Enable TLS for Postfix on Ubuntu
Regarding the Postfix documentation, TLS support is turned off by default, so you can start using Postfix as soon as it is installed.
On newer Ubuntu versions TLS is enabled by default and these lines:
(You can check your version by using the command postconf mail_version)
Besides checking directly the main.cf file, you can also check the following parameters with the postconf command, by default it displays the values of the main.cf configuration file.
Source: https://www.postfix.org/postconf.1.html
# SMTPD TLS configuration for inbound connections
smtpd_tls_security_level=may
# SMTP TLS configuration for outbound connections
smtp_tls_security_level=may
may –> Opportunistic TLS: announce STARTTLS support to remote SMTP clients, but do not require that clients use TLS encryption.
Source: https://www.postfix.org/TLS_README.html#server_enable
Default TLS Configuration on Postfix
By default the TLS configuration looks like below after a new installation from Postfix on Ubuntu. Postfix will use here by default the self-signed default snake oil certificates that comes with Ubuntu.
You can change this certificate of course with a public trusted one, if you want to avoid warning messages when connnecting with a client. Encrypted communication between SMTP servers and by using Opportunistic TLS, also works with self-signed certificates. Here it is more important that email messages are encrypted between the SMTP servers instead to authenticate and identify each peer.
smtpd_use_tls=yes is replaced by smtpd_tls_security_level=may since version >= 2.3.
With smtpd_tls_security_level=may, the Postfix SMTP server announces STARTTLS support to remote SMTP clients, but does not require that clients use TLS encryption.
You can ENFORCE the use of TLS, so that the Postfix SMTP server announces STARTTLS and accepts no mail without TLS encryption, by setting smtpd_tls_security_level = encrypt. According to RFC 2487 this MUST NOT be applied in case of a publicly-referenced Postfix SMTP server. This option is off by default and should only seldom be used.
Source: https://www.postfix.org/postconf.5.html#smtpd_tls_security_level
Determine if Postfix already using TLS encryption
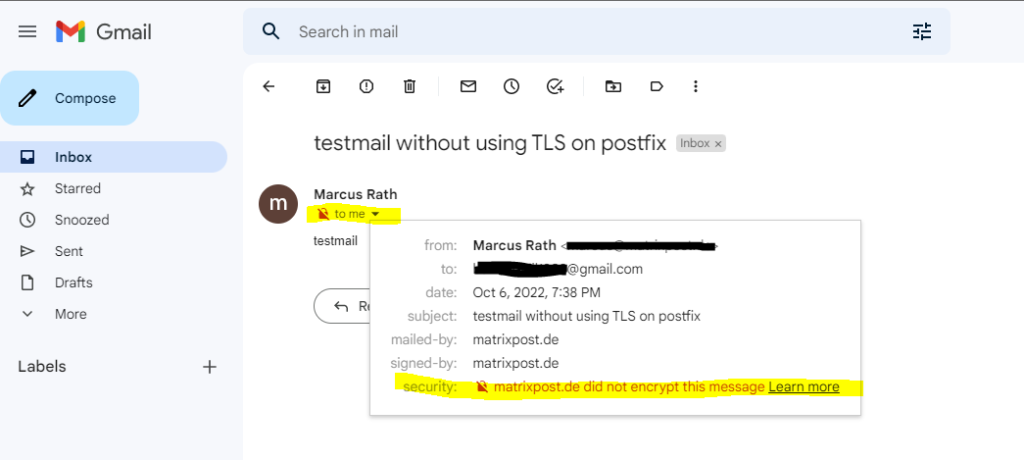
An easy way to check if postfix send email messages encrypted to the destination email server, is when you had an Gmail account to just look in your inbox as shown below.
Sending email message from my postfix server to Gmail where TLS is not enabled!
The parameter smtp_tls_security_level ( in the main.cf file is missing or none, in that case TLS will not be used.
Enable TLS on Postfix
Enable TLS by adding the following line to your etcpostfixmain.cf file.
# SMTP TLS configuration for outbound connections
smtp_tls_security_level = may
SMTPD TLS configuration for inbound connections
smtpd_tls_security_level = may
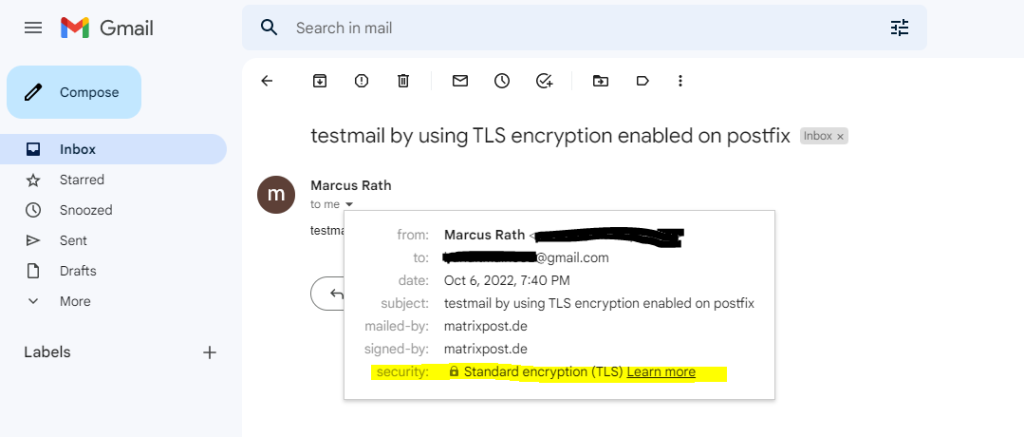
By setting the parameter below for outbound connections,
smtp_tls_received_header = yes
you can also check if the email message was encrpyted by postfix in the E-Mail header as shown below
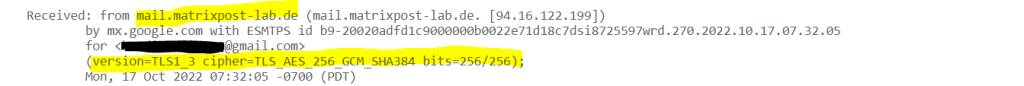
For inbound connections use
smtpd_tls_received_header = yes
SMTPD TLS configuration for inbound connections
# SMTPD TLS configuration for inbound connections
smtpd_tls_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
smtpd_tls_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
smtpd_tls_protocols = !SSLv2, !SSLv3
# Enable Opportunistic TLS
smtpd_tls_security_level = may
smtpd_tls_auth_only = yes
smtpd_tls_loglevel = 2
tls_random_source = dev:/dev/urandom
# displays TLS information in the E-Mail header
smtpd_tls_received_header = yes
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
Below each parameter is explained …
smtpd_tls_cert_file
https://www.postfix.org/postconf.5.html#smtpd_tls_cert_file
On Ubuntu by default the self-signed snakeoil certificates will be configured for postfix automatically which is valid for 10 years.
You can renew the default snakeoil certificate by running the following command:
$ sudo make-ssl-cert generate-default-snakeoil –force-overwrite
Path:
/etc/ssl/certs/ssl-cert-snakeoil.pem
/etc/ssl/private/ssl-cert-snakeoil.key
make-ssl-cert is a simple debconf to openssl wrapper to create self-signed certificates.
Source: https://manpages.ubuntu.com/manpages/bionic/man8/make-ssl-cert.8.html
In short you can use the script to simplify the creation of a self signed certificate by openssl. Finally this part from the make-ssl-cert script will create the certificate by using OpenSSL.
elif [ “${subcommand}” = “generate-default-snakeoil” ]; then
if ! openssl req -config “${TMPFILE}” -new -x509 -days “${opt_expiration_days}” -nodes -sha256
-out /etc/ssl/certs/ssl-cert-snakeoil.pem
-keyout /etc/ssl/private/ssl-cert-snakeoil.key > “${TMPOUT}” 2>&1
Btw. the expiration date you can change in the /usr/sbin/make-ssl-cert script at about line 125 and the following parameter: opt_expiration_days=”3650″
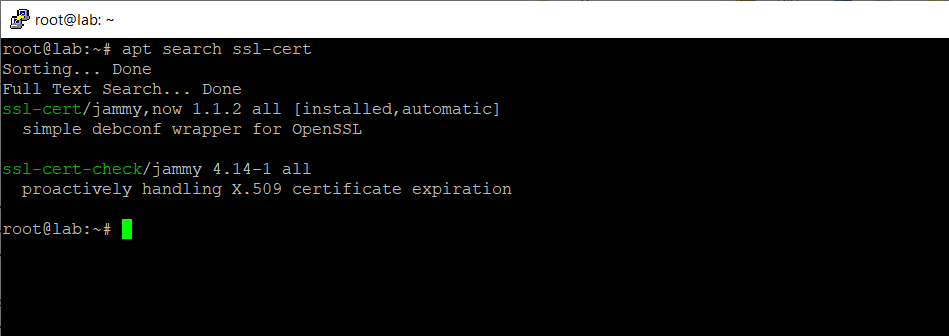
To check if ssl-cert is already installed, by default it is preinstalled on Ubuntu.
$ sudo apt search ssl-cert
smtpd_tls_protocols
https://www.postfix.org/postconf.5.html#smtpd_tls_protocols
TLS protocols accepted by the Postfix SMTP server with opportunistic TLS encryption. If the list is empty, the server supports all available TLS protocol versions. A non-empty value is a list of protocol names to include or exclude, separated by whitespace, commas or colons.
With Postfix < 3.6 there is no support for a minimum or maximum version, and the protocol range is configured via protocol exclusions. To require at least TLS 1.0, set smtpd_tls_protocols = !SSLv2, !SSLv3
smtpd_tls_auth_only = no
https://www.postfix.org/TLS_README.html#server_tls_auth
To maintain compatibility with non-TLS clients, the default is to accept AUTH without encryption. In order to change this behavior, set smtpd_tls_auth_only = no
smtpd_tls_loglevel
https://www.postfix.org/postconf.5.html#smtpd_tls_loglevel
smtpd_tls_session_cache_database
https://www.postfix.org/TLS_README.html#server_tls_cache
The Postfix SMTP server and the remote SMTP client negotiate a session, which takes some computer time and network bandwidth. SSL protocol versions other than SSLv2 support resumption of cached sessions. Not only is this more CPU and bandwidth efficient, it also reduces latency as only one network round-trip is used to resume a session while it takes two round-trips to create a session from scratch.
SMTP TLS configuration for outbound connections
# SMTP TLS configuration for outbound connections
smtp_tls_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
smtp_tls_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
smtp_tls_protocols = !SSLv2, !SSLv3
smtp_tls_auth_only = yes
# Enable Opportunistic TLS
smtp_tls_security_level = may
# displays TLS information in the E-Mail header
smtp_tls_received_header = yes
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
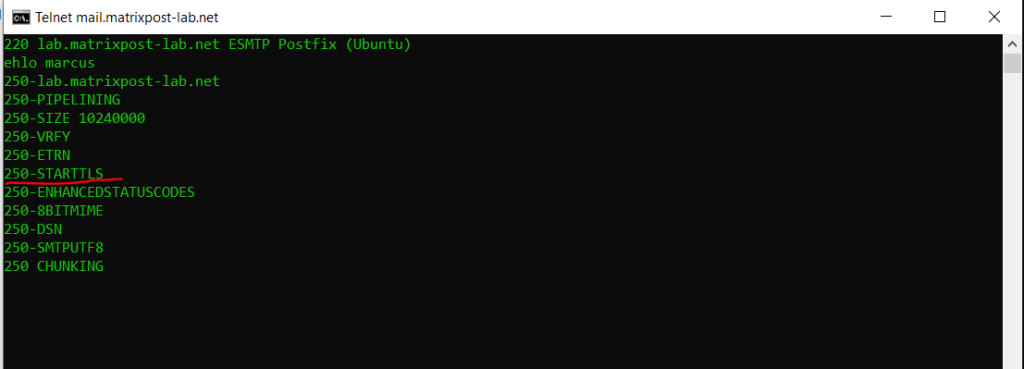
You can also check if postfix will support TLS by using telnet and openssl.
> telnet mail.matrixpost-lab.de 25
ehlo <normally the FQDN from the sending server, but here you can enter what you want for testing>
The STARTTLS keyword is used to tell the SMTP client that the SMTP server is currently able to negotiate the use of TLS.
Source: https://datatracker.ietf.org/doc/html/rfc3207#section-3
Opportunistic TLS (Transport Layer Security) refers to extensions in plain text communication protocols, which offer a way to upgrade a plain text connection to an encrypted (TLS or SSL) connection instead of using a separate port for encrypted communication. Several protocols use a command named “STARTTLS” for this purpose.
Source: https://en.wikipedia.org/wiki/Opportunistic_TLS
OpenSSL for Windows
https://slproweb.com/products/Win32OpenSSL.html
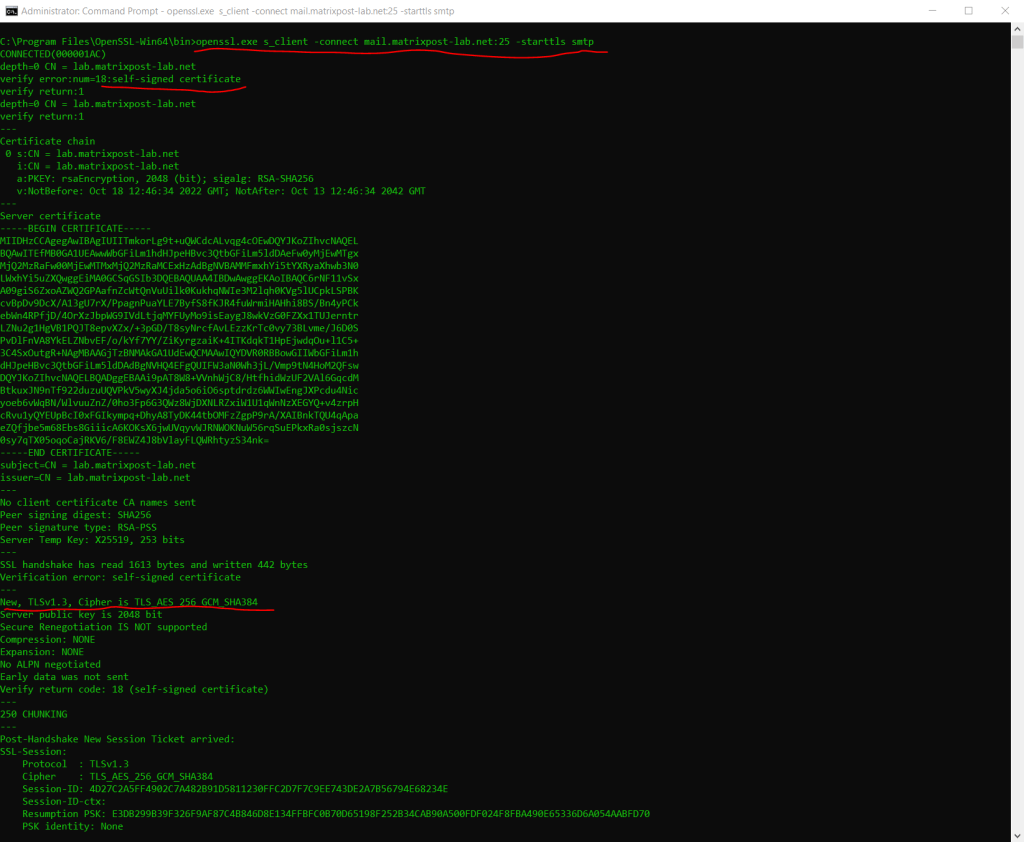
By using OpenSSL you can also check the TLS connection and the server certificate from postfix or other SMTP servers with the following command.
> openssl.exe s_client -connect mail.matrixpost-lab.net:25 -starttls smtp
Links
The Postfix Home Page
https://www.postfix.org/
OpenSSL for Windows
https://slproweb.com/products/Win32OpenSSL.html



