How to enroll already Microsoft Entra joined (former Azure AD joined) Devices to Microsoft Intune?
Devices that are already Microsoft Entra joined (former Azure AD joined), before you have enabled MDM auto-enrollment in your tenant, will unfortunately after enabling MDM auto-enrollment not enroll automatically in Microsoft Intune.
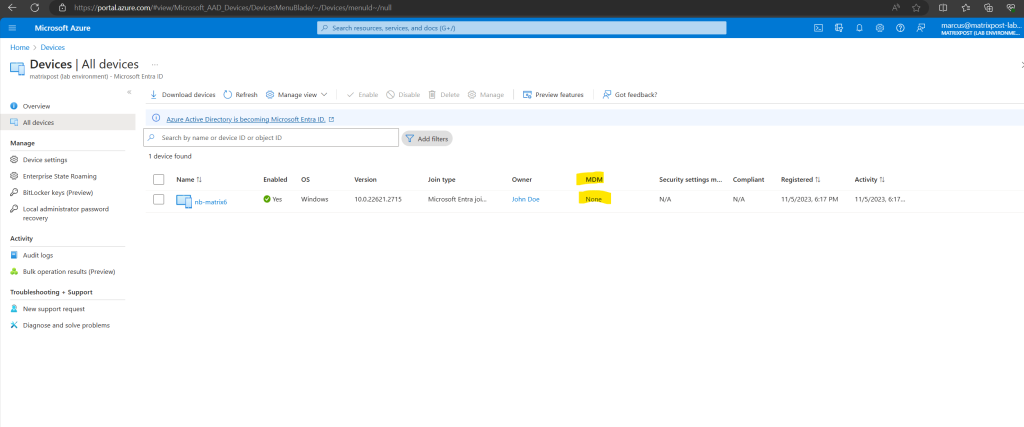
When you enable MDM auto-enrollment like shown below and now a user with an eligible license for Microsoft Intune like Enterprise Mobility + Security E3 will join its device to Microsoft Entra ID, the device will automatically enroll in Microsoft Intune.
Use MDM auto-enrollment to manage enterprise data on your employees’ Windows devices. MDM auto-enrollment will be configured for Microsoft Entra joined devices and bring your own device scenarios.
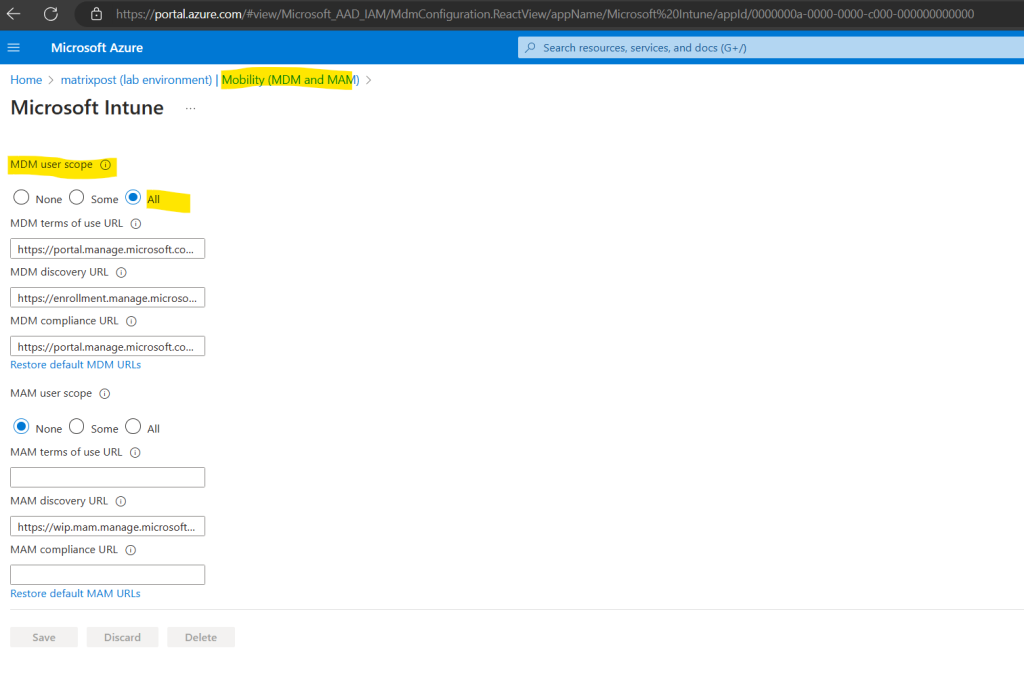
As mentioned in case you will enable MDM auto-enrollment after you have already joined some devices to Microsoft Entra ID, these devices will unfortunately not triggered by default to enroll automatically to Microsoft Intune.
There is a post about how you can nevertheless enroll these already Microsoft Entra joined devices to Microsoft Intune by firing up a little PowerShell script on these devices which leverages the C:Windows\system32\deviceenroller.exe. Below I will refer to this post.
We first need to allow the script can be executed on the affected devices by adjusting the execution policy.
about_Execution_Policies
https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_execution_policies?view=powershell-7.3
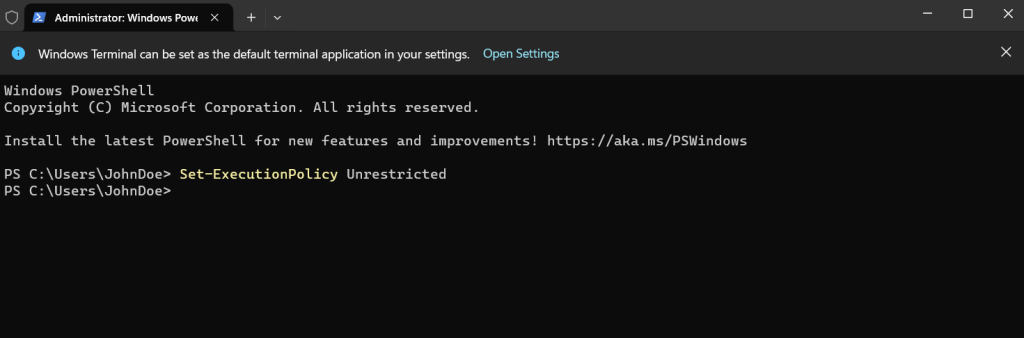
The script itself needs to be executed with system context, therefore we can fortunately use the PsExec tools from the Sysinternals suite.
More about Sysinternals and its PsExec tool you can find in my following post https://blog.matrixpost.net/sysinternals-and-its-psexec-tool/.
Copy the following PowerShell script to the affected device. I was saving the script for example as AutoEnrollMDM.ps1 to the device I wanted to enroll to Microsoft Intune.
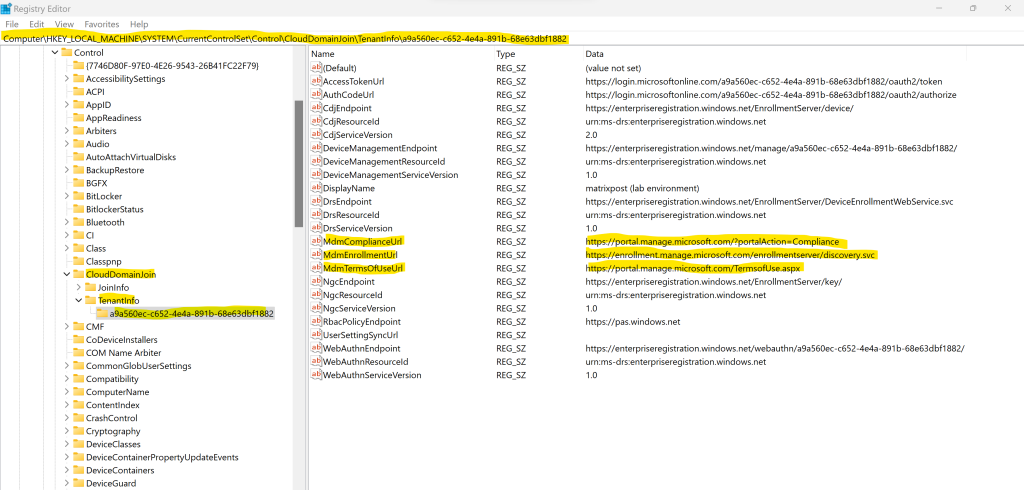
The script is first checking if the Microsoft Entra joined registry settings including the Tenant ID and MDM Enrollment URL is already set for the affected device. These registry settings should be set when joining the device to Microsoft Entra ID (former Azure AD). If not already set, the script will try to set the MDM Enrollment URL in the registry which is then later used by the C:Windowssystem32deviceenroller.exe in order to enroll the device in Microsoft Intune.
# Set MDM Enrollment URL's
$key = 'SYSTEMCurrentControlSetControlCloudDomainJoinTenantInfo*'
try{
$keyinfo = Get-Item "HKLM:$key"
}
catch{
Write-Host "Tenant ID is not found!"
exit 1001
}
$url = $keyinfo.name
$url = $url.Split("")[-1]
$path = "HKLM:SYSTEMCurrentControlSetControlCloudDomainJoinTenantInfo$url"
if(!(Test-Path $path)){
Write-Host "KEY $path not found!"
exit 1001
}else{
try{
Get-ItemProperty $path -Name MdmEnrollmentUrl
}
catch{
Write_Host "MDM Enrollment registry keys not found. Registering now..."
New-ItemProperty -LiteralPath $path -Name 'MdmEnrollmentUrl' -Value 'https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc' -PropertyType String -Force -ea SilentlyContinue;
New-ItemProperty -LiteralPath $path -Name 'MdmTermsOfUseUrl' -Value 'https://portal.manage.microsoft.com/TermsofUse.aspx' -PropertyType String -Force -ea SilentlyContinue;
New-ItemProperty -LiteralPath $path -Name 'MdmComplianceUrl' -Value 'https://portal.manage.microsoft.com/?portalAction=Compliance' -PropertyType String -Force -ea SilentlyContinue;
}
finally{
# Trigger AutoEnroll with the deviceenroller
try{
C:Windowssystem32deviceenroller.exe /c /AutoEnrollMDM
Write-Host "Device is ready for Autopilot enrollment now!"
exit 0
}
catch{
Write-Host "Something went wrong (C:Windowssystem32deviceenroller.exe)"
exit 1001
}
}
}
exit 0Working with registry entries
https://learn.microsoft.com/en-us/powershell/scripting/samples/working-with-registry-entries
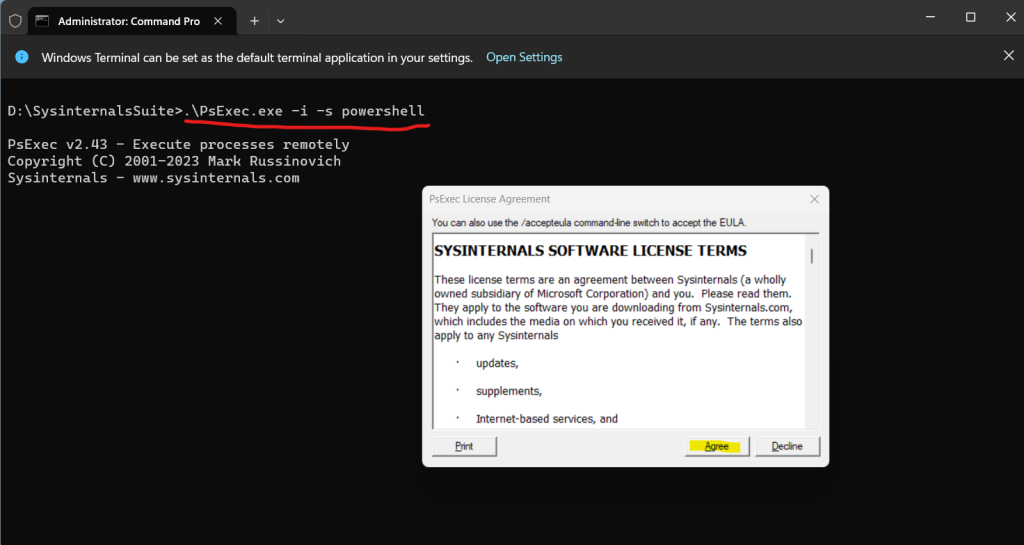
In order to start a new PowerShell session which runs under the system account we can now use the PsExec tool like shown below.
> PsExec.exe -i -s powershell
Source: https://learn.microsoft.com/en-us/sysinternals/downloads/psexec#using-psexec
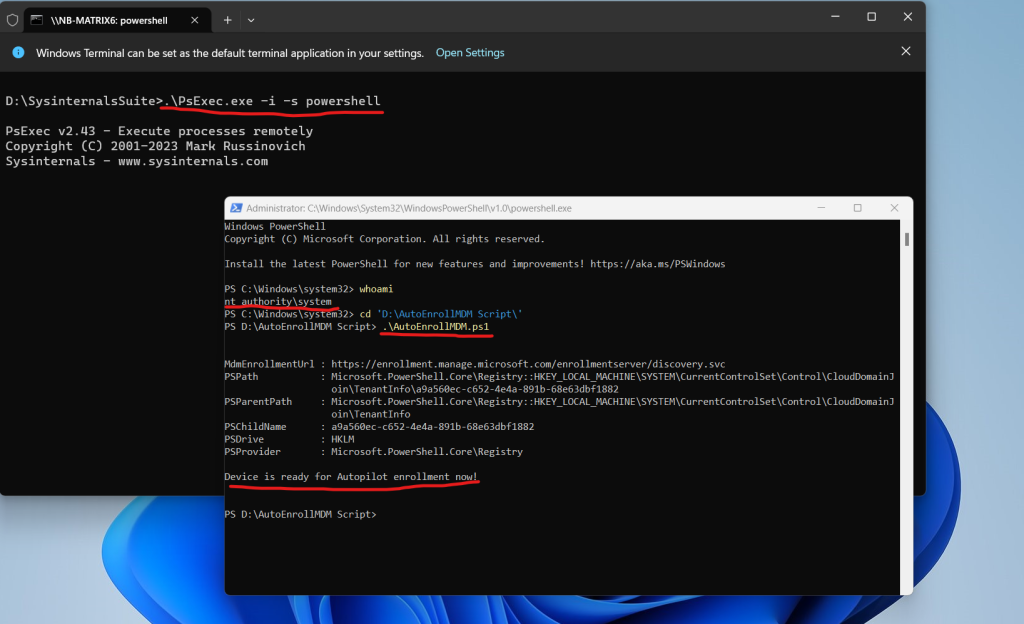
By using the whoami command you can check if the process is really running under the system account. Finally we can run the script to auto-enroll the device to Microsoft Intune.
In case you are also interested in Windows Autopilot, you can read my following post https://blog.matrixpost.net/set-up-windows-autopilot/.
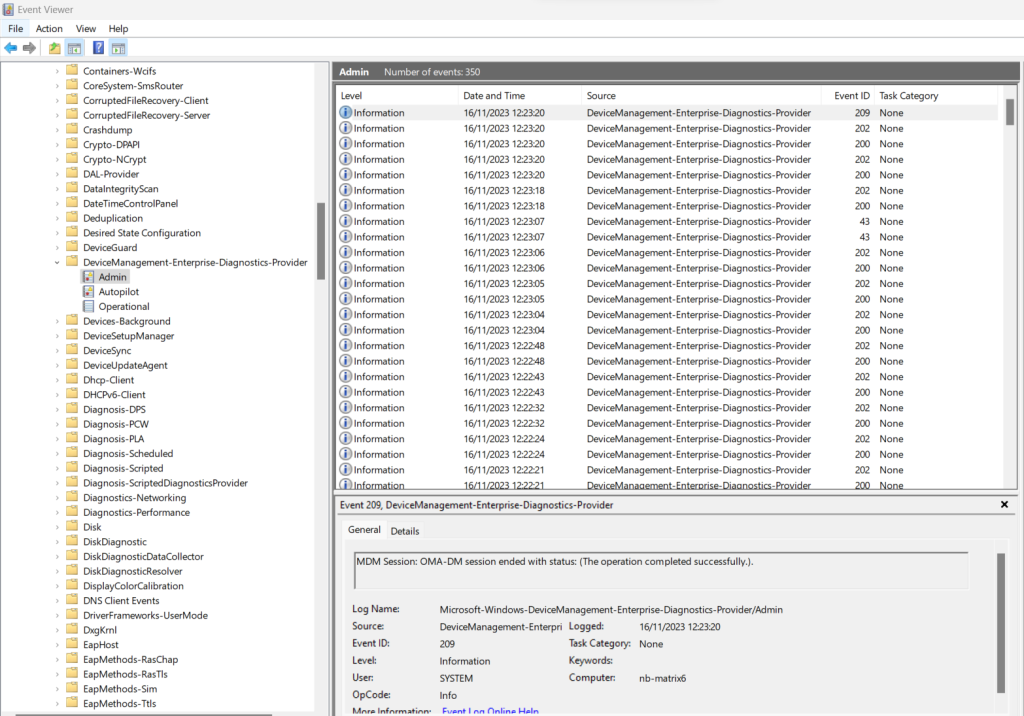
In case something went wrong you can also analyze the corresponding logs under Event Viewer -> Applications and Services Logs -> Microsoft -> Windows -> DeviceManagement-Enterprise-Diagnostics-Provider.
In my case I was first getting an error regarding device credentials, but after running the script a second time, the device enrolled immediately in Microsoft Intune.
So if the device after running the script is not immediately shown up in Microsoft Intune, try to run the script a second time.
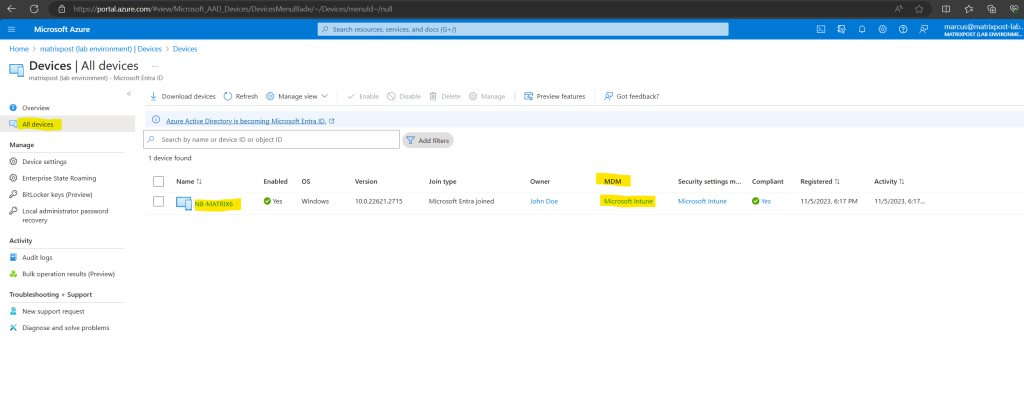
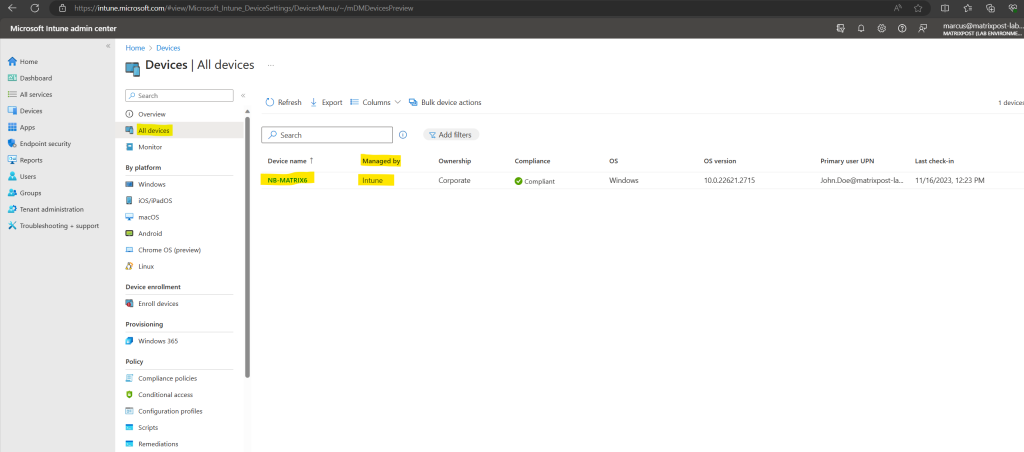
The device is shown up in Microsoft Intune immediately after running the script.
Links
Microsoft Intune securely manages identities, manages apps, and manages devices
https://learn.microsoft.com/en-us/mem/intune/fundamentals/what-is-intuneManage your devices and control device features in Microsoft Intune
https://learn.microsoft.com/en-us/mem/intune/fundamentals/manage-devicesDeployment guide: Setup or move to Microsoft Intune
https://learn.microsoft.com/en-us/mem/intune/fundamentals/deployment-guide-intune-setupDeployment guidance: Enroll devices in Microsoft Intune
https://learn.microsoft.com/en-us/mem/intune/fundamentals/deployment-guide-enrollment
Related Posts
Follow me on LinkedIn


