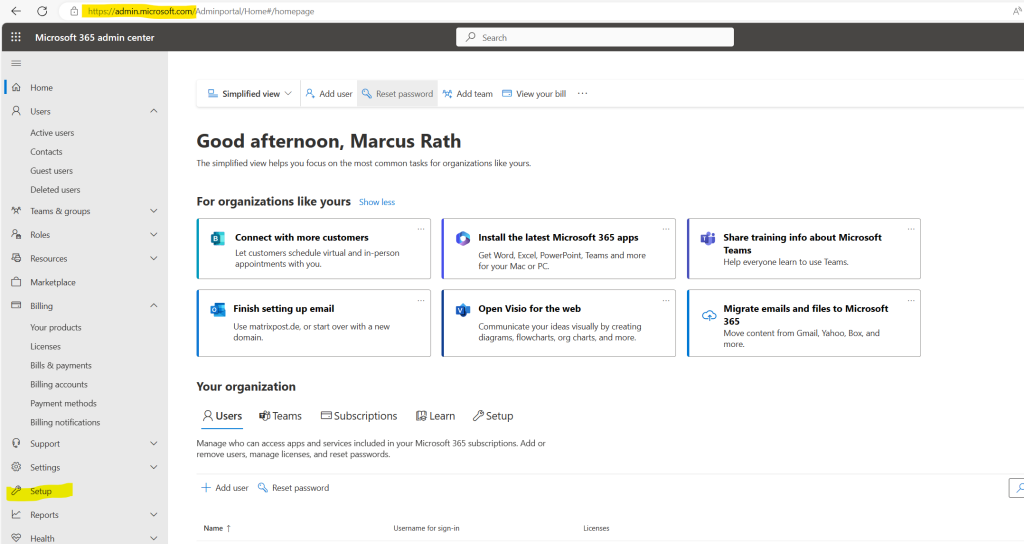
Then select Advanced deployment guides & assistance.
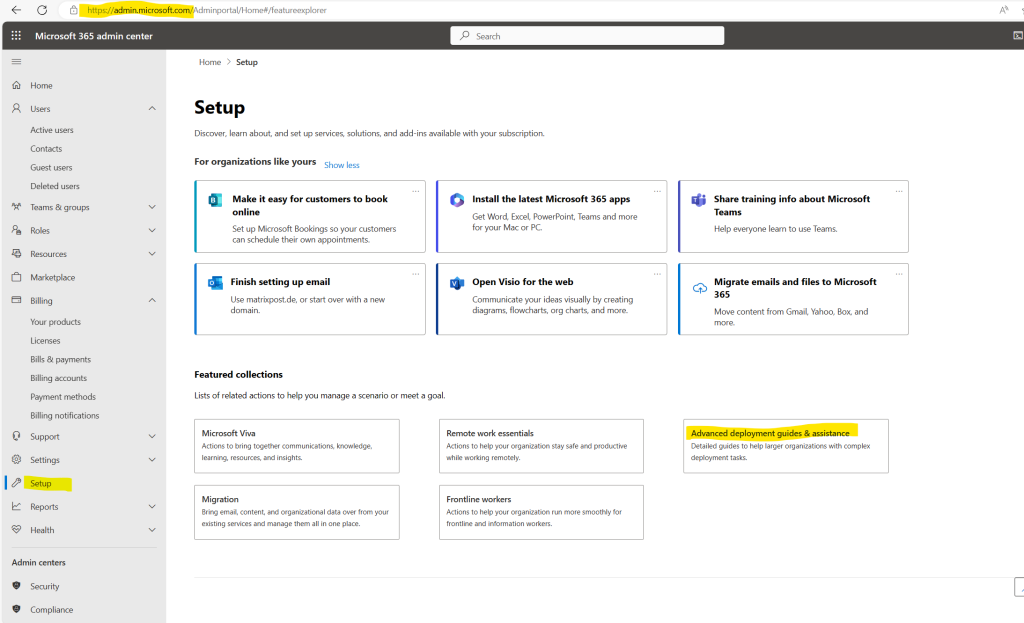
Select All guides and scroll down to the Security section, here we select Microsoft Defender for Office 365 setup guide.
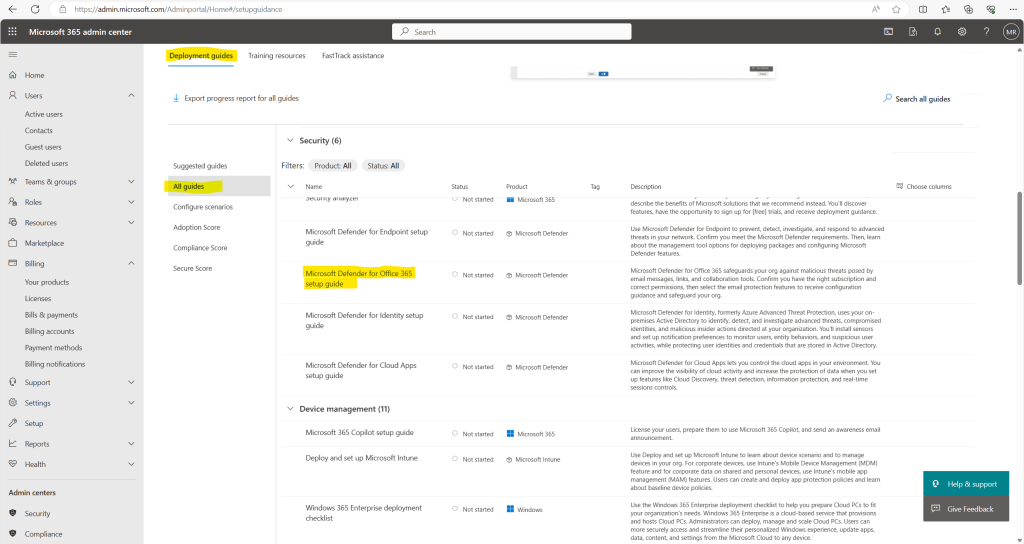
This guide will configure (resp. will guide us to configure) Defender for Office 365 according to Microsoft best practices and provide optional configurations to help optimize and secure your environment.
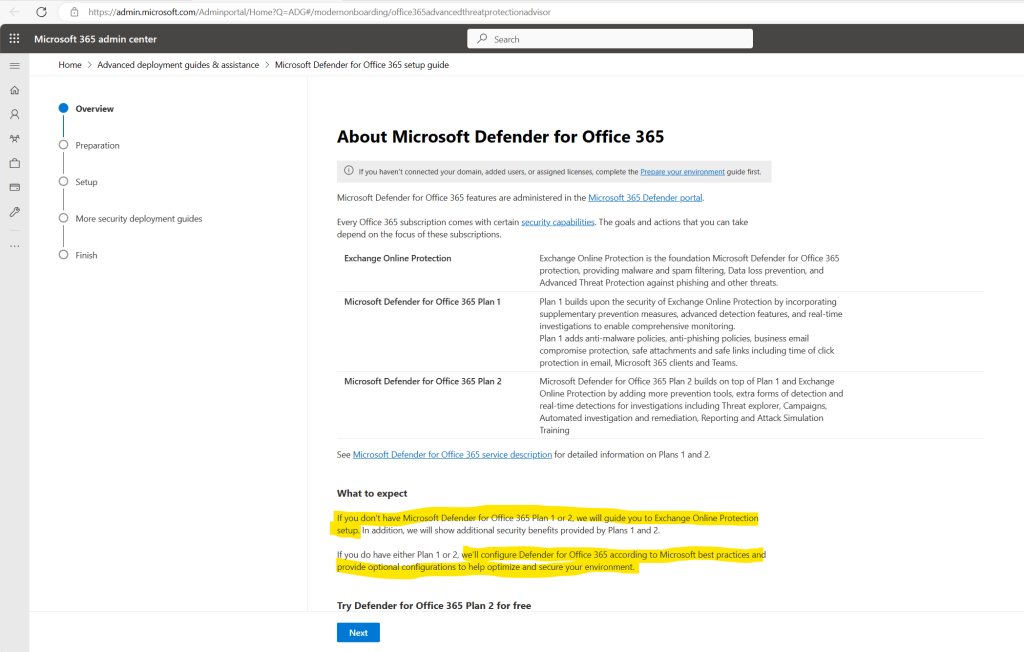
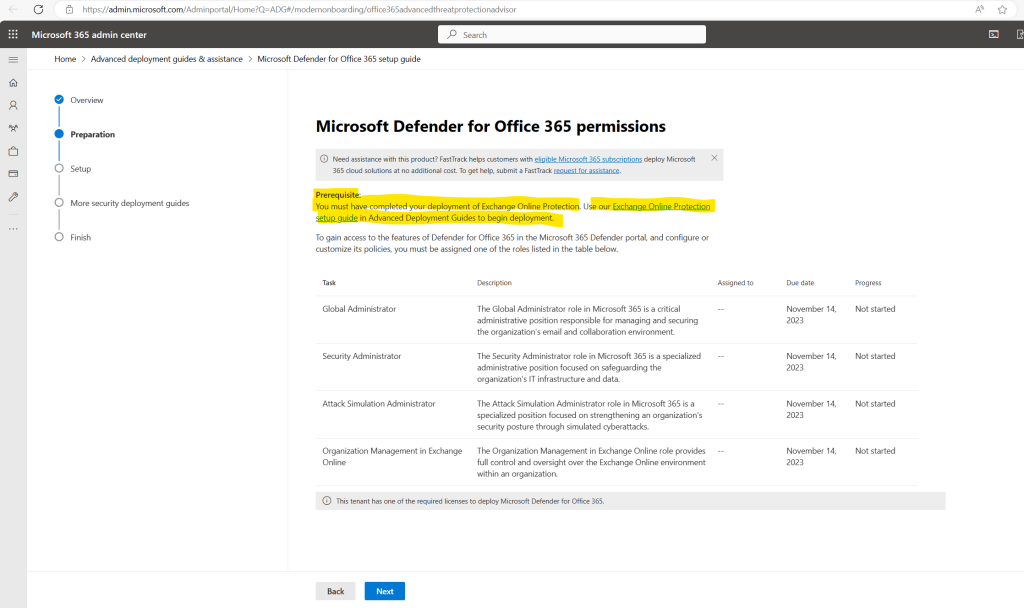
I have requested a Microsoft Defender for Office 365 (Plan 2) Trial license for my tenant, in order to setup Microsoft Defender for Office 365, I will first have to complete the deployment of Exchange Online Protection as shown below.
As already mentioned, this is just a guide which will navigate us through each step to setup and configure Microsoft Defender for Office 365. Therefore its finally just a recommendation to first configure Exchange Online Protection before we processing to configure Microsoft Defender for Office 365.
To go step by step I will therefore click on the link below to start the Exchange Online Protection setup guide.
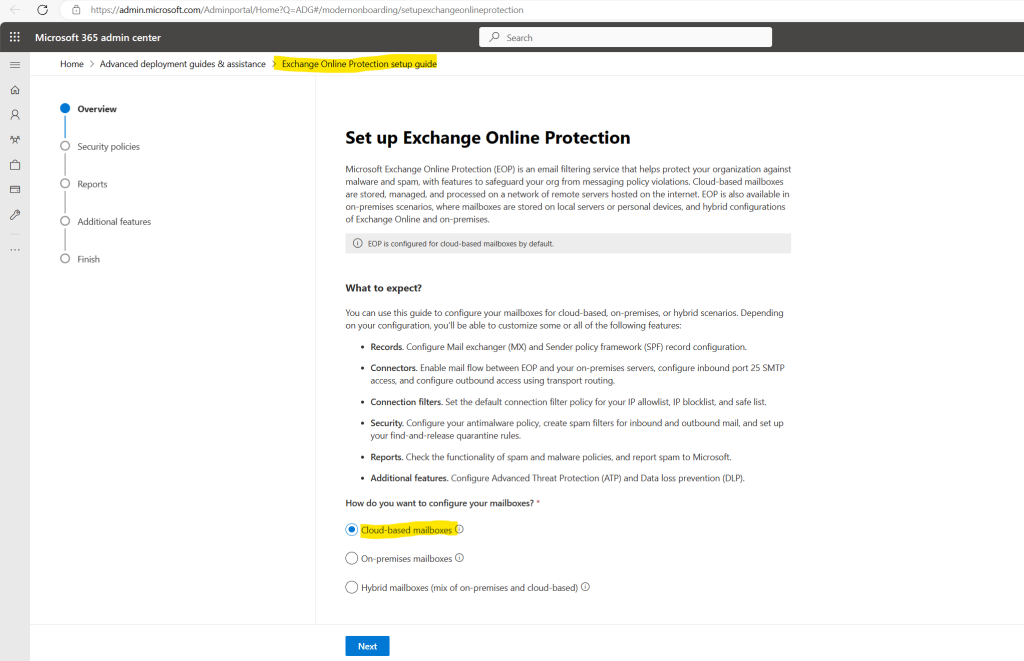
My private tenant is cloud only and therefore I will just have to configure EOP for cloud-based mailboxes.
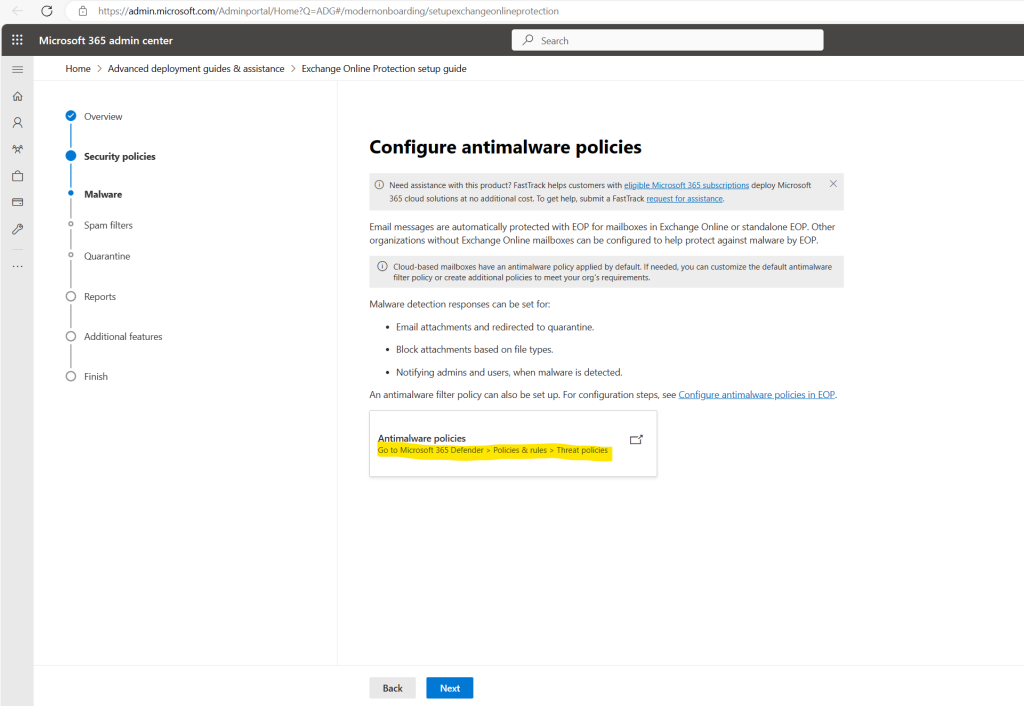
Cloud-based mailboxes have an antimalware policy applied by default. If needed, you can customize the default antimalware filter policy or create additional policies to meet your org’s requirements.
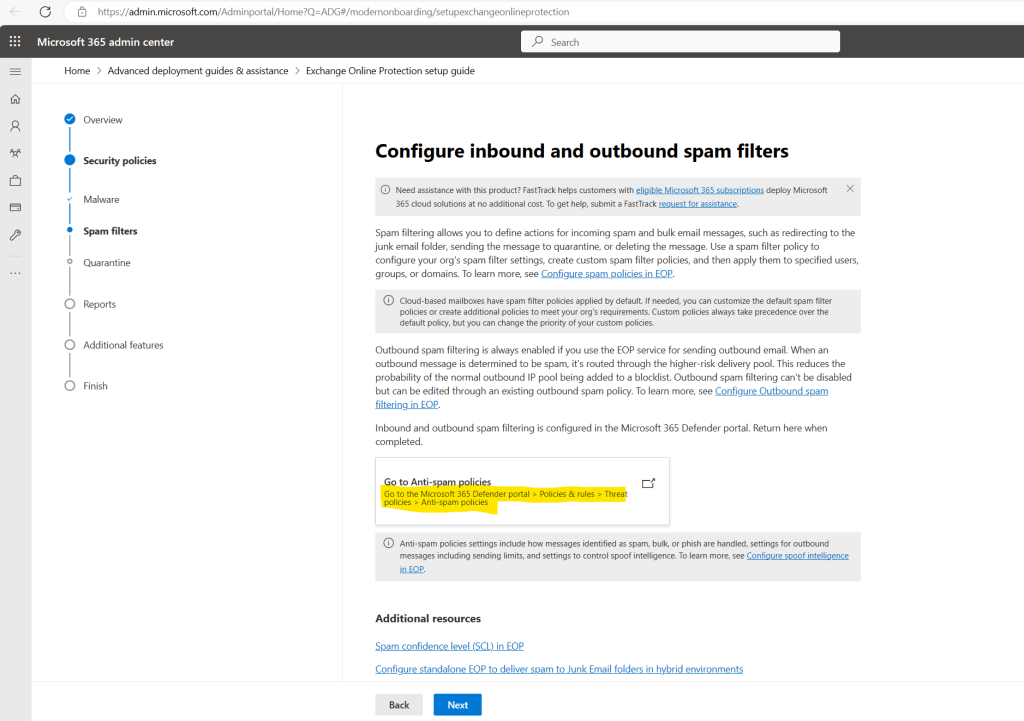
Cloud-based mailboxes have spam filter policies applied by default. If needed, you can customize the default spam filter policies or create additional policies to meet your org’s requirements. Custom policies always take precedence over the default policy, but you can change the priority of your custom policies.
Both admins and users can release messages in their specific quarantine mailbox. For added security, admins receive notifications when users have released items from their quarantine mailboxes.
The Microsoft 365 Defender portal includes capabilities that help protect your environment. It also includes reports and dashboards you can use to monitor and take action. Some areas come with default policy configurations.
Here you will get just informed about additional security features available for your subscription.
Finally we have completed the guide for Exchange Online Protection (EOP) and can click on Done.
Now we can resume the Microsoft Defender for Office 365 setup guide as all prerequisites are fulfilled by clicking on Next.
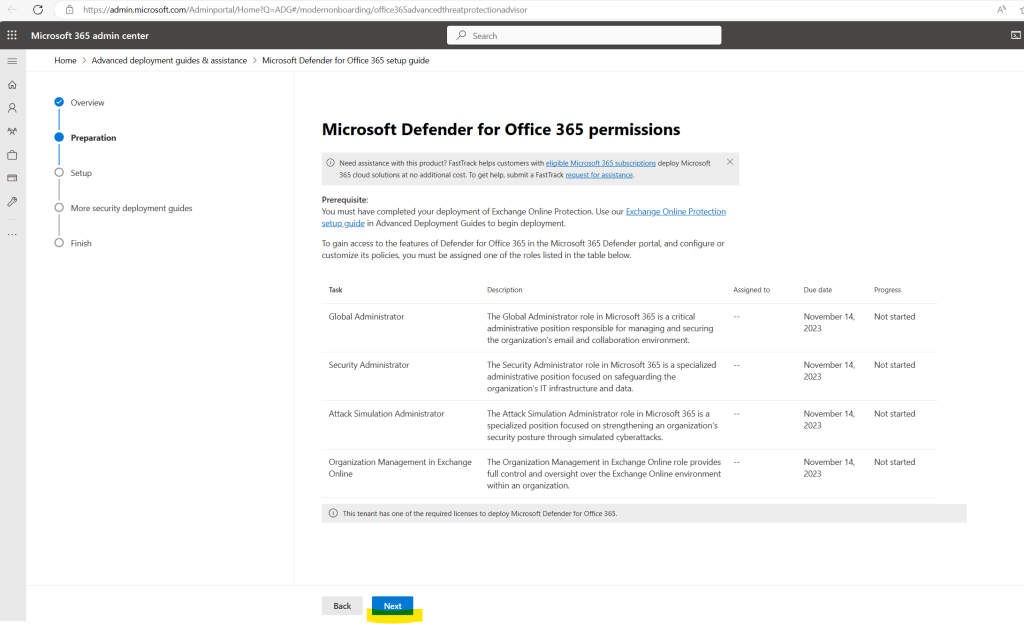
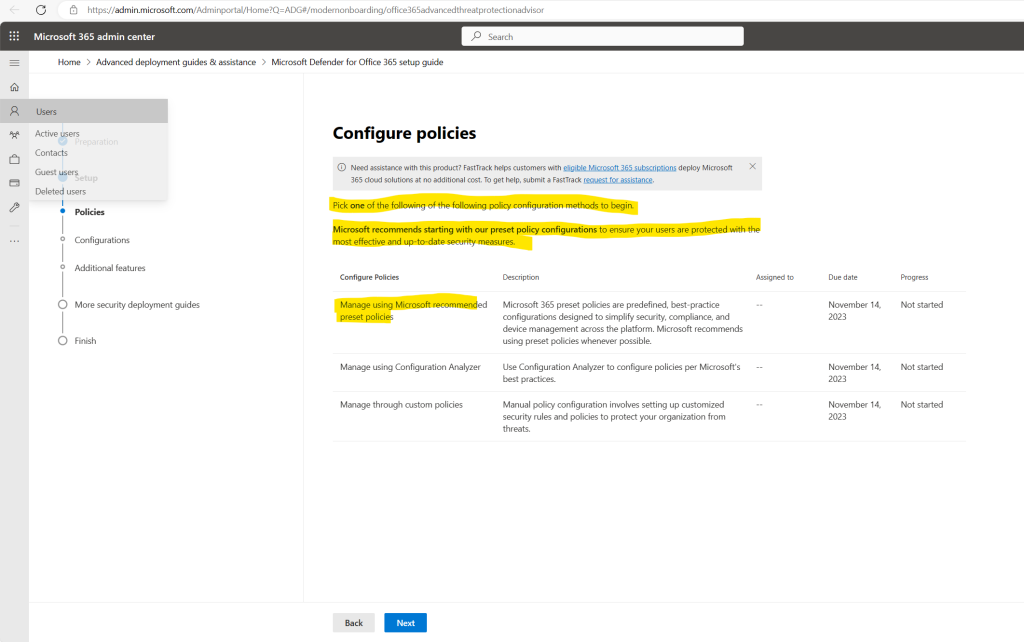
I will use here as recommended the Microsoft preset policies.
Microsoft 365 preset policies are predefined, best-practice configurations designed to simplify security, compliance, and device management across the platform. Microsoft recommends using preset policies whenever possible.
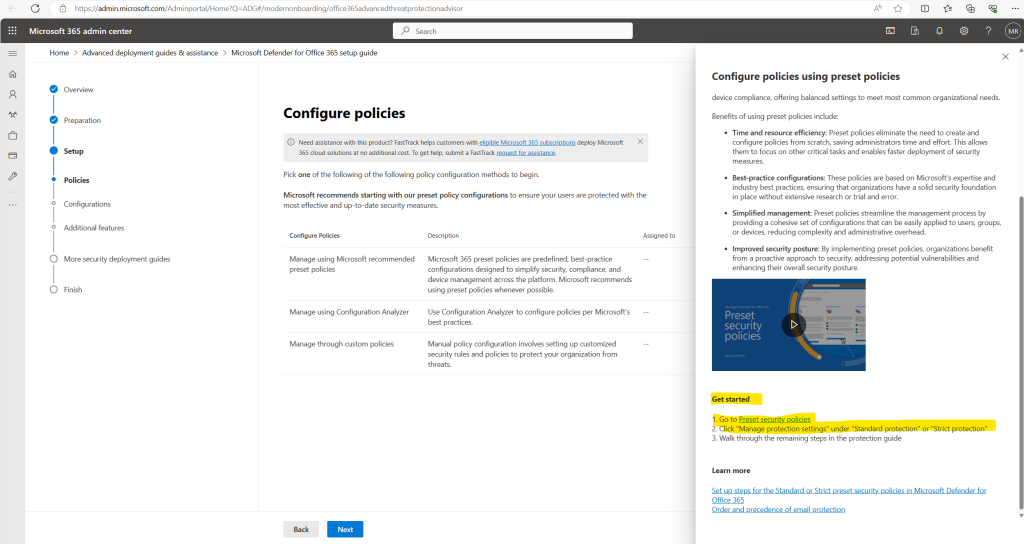
To configure preset policies we need to navigate to Email & colaboration -> Policies & rules -> Threat policies -> Preset Security Policies or by clicking on the link below in the guide.
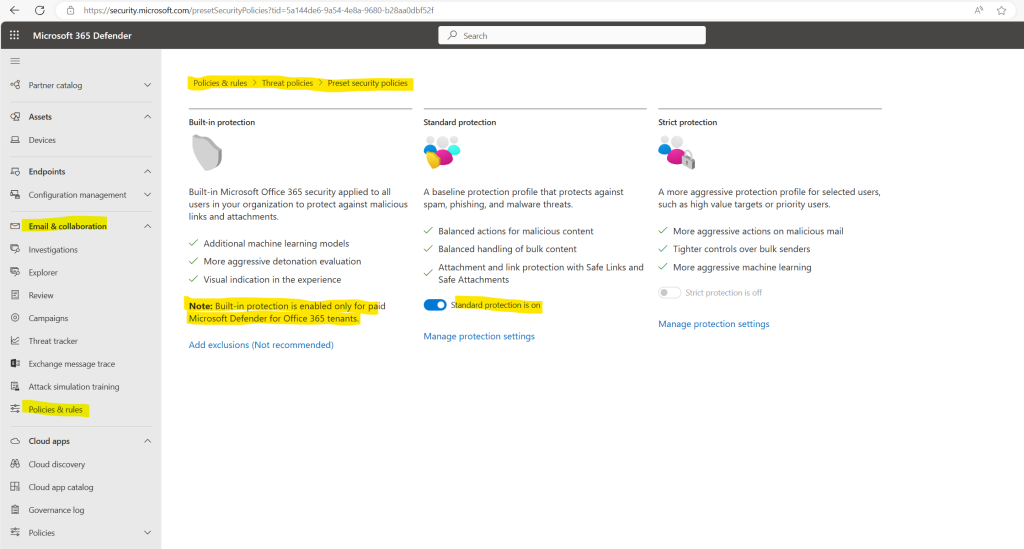
By default built-in protection is applied to all users in your organization.
Built-in protection offers a base level of unobtrusive protection, and includes malware, zero day (Safe Attachments), and URL protection (Safe Links) in email (including internal email), SharePoint Online, OneDrive, and Teams. Note that URL protection provided in this state is via API call only. It doesn’t wrap or rewrite URLs but does require a supported Outlook client. You can create your own custom policies to expand your protection.
Click here on Manage protection settings under Standard protection or Strict protection and walk through the remaining steps.
I will configure below the standard protection. Select All Recipients to apply Exchange Online Protection tenant wide, or select Specific recipients to manually add users, groups, or domains you want to apply the protection policy to. Click the Next button.
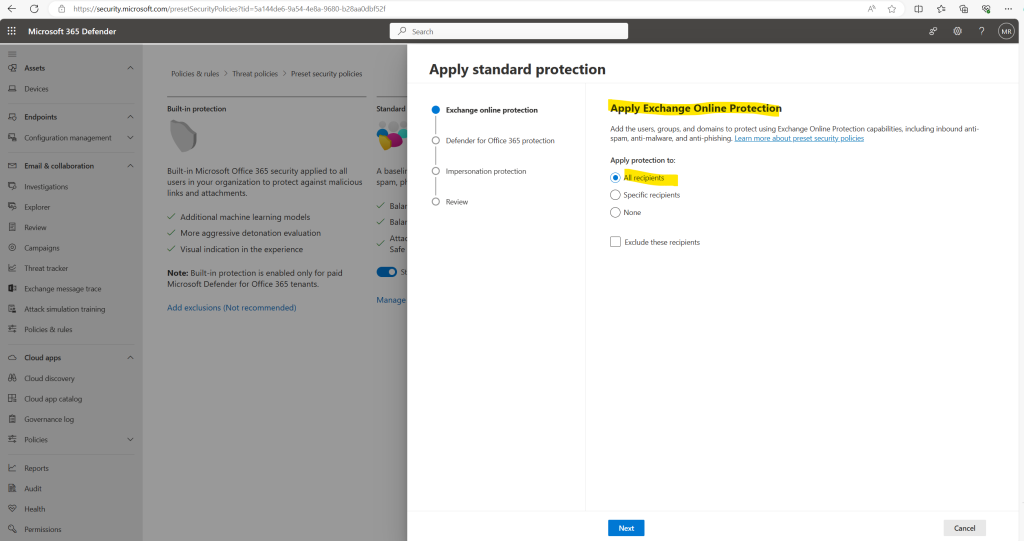
Select All Recipients to apply Defender for Office 365 Protection tenant wide, or select Specific recipients to manually add add users, groups, or domains you want to apply the protection policy to. Click the Next button.
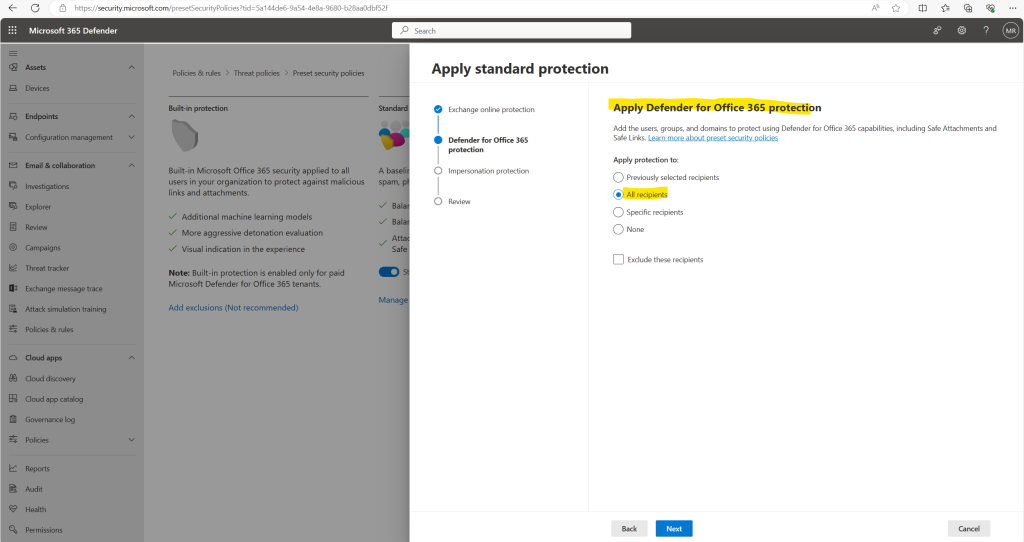
In this final step for standard protection we can also configure additional impersonation protection.
The default anti-phishing policy automatically applies to all recipients. For greater granularity, you can also create custom anti-phishing policies that apply to specific users, groups, or domains in your organization.
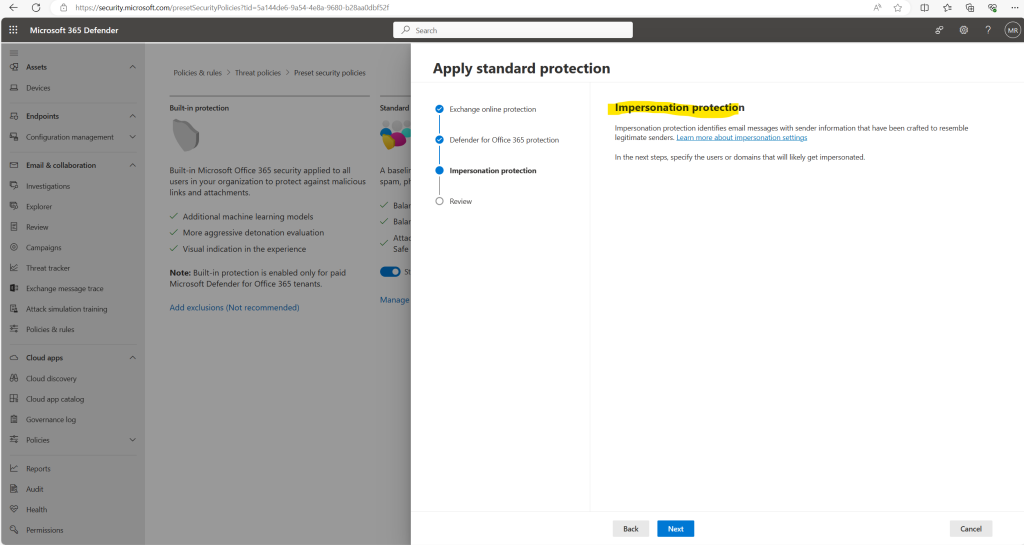
For more information about these settings, see Impersonation settings in anti-phishing policies in Microsoft Defender for Office 365. To configure these settings, see Configure anti-phishing policies in Defender for Office 365.
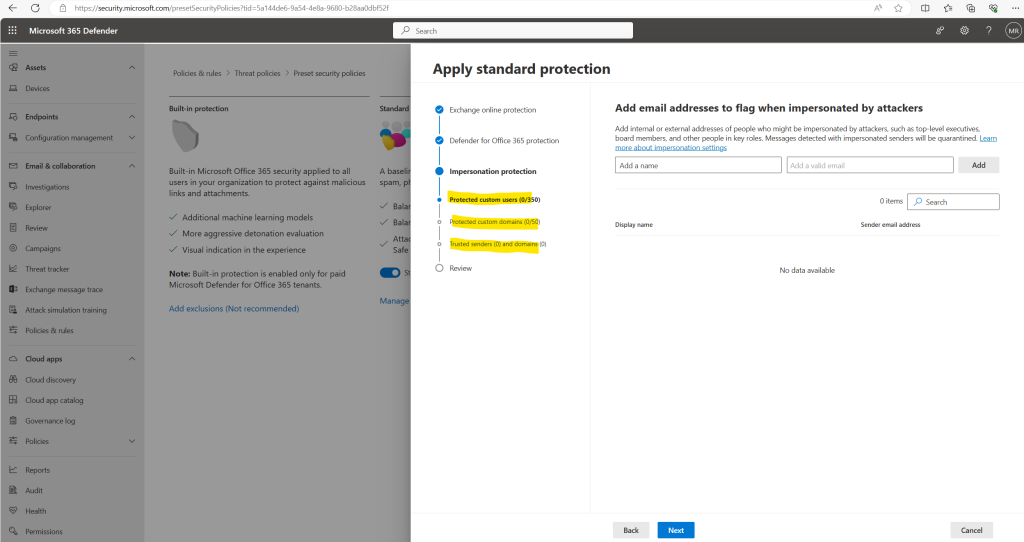
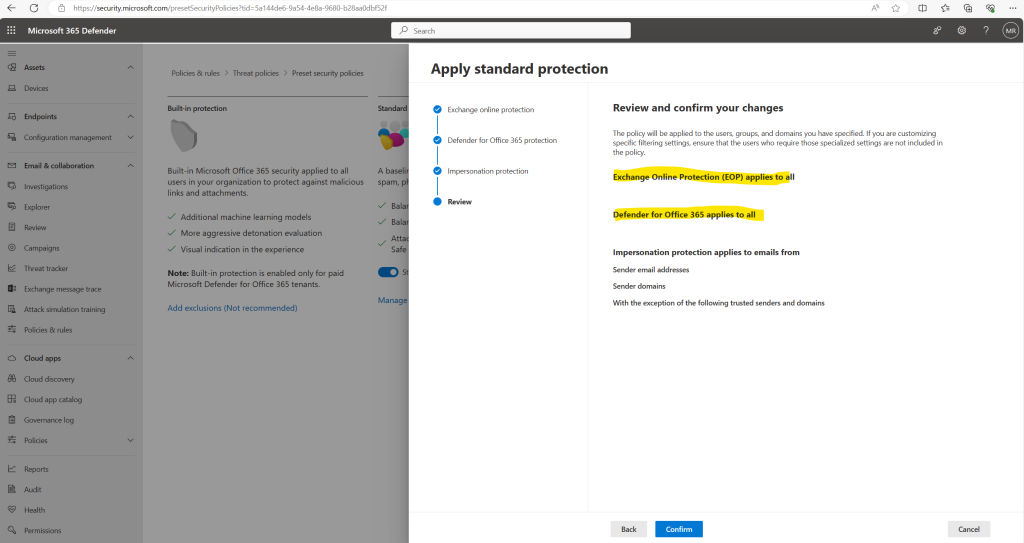
In the next step of the guide we can configure Microsoft 365 Defender for Office 365 features.
The following features are included in your Microsoft 365 Defender for Office 365 plan. For a more detailed list of plan features, see Microsoft Defender for Office 365 service description.
I will skip these steps for now.
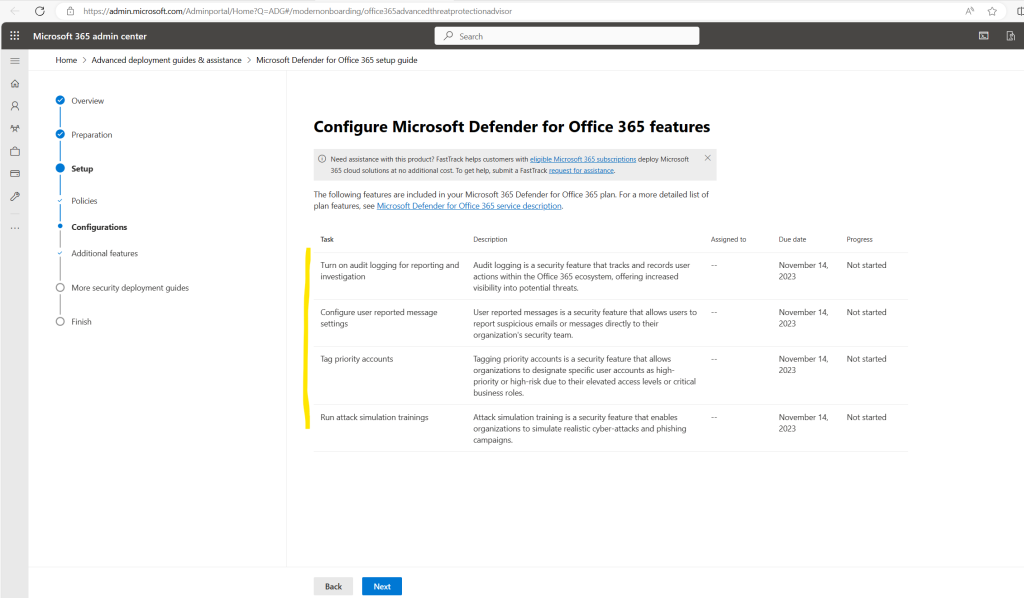
The next step will guide you through the configuration of additional features, you can also see here in brackets which plan includes this feature.
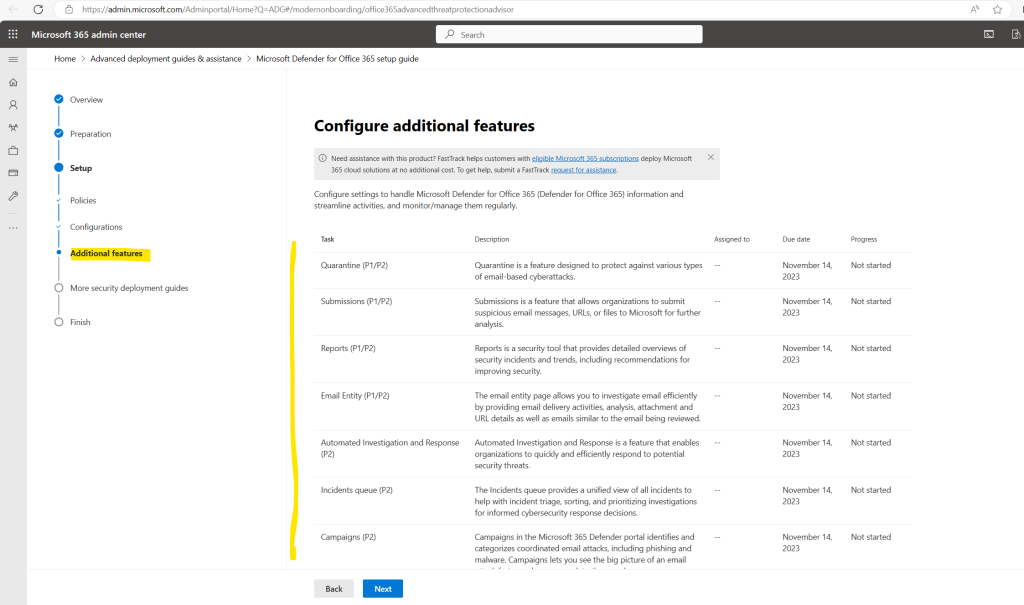
Before the guide is completed it will show some additional guides about securing Microsoft 365 and Azure.
Finally the guide will give us some additional resources about securing our cloud environment.
In the following article you will find many resources to get a deeper insight into Microsoft Defender for Office 365.
Become a Microsoft Defender for Office 365 Ninja! | June 2022
https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/become-a-microsoft-defender-for-office-365-ninja-june-2022/ba-p/2187392
Related Posts about Exchange Online Protection (EOP) and Policies
You are maybe also interested in one of the following posts.
Links
Microsoft Defender for Office 365 overview
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/mdo-about?view=o365-worldwideGet started with Microsoft Defender for Office 365
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/mdo-deployment-guideExchange Online Protection overview
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/eop-about?view=o365-worldwideMicrosoft Defender for Office 365 security comparison
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/mdo-security-comparisonEmail authentication in EOP
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/email-authentication-aboutWelcome to the Microsoft Defender for Office 365 step-by-step guides
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/step-by-step-guides/step-by-step-guide-overviewBecome a Microsoft Defender for Office 365 Ninja! | June 2022
https://techcommunity.microsoft.com/t5/microsoft-defender-for-office/become-a-microsoft-defender-for-office-365-ninja-june-2022/ba-p/2187392What is Threat Explorer and Real-time detections?
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/real-time-detections
Tags In
Follow me on LinkedIn


