What is Microsoft Entra Permissions Management?
Microsoft Entra Permissions Management is a cloud infrastructure entitlement management (CIEM pronounced kim) solution that provides comprehensive visibility into permissions assigned to all identities. For example, over-privileged workload and user identities, actions, and resources across multicloud infrastructures in Microsoft Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP).
Permissions Management detects, automatically right-sizes, and continuously monitors unused and excessive permissions.
Organizations have to consider permissions management as a central piece of their Zero Trust security to implement least privilege access across their entire infrastructure.
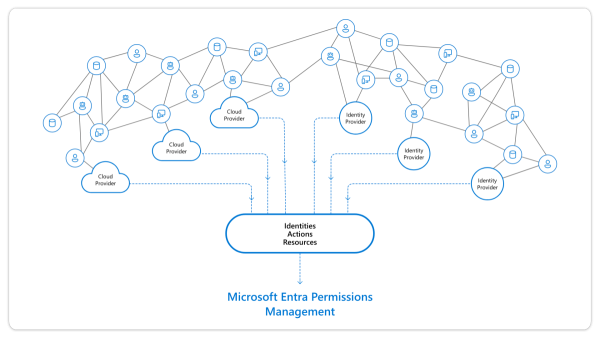
Permissions Management allows customers to address three key use cases:
- discover
- remediate
- monitor
We will take a look at them below.
Discover
Customers can assess permission risks by evaluating the gap between permissions granted and permissions used.
- Cross-cloud permissions discovery: Granular and normalized metrics for key cloud platforms: AWS, Azure, and GCP.
- Permission Creep Index (PCI): An aggregated metric that periodically evaluates the level of risk associated with the number of unused or excessive permissions across your identities and resources. It measures how much damage identities can cause based on the permissions they have.
- Permission usage analytics: Multi-dimensional view of permissions risk for all identities, actions, and resources.
Remediate
Customers can right-size permissions based on usage, grant new permissions on-demand, and automate just-in-time access for cloud resources.
- Automated deletion of permissions unused for the past 90 days.
- Permissions on-demand: Grant identities permissions on-demand for a time-limited period or an as-needed basis.
Monitor
Customers can detect anomalous activities with machine learning-powered (ML-powered) alerts and generate detailed forensic reports.
- ML-powered anomaly detections.
- Context-rich forensic reports around identities, actions, and resources to support rapid investigation and remediation.
Permissions Management deepens Zero Trust security strategies by augmenting the least privilege access principle, allowing customers to:
- Get comprehensive visibility: Discover which identity is doing what, where, and when.
- Automate least privilege access: Use access analytics to ensure identities have the right permissions, at the right time.
- Unify access policies across infrastructure as a service (IaaS) platforms: Implement consistent security policies across your cloud infrastructure.
Once your organization has explored and implemented the discover, remediation and monitor phases, you’ve established one of the core pillars of a modern zero-trust security strategy.
Permissions Management vs. Privileged Identity Management (PIM)
Permissions Management complements Microsoft Entra PIM. Microsoft Entra PIM provides just-in-time access for admin roles in Azure and Microsoft Online Services and apps that use groups. Permissions Management allows multicloud discovery, remediation, and monitoring of privileged access across Azure, AWS, and GCP.
Onboarding Permissions Management
Customers with Global Administrator role have first to onboard Permissions Management on their Microsoft Entra tenant, and then onboard their AWS accounts, GCP projects, and Azure subscriptions.
Once fully onboarded with data collection setup, customers can access permissions usage insights within hours. Our machine-learning engine refreshes the Permission Creep Index every hour so that customers can start their risk assessment right away.
In order to enable Entra Permissions Management in your organization and Azure tenant, you can either sign up for a 45-day free trial as I will use for this post or by using volume licensing. More details you will find in the following article from Microsoft https://learn.microsoft.com/en-us/azure/active-directory/cloud-infrastructure-entitlement-management/onboard-enable-tenant.
Open the Permissions Management portal by using the Launch portal button below.
Permissions Management launches with the Data Collectors dashboard. As you can see from the URI, this CIEM solution actually belongs to CloudKnox which Microsoft acquired in July 2021.
Microsoft acquires CloudKnox Security to offer unified privileged access and cloud entitlement management.
https://blogs.microsoft.com/blog/2021/07/21/microsoft-acquires-cloudknox-security-to-offer-unified-privileged-access-and-cloud-entitlement-management/
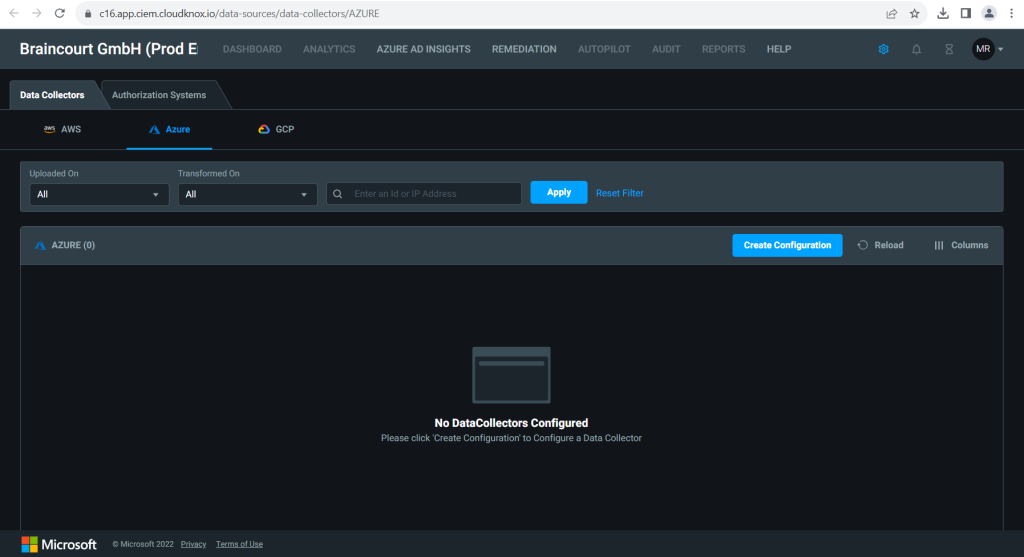
For information on how to onboard an AWS account, Azure subscription, or GCP project into Permissions Management, select one of the following articles and follow the instructions:
Onboard a Microsoft Azure subscription
To demonstrate Permissions Management I will just onboard here my Azure subscriptions.
Onboarding a subscription creates a new authorization system to represent the Azure subscription in Permissions Management.
The Permissions Management service is built on Azure, and given you’re onboarding your Azure subscriptions to be monitored and managed, setup is simple with few moving parts to configure. Below is what is required to configure onboarding:
- When your tenant is onboarded, an application is created in the tenant.
- This app requires ‘reader’ permissions on the subscriptions
- For controller functionality, the app requires ‘User Access Administrator’ to create and implement right-size roles
On the Data Collectors dashboard, select Azure, and then select Create Configuration.
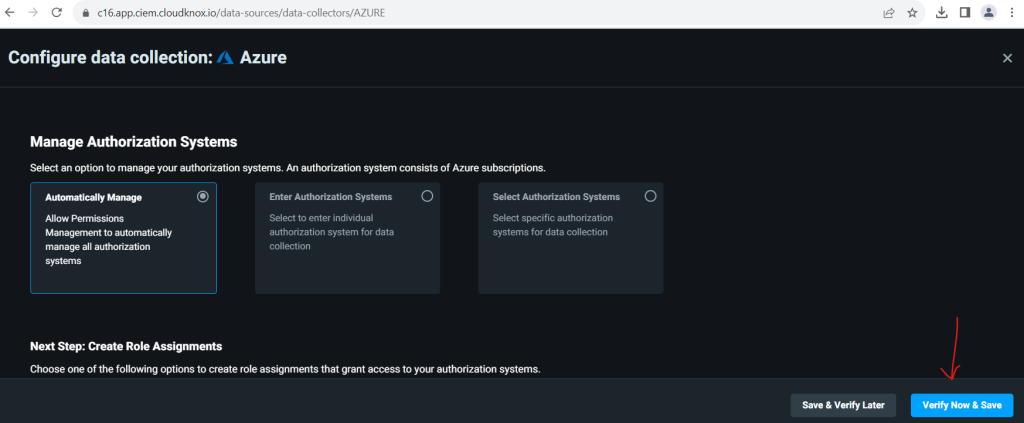
Choose from three options to manage Azure subscriptions.
I will choose here the first option Automatically Manage.
This option lets subscriptions be automatically detected and monitored without further work required. A key benefit of automatic management is that any current or future subscriptions found are onboarded automatically.
More about the options you will find here https://learn.microsoft.com/en-us/azure/active-directory/cloud-infrastructure-entitlement-management/onboard-azure#1-add-azure-subscription-details
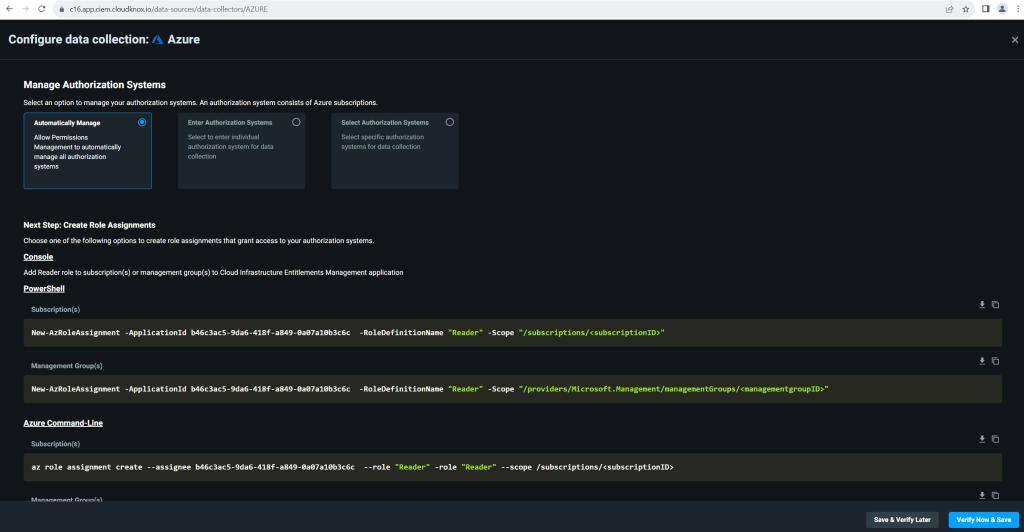
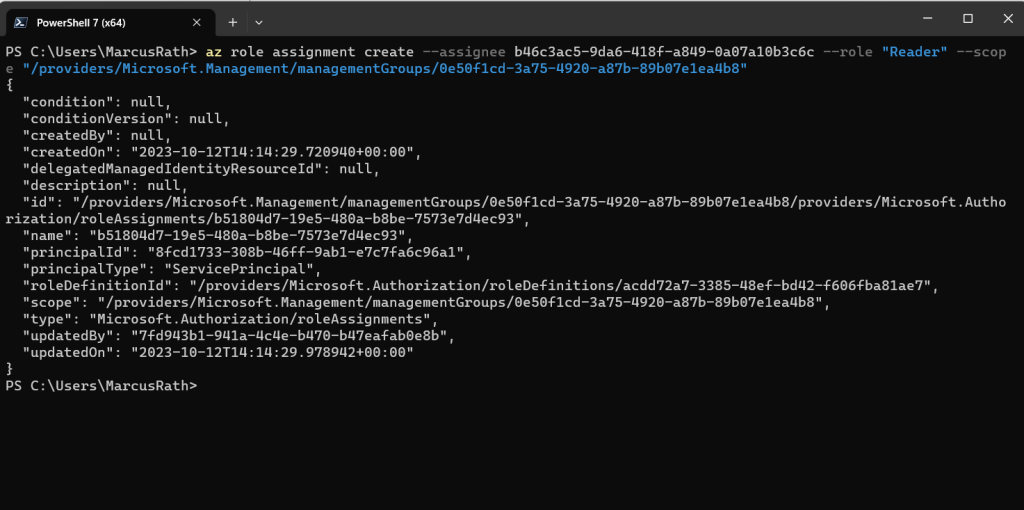
The steps listed on the screen outline how to create the role assignment for the Cloud Infrastructure Entitlements Management application. This is performed manually in the Microsoft Entra ID console, or programmatically with PowerShell or the Azure CLI.
I will grant the reader role to the Cloud Infrastructure Entitlement Management application to the management group where my subscriptions are assigned to.
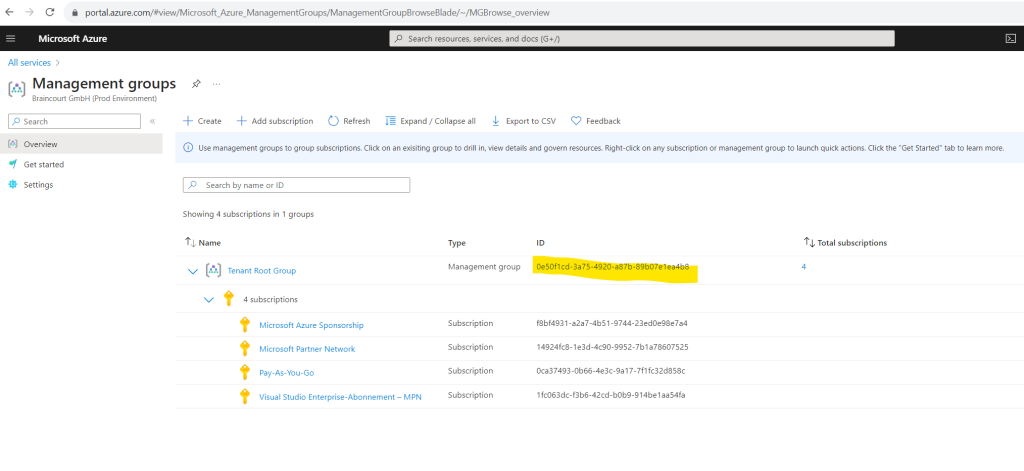
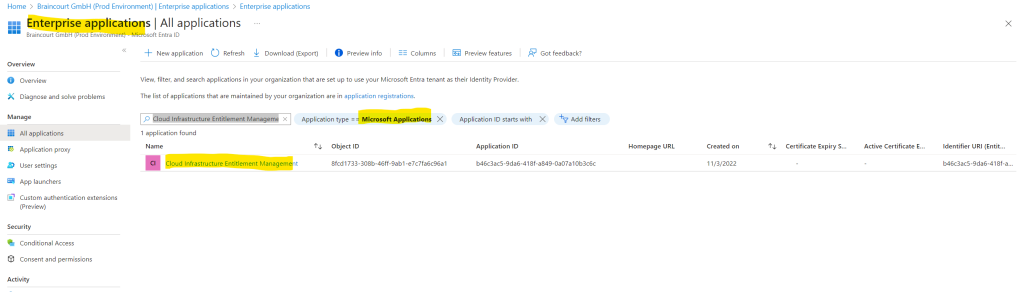
You will find this app in the Enterprise applications blade from Microsoft Entra ID (formerly Azure ID). Filter for Microsoft Applications and paste the app name Cloud Infrastructure Entitlement Management into the find box.
Then click on Verify Now & Save
To view status of onboarding after saving the configuration:
- Collectors are now listed and change through status types. For each collector listed with a status of Collected Inventory, click on that status to view further information.
- You can then view subscriptions on the In Progress page.
The status column in your Permissions Management UI shows you which step of data collection you’re at:
- Pending: Permissions Management has not started detecting or onboarding yet.
- Discovering: Permissions Management is detecting the authorization systems.
- In progress: Permissions Management has finished detecting the authorization systems and is onboarding.
- Onboarded: Data collection is complete, and all detected authorization systems are onboarded to Permissions Management.
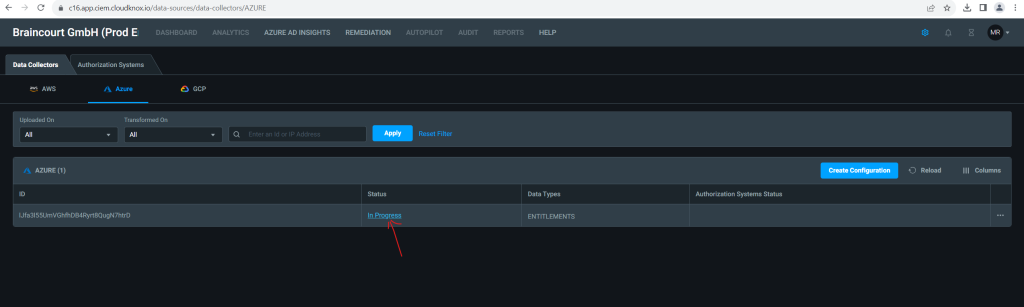
Subscriptions Onboarding
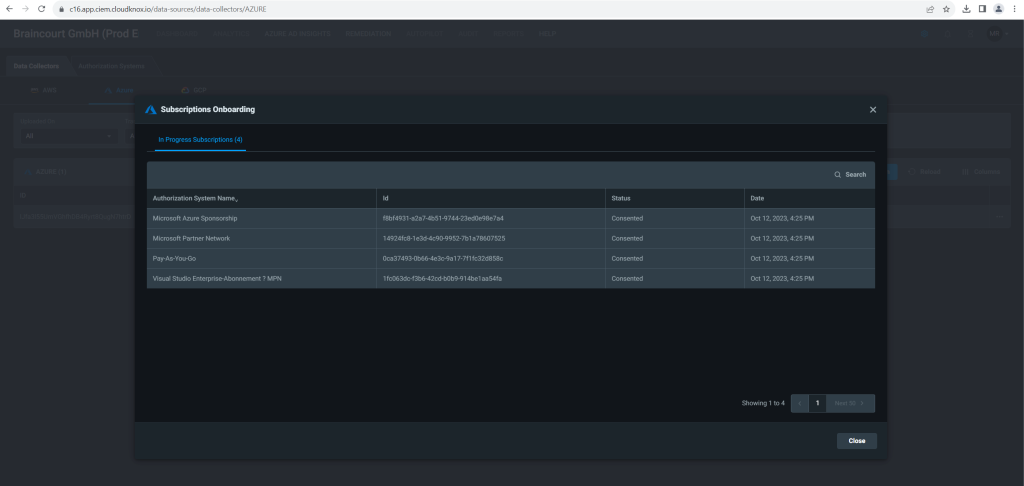
As mentioned Onboarding a subscription creates a new authorization system to represent the Azure subscription in Permissions Management.
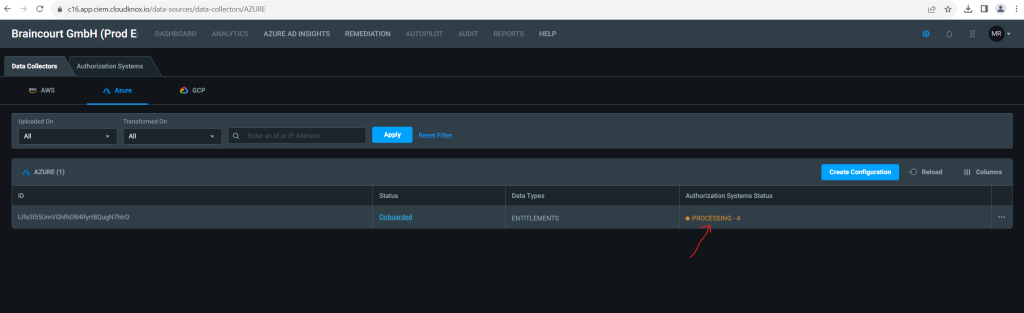
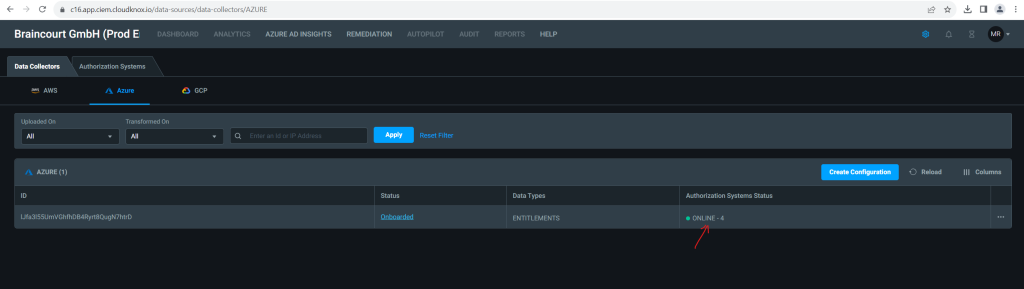
To view the data, click above on the Online link or select the Authorization Systems tab.
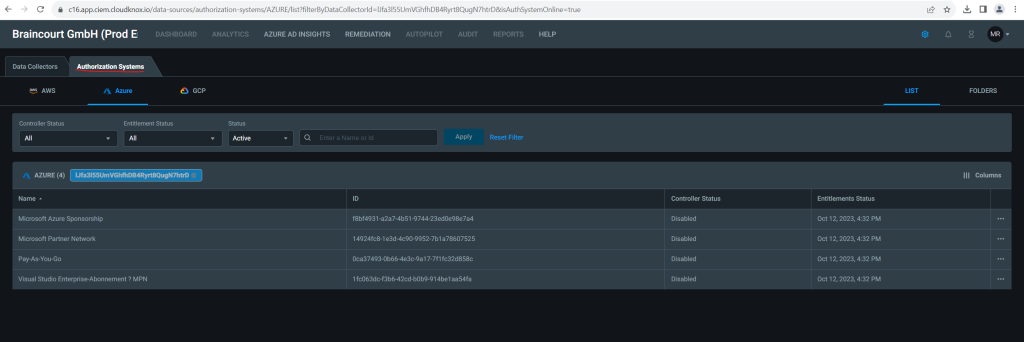
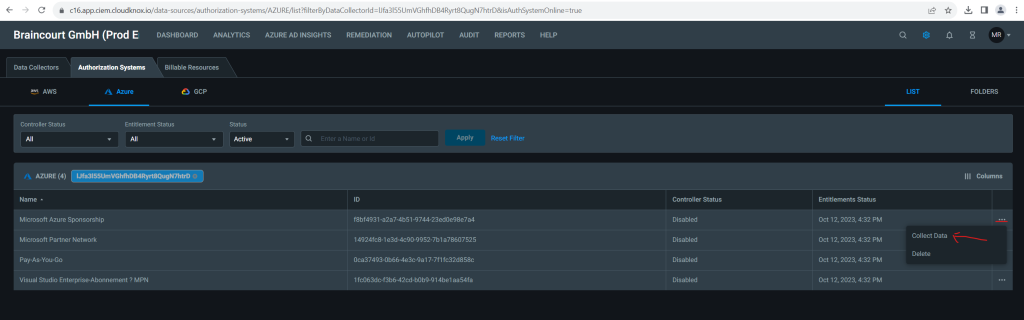
View key statistics and data about your authorization system
Permissions Management provides a summary of key statistics and data about your authorization system regularly. This information is available for Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
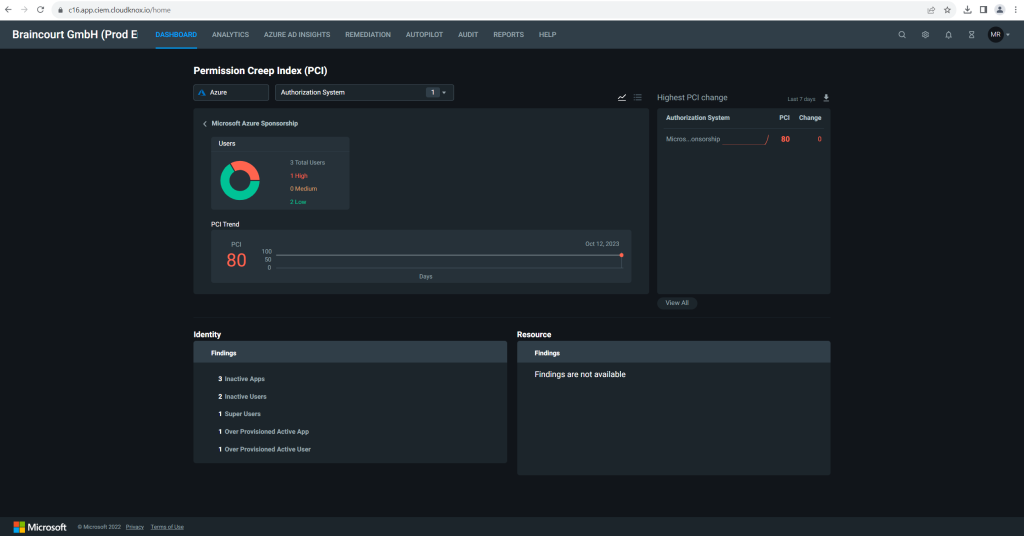
The data provided by Permissions Management includes metrics related to avoidable risk. These metrics allow the Permissions Management administrator to identify areas where they can reduce risks related to the principle of least permissions.
You can view the following information in Microsoft Entra:
- The Permission Creep Index (PCI) heat map on the Permissions Management Dashboard identifies:
- The number of users who have been granted high-risk permissions but aren’t using them.
- The number of users who contribute to the permission creep index (PCI) and where they are on the scale.
- The Analytics dashboard provides a snapshot of permission metrics within the last 90 days.
More you will find in the following article from Microsoft https://learn.microsoft.com/en-us/azure/active-directory/cloud-infrastructure-entitlement-management/ui-dashboard
What is Microsoft Entra?
To see all products included in the unifying brand named Microsoft Entra please take a look at my following post.
Links
Permissions Management
https://learn.microsoft.com/en-us/azure/active-directory/cloud-infrastructure-entitlement-management/



